How to remove Pcdsecuresupdates.live
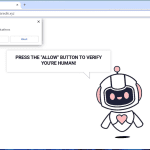
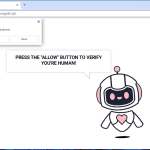
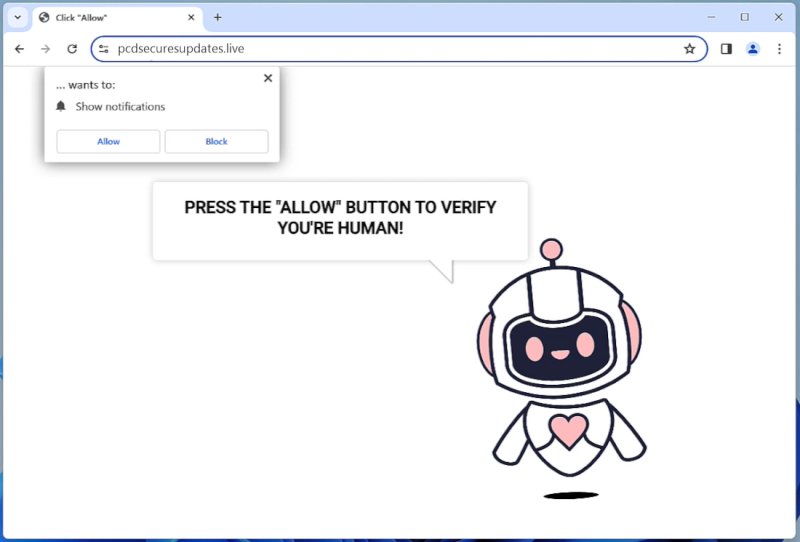
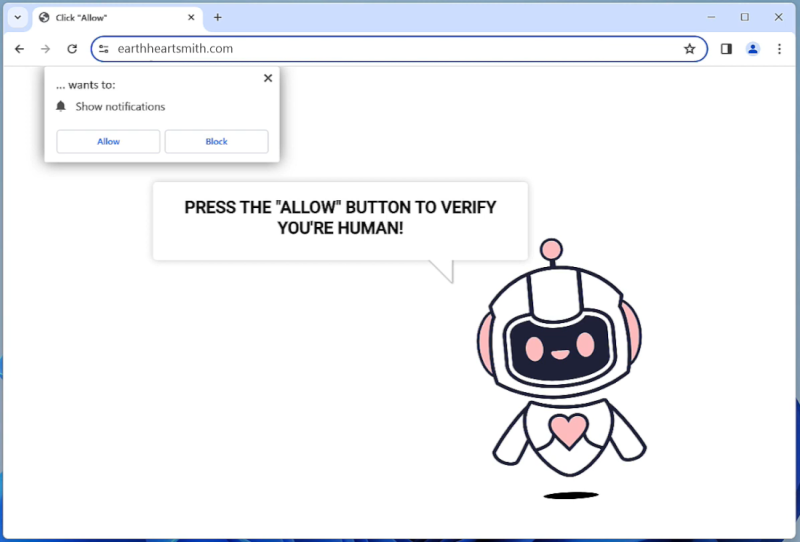
Pcdsecuresupdates.live is a malicious website that tricks users into allowing browser notifications by displaying fake error messages claiming that the user’s device needs updates for security reasons. Once granted permission, the website starts displaying intrusive pop-up notifications, ads, and redirects to other potentially harmful websites. This can lead to a compromised browsing experience, as well as potential exposure to malware and other cyber threats.
Pcdsecuresupdates.live primarily targets users of popular web browsers such as Google Chrome, Mozilla Firefox, and Microsoft Edge. It can infect both desktop and mobile devices, making it a widespread threat across various platforms. The deceptive tactics used by this website exploit users’ trust in software update notifications, ultimately leading to the infiltration of their devices and the exposure of sensitive information. It is important for users to be cautious when encountering such websites and to avoid granting unnecessary permissions to prevent potential security risks.