How to remove Hogarlainz.com
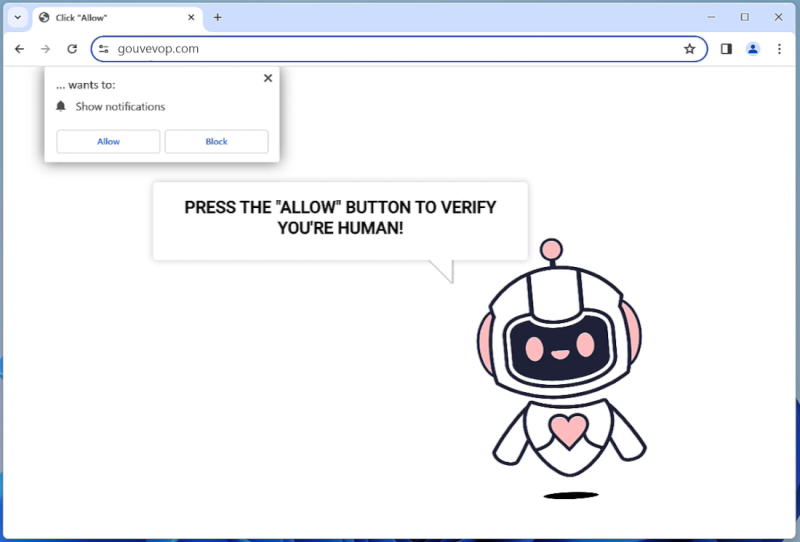
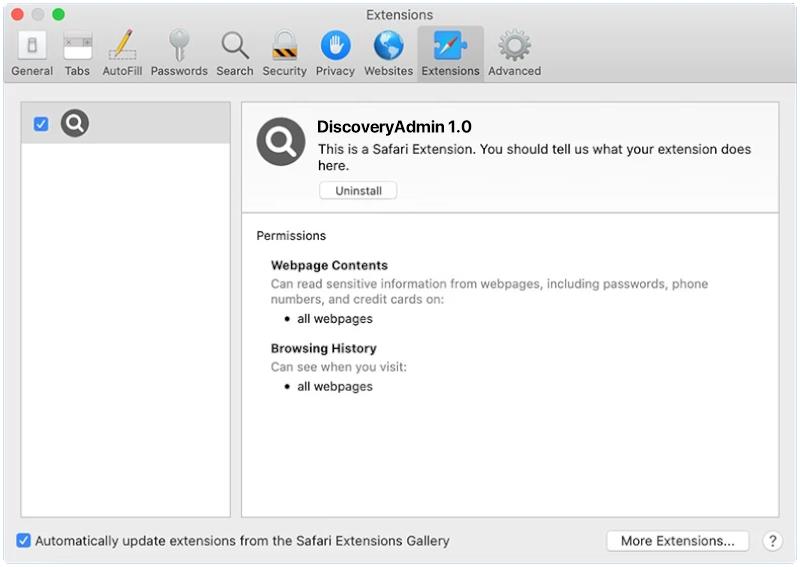
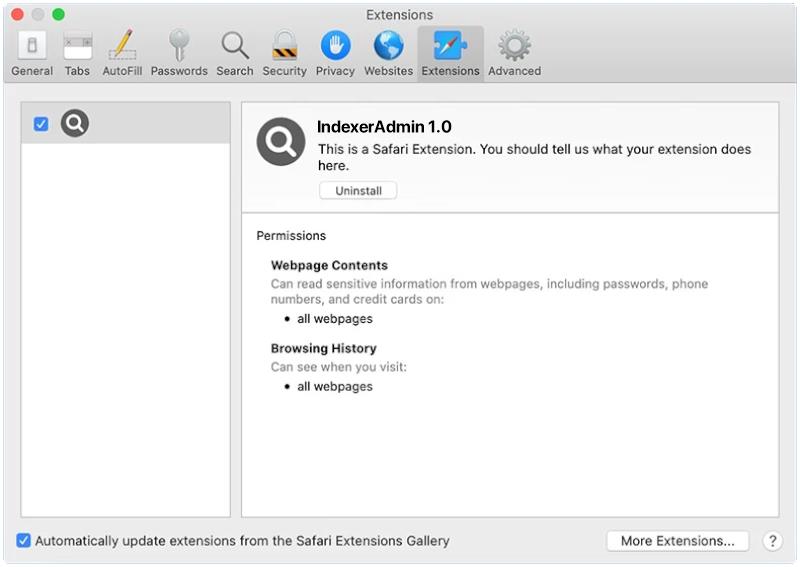
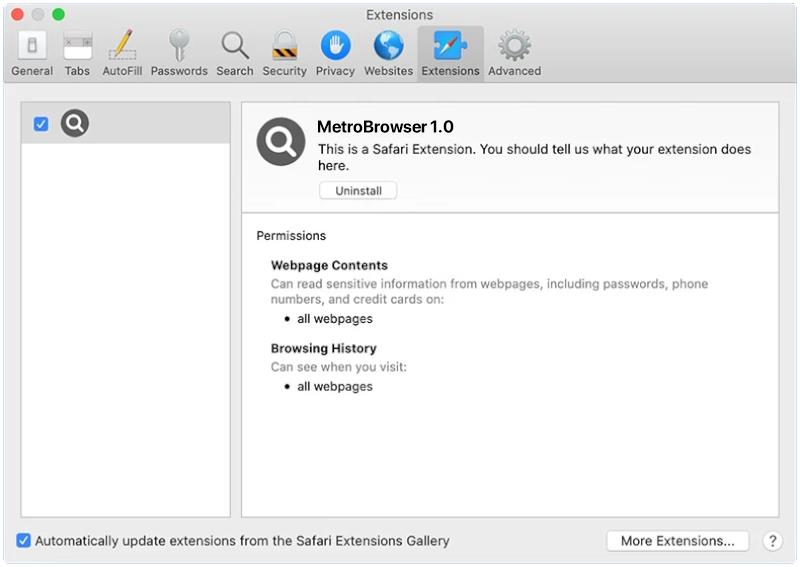
Hogarlainz.com is a type of adware that infects computers and web browsers by displaying intrusive advertisements and pop-ups on the user’s screen. This adware typically enters a system through bundled software downloads, malicious websites, or clicking on malicious links. Once installed, Hogarlainz.com can track the user’s online behavior and display targeted ads based on their browsing habits.
Hogarlainz.com adware can also redirect users to malicious websites and compromise their online security. It can slow down the computer’s performance, consume system resources, and make the browser crash frequently. Additionally, Hogarlainz.com may collect sensitive information such as browsing history, search queries, and personal data, putting the user’s privacy at risk. It is important for users to regularly scan their systems for adware and malware to prevent such infections and protect their personal information.