Ldhy Ransomware is a type of malicious software that encrypts files on a victim’s computer and demands a ransom payment in order to restore access to the encrypted files. Here is some information about Ldhy Ransomware:
1. Infection: Ldhy Ransomware typically infects computers through various methods, including email attachments, malicious downloads, fake software updates, or exploit kits.
2. File Extensions: Ldhy Ransomware adds the “.ldhy” extension to the encrypted files. For example, a file named “document.doc” will be renamed to “document.doc.ldhy” after encryption.
3. File Encryption: Ldhy Ransomware uses strong encryption algorithms such as AES or RSA to encrypt the victim’s files. This encryption renders the files inaccessible without the decryption key.
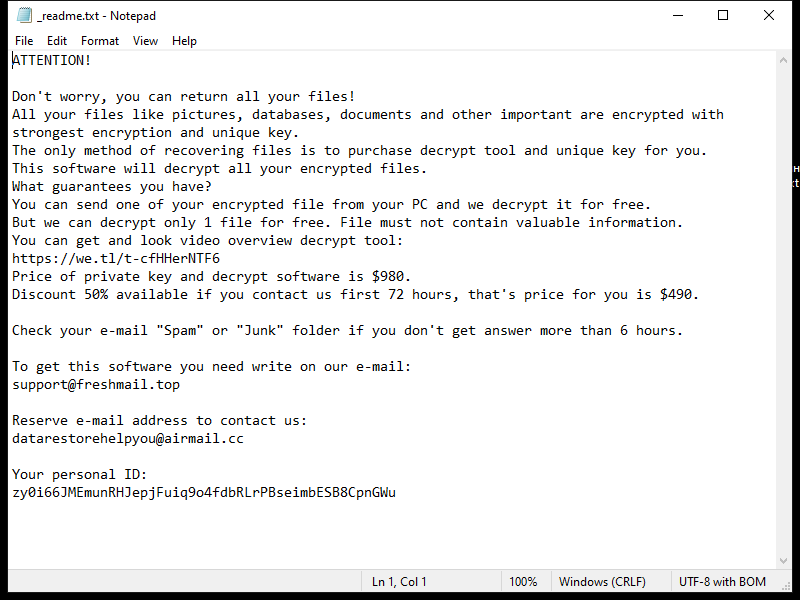
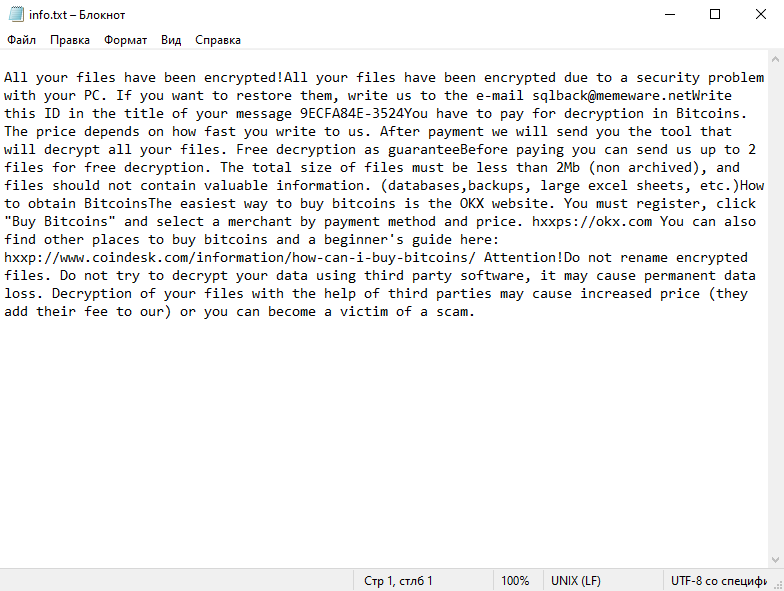
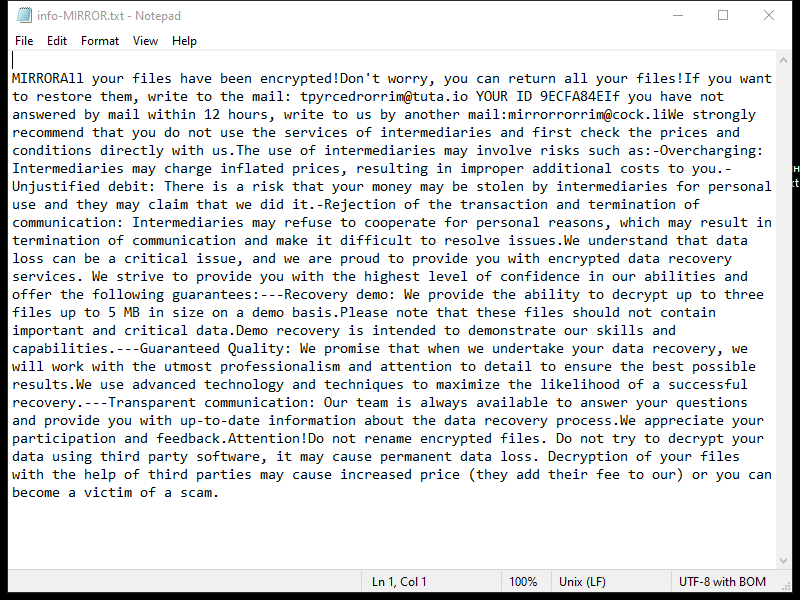
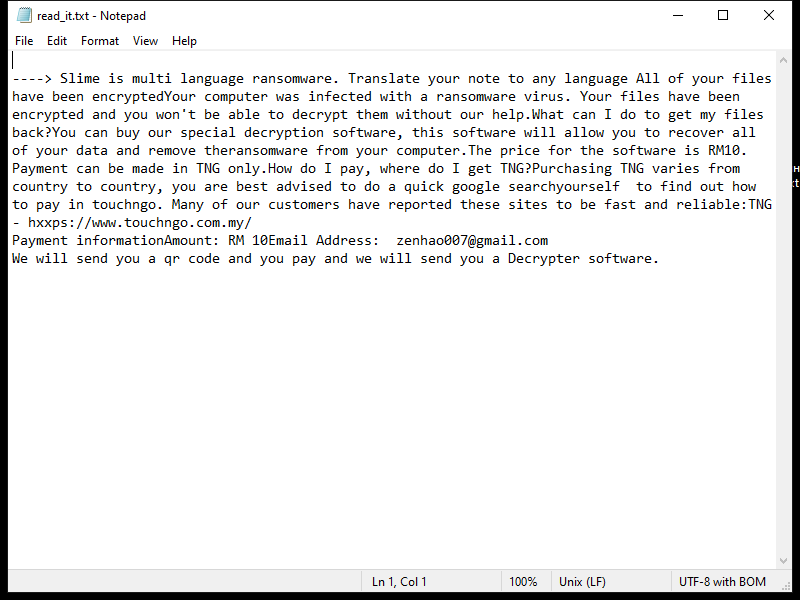
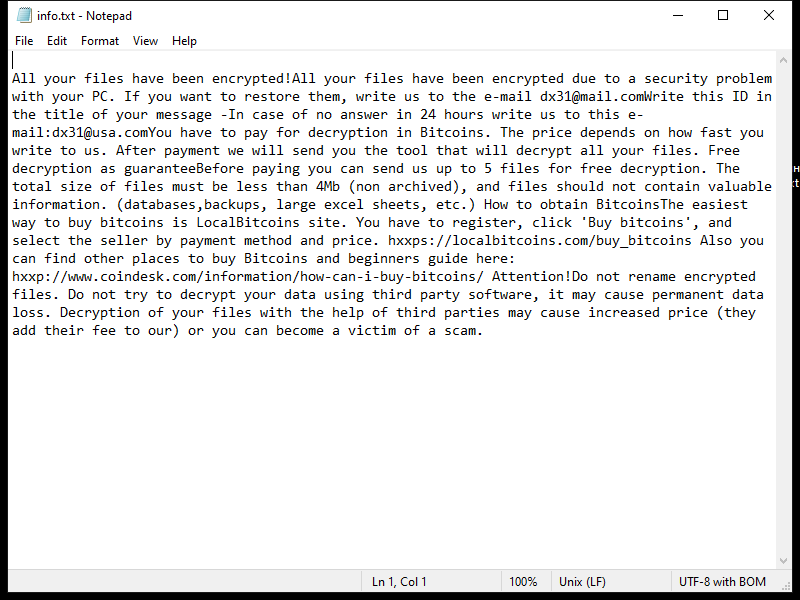
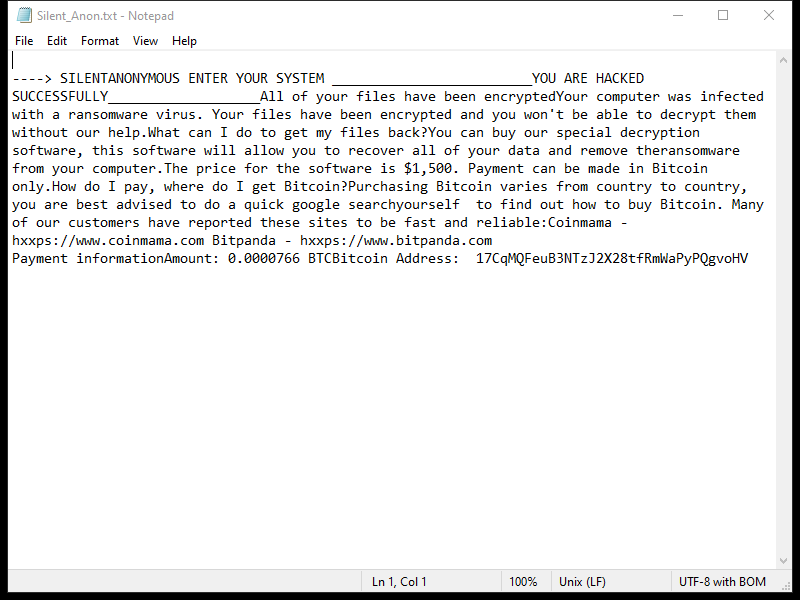
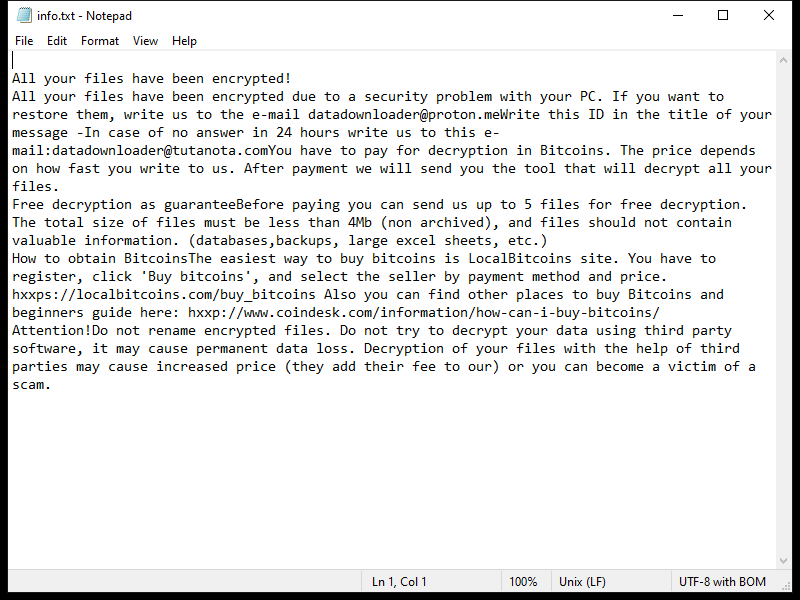
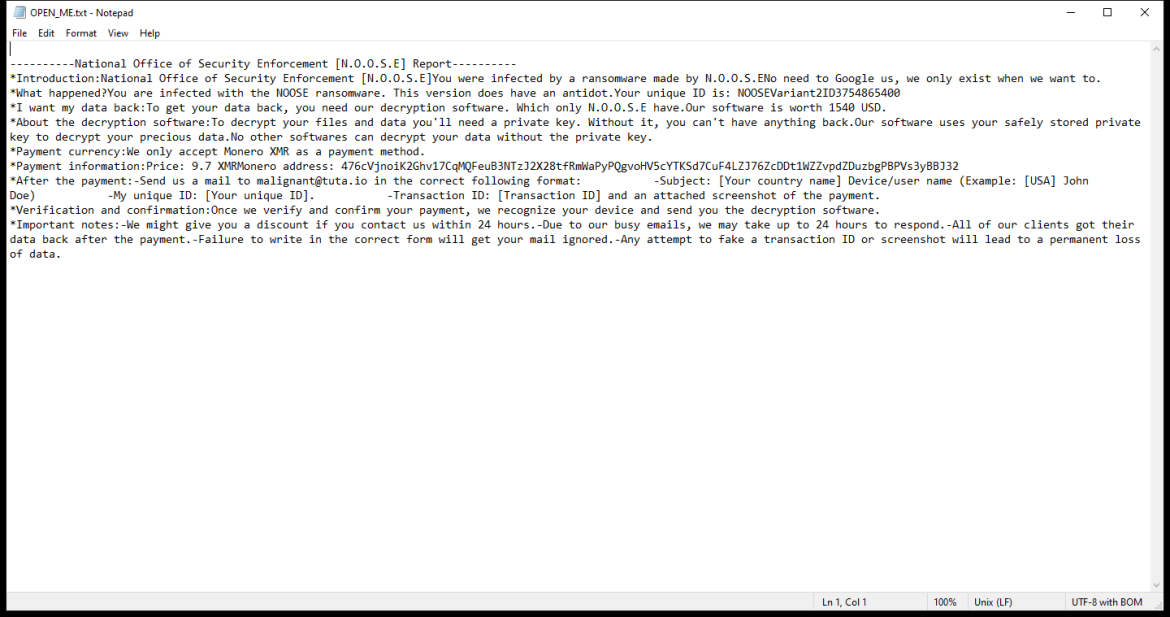
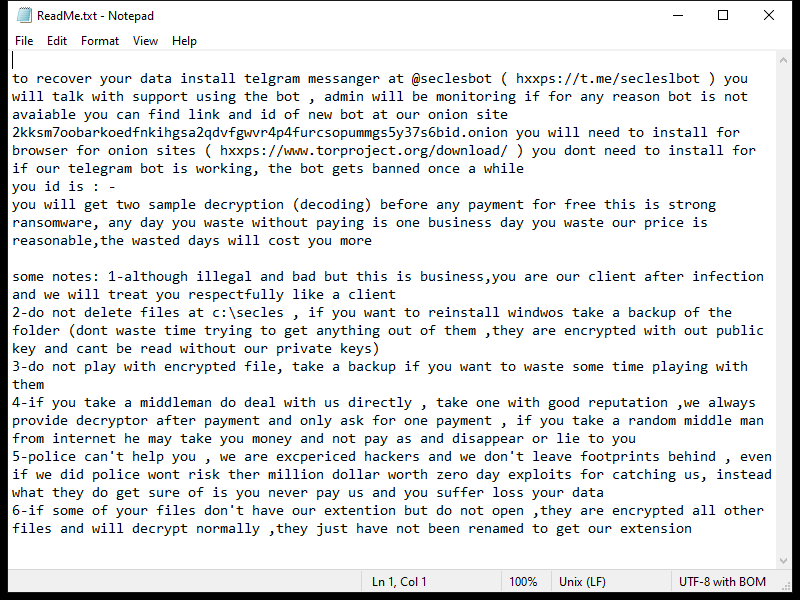
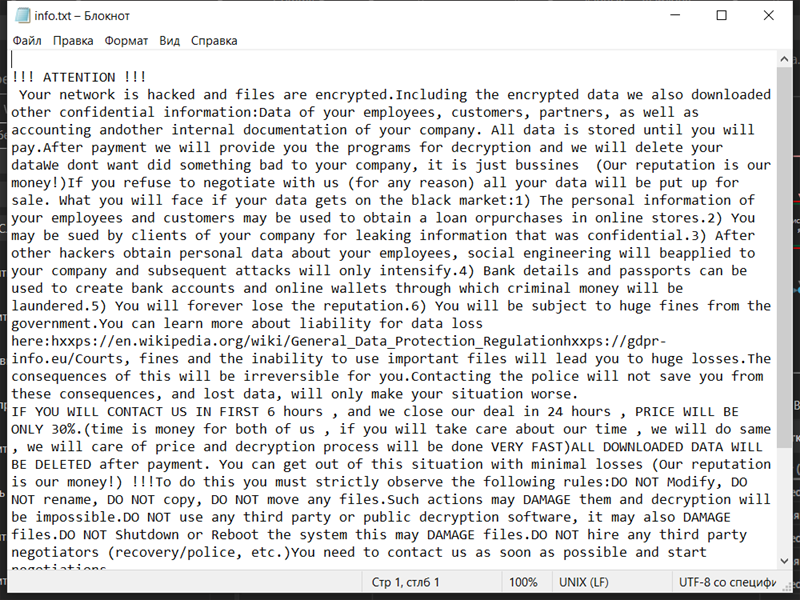
4. Ransom Note: Ldhy Ransomware creates a ransom note, usually in the form of a text file or a pop-up message, which provides instructions on how to pay the ransom and obtain the decryption key. The ransom note is typically placed on the desktop or in folders containing encrypted files.
5. Decryption Tools: As of now, there is no publicly available decryption tool specifically designed for Ldhy Ransomware. However, security companies like Emsisoft continue to develop decryption tools for various ransomware strains, including the Stop Djvu ransomware family, which Ldhy Ransomware belongs to.
6. Emsisoft Stop Djvu Decryptor: Emsisoft has developed the Stop Djvu Decryptor tool, which can decrypt files encrypted by some variants of the Djvu ransomware family. However, it may not be able to decrypt files affected by the latest variants, including Ldhy Ransomware. It is recommended to regularly check Emsisoft’s website for updates on available decryption tools.
Please note that paying the ransom does not guarantee that you will receive the decryption key, and it supports the criminal activities of ransomware operators. It is important to regularly back up your files and implement robust security measures to prevent ransomware infections.