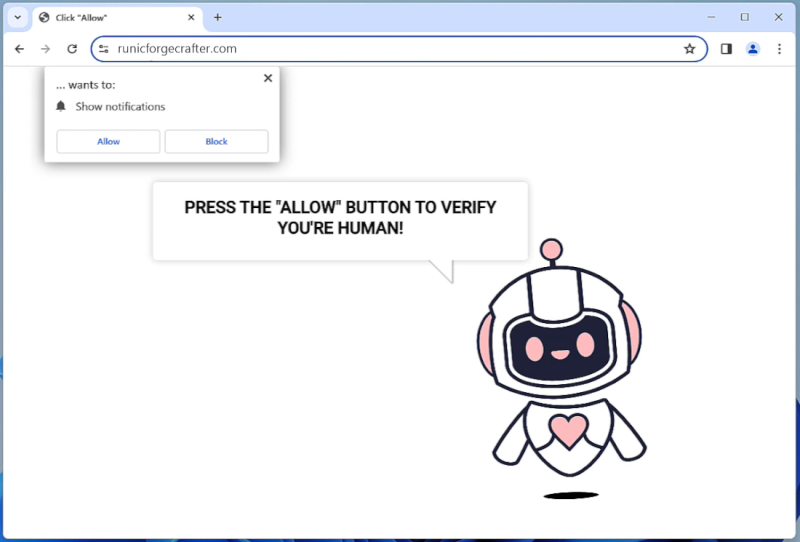
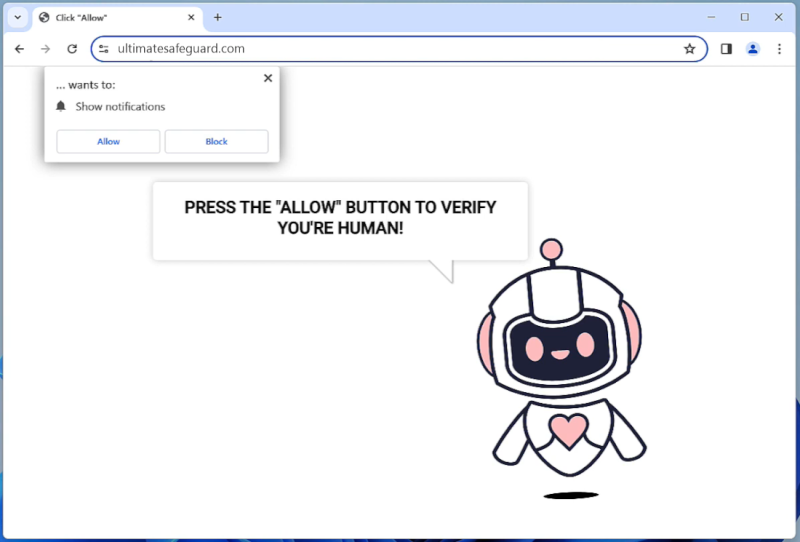
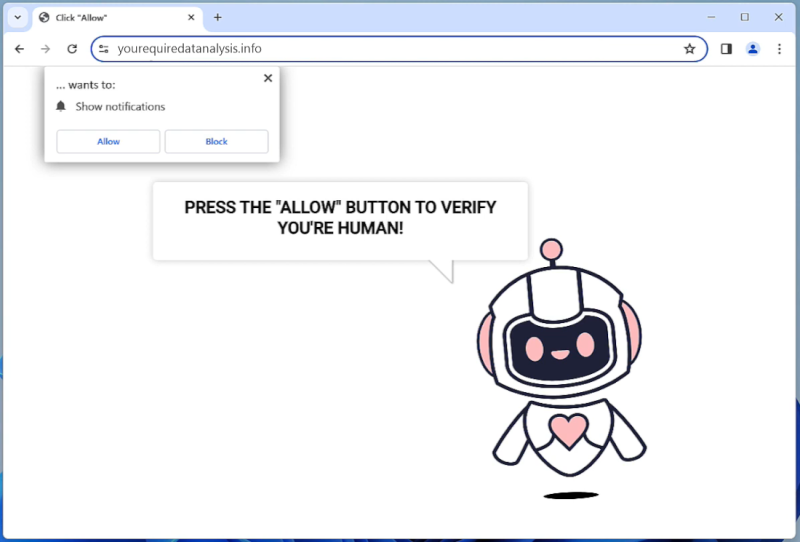
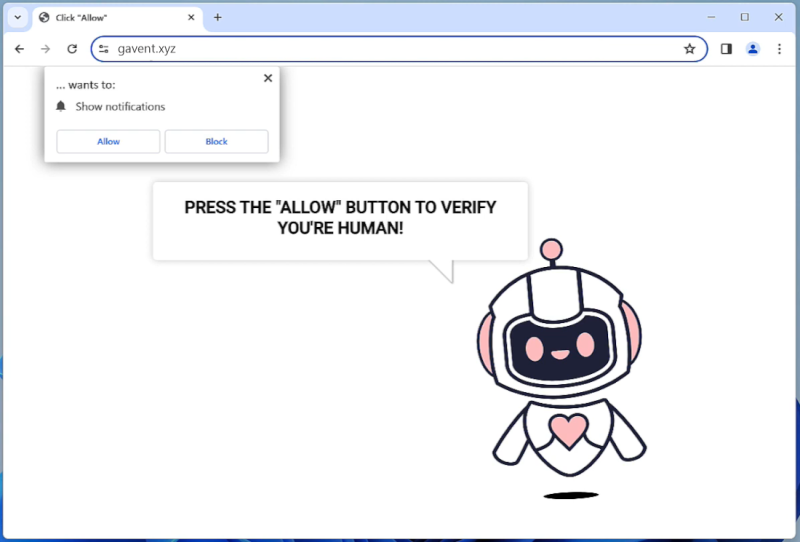
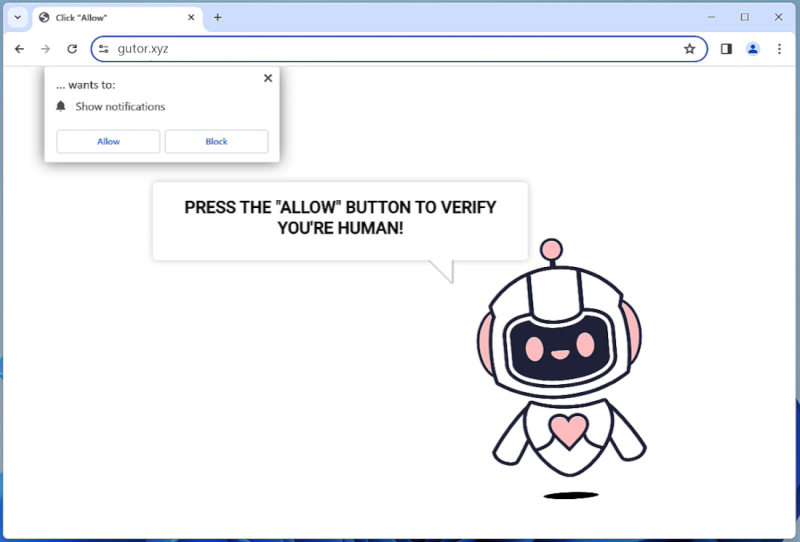
Runicforgecrafter.com is a malicious website that infects computers by tricking users into allowing browser notifications. When a user visits the website, they are prompted with a message asking to enable notifications in order to access the content. Once the notifications are enabled, the website starts displaying unwanted pop-up notifications on the user’s browser, even when they are not visiting the website.
This form of malware exploits browser notifications to bombard users with unwanted advertisements, fraudulent messages, and potentially harmful links. Runicforgecrafter.com can infect various browsers such as Google Chrome, Mozilla Firefox, and Safari, across different devices including desktop computers, laptops, and mobile devices. Users should be cautious when visiting unfamiliar websites and avoid enabling notifications from suspicious sources to prevent falling victim to this type of malware.