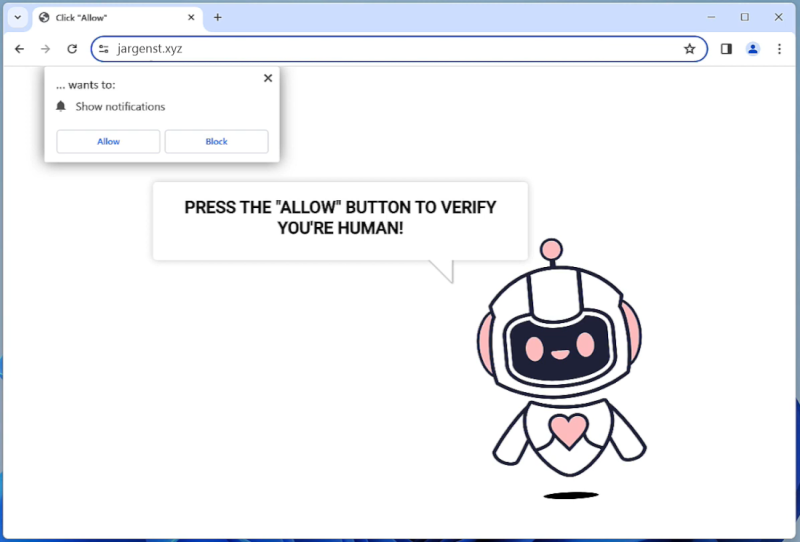
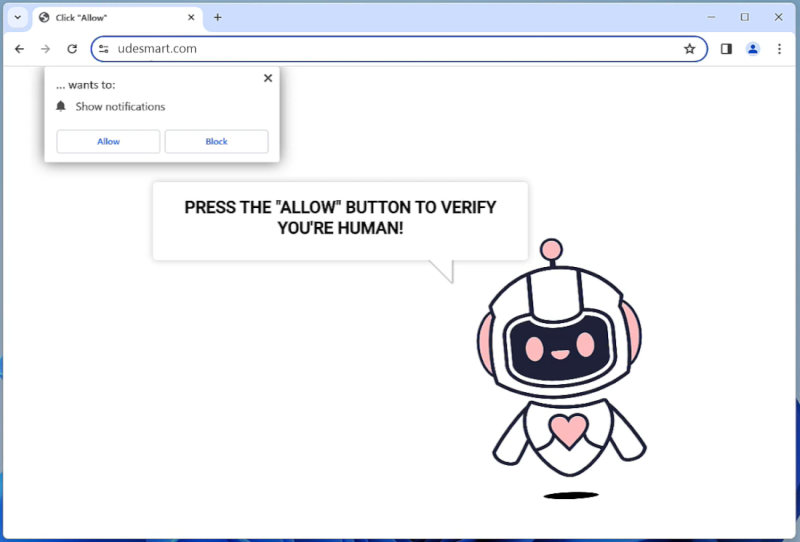
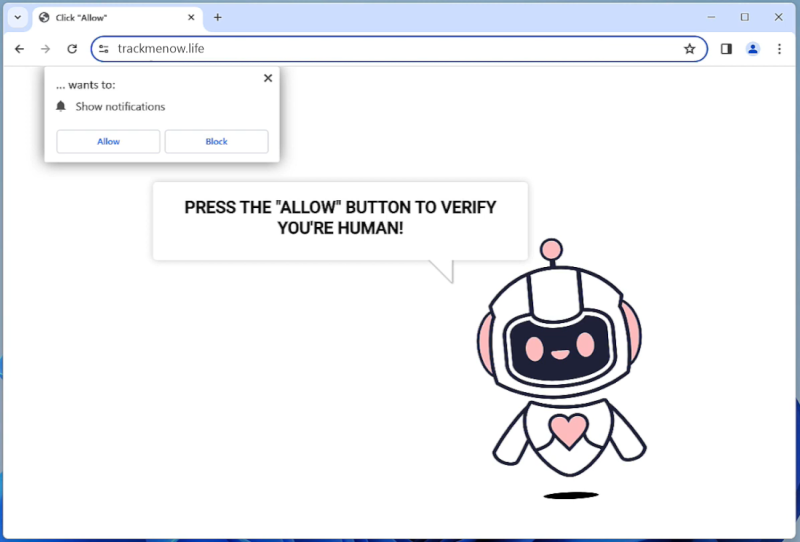
Jargenst.xyz is a malicious website that infects computers by tricking users into allowing browser notifications. It typically spreads through deceptive pop-up ads or malicious links that prompt users to click on them, which then leads to a prompt asking for permission to show notifications from the website. If the user agrees, Jargenst.xyz starts bombarding them with unwanted notifications, which can contain links to other malicious websites or scams.
Once a user grants permission for notifications from Jargenst.xyz, the website can exploit this feature to display notifications even when the browser is closed. This can be particularly annoying and disruptive for users, as the notifications can appear on the desktop or lock screen of their device. Jargenst.xyz primarily targets popular web browsers such as Google Chrome, Mozilla Firefox, and Microsoft Edge, and can infect both desktop and mobile devices. Users are advised to be cautious when encountering suspicious pop-ups or prompts asking for notification permissions to avoid falling victim to such malware infections.