How to remove Troll Stealer
Troll Stealer is a type of malicious software, also known as malware, that aims to steal sensitive information from an infected computer. It is often categorized as a Trojan horse, which refers to a program that disguises itself as a legitimate file or software to trick users into downloading and executing it.
Troll Stealer typically infects computers through various means, including email attachments, malicious websites, software downloads from unreliable sources, or exploiting vulnerabilities in outdated software. Once the malware gains access to a computer, it can perform a range of malicious activities, such as:
1. Keylogging: Troll Stealer may record keystrokes and capture sensitive information like login credentials, credit card details, or personal data entered by the user.
2. Screen capturing: The malware can take screenshots of the infected computer’s screen, potentially capturing sensitive or private information.
3. Clipboard hijacking: Troll Stealer can monitor and capture data copied to the clipboard, including copied passwords or other sensitive information.
4. File stealing: The malware can search for specific files on the infected computer and exfiltrate them to remote servers controlled by cybercriminals. These files can include documents, images, or other personal data.
5. Remote access: Troll Stealer might enable unauthorized remote access to the infected computer, allowing cybercriminals to take control, steal information, or further compromise the system.
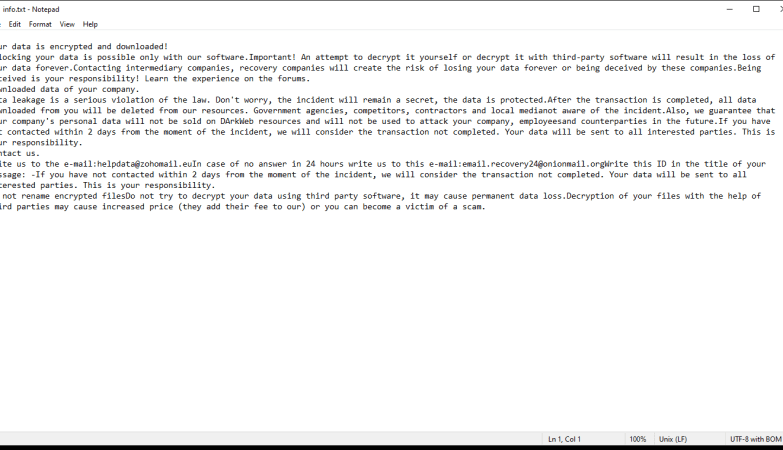
It is important to note that malware like Troll Stealer should be avoided and removed from infected computers as soon as possible to protect personal information and prevent further damage. Using up-to-date antivirus software, regularly updating system software, exercising caution while downloading files or visiting websites, and avoiding suspicious email attachments are some preventive measures to reduce the risk of infection.