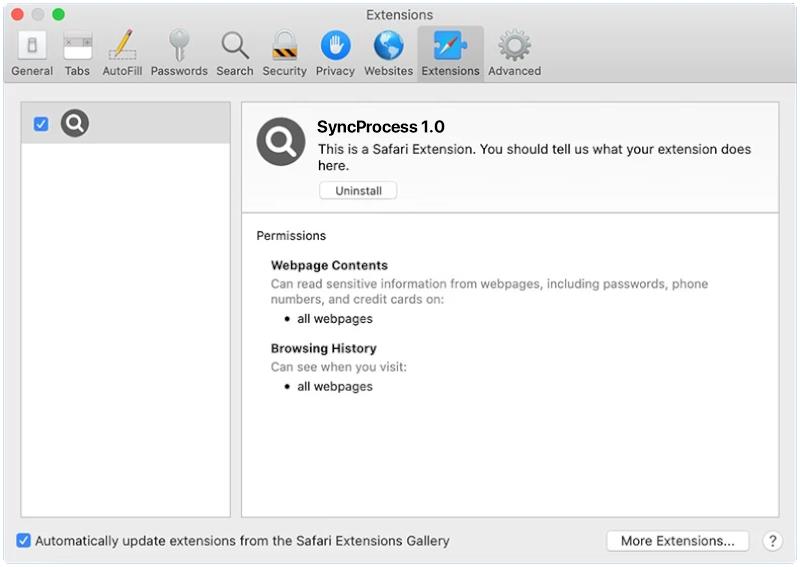
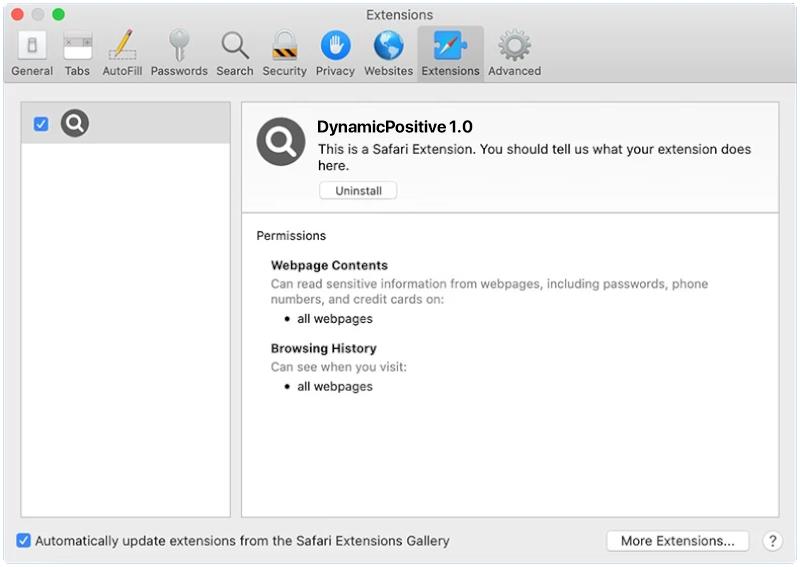
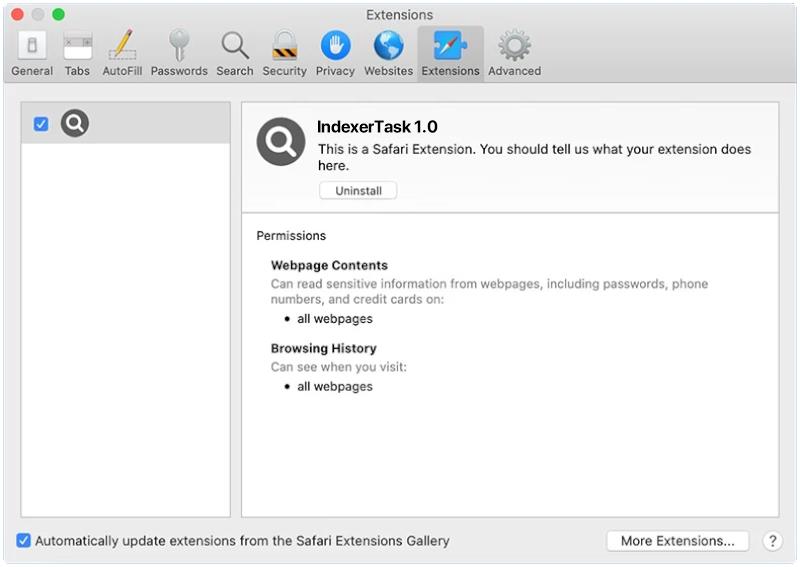
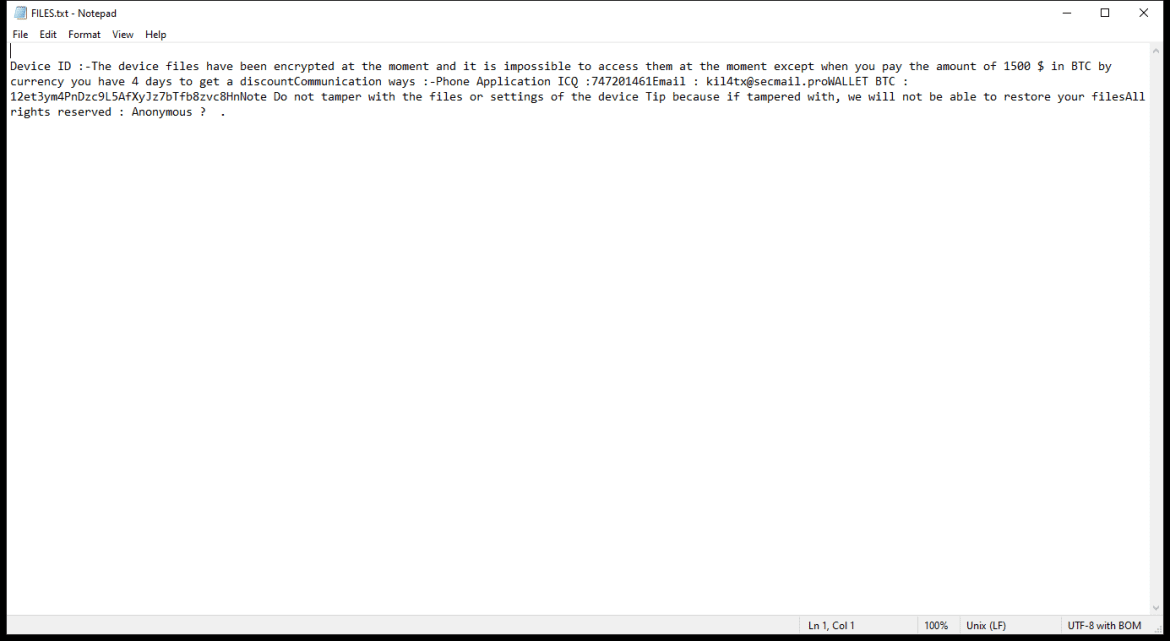
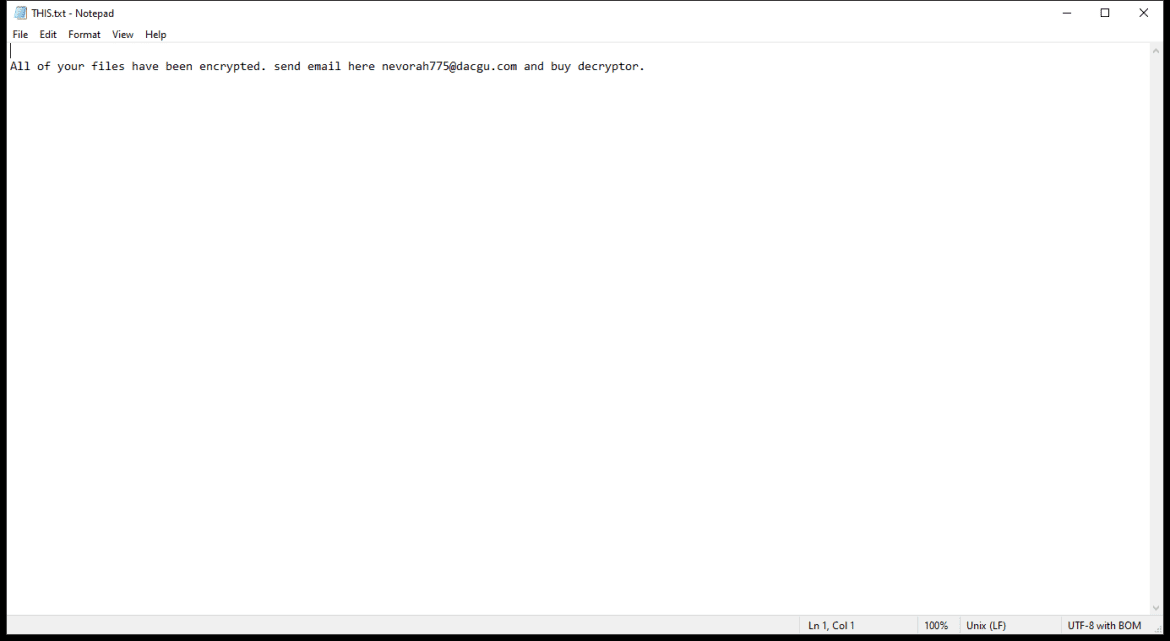
Pws:Win32/Zbot.Fd!Mtb is a type of malware known as a password stealer. It is designed to steal sensitive information such as usernames, passwords, and other personal data from infected computers.
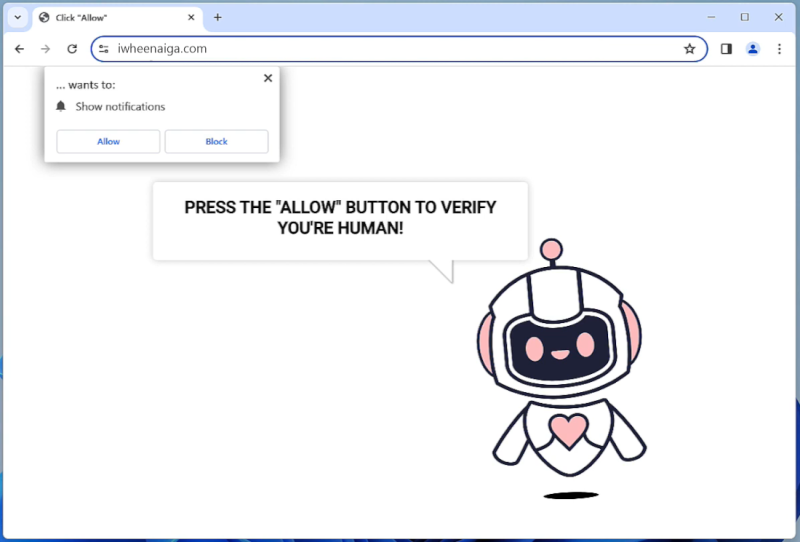
Pws:Win32/Zbot.Fd!Mtb typically infects computers through various methods such as phishing emails, malicious websites, software vulnerabilities, or through the use of infected USB drives. Once the malware infects a computer, it can remain hidden and silently collect data without the user’s knowledge.
To protect against Pws:Win32/Zbot.Fd!Mtb and other malware, it is important to regularly update your operating system and software, use strong and unique passwords, avoid clicking on suspicious links or downloading attachments from unknown sources, and use reputable antivirus software to scan and remove any potential threats.