How to remove DarkMe
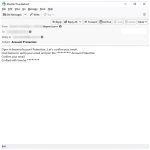
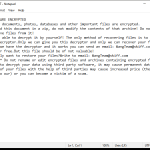
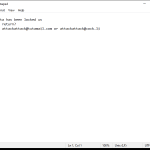
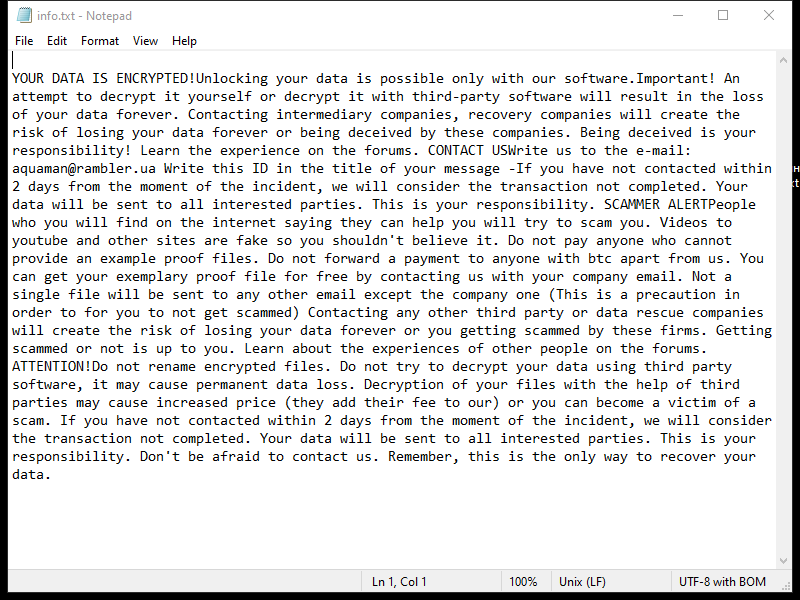
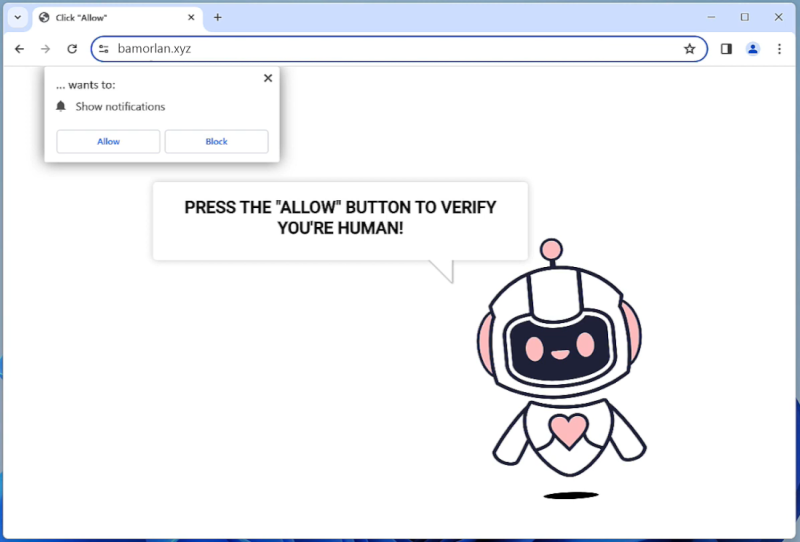
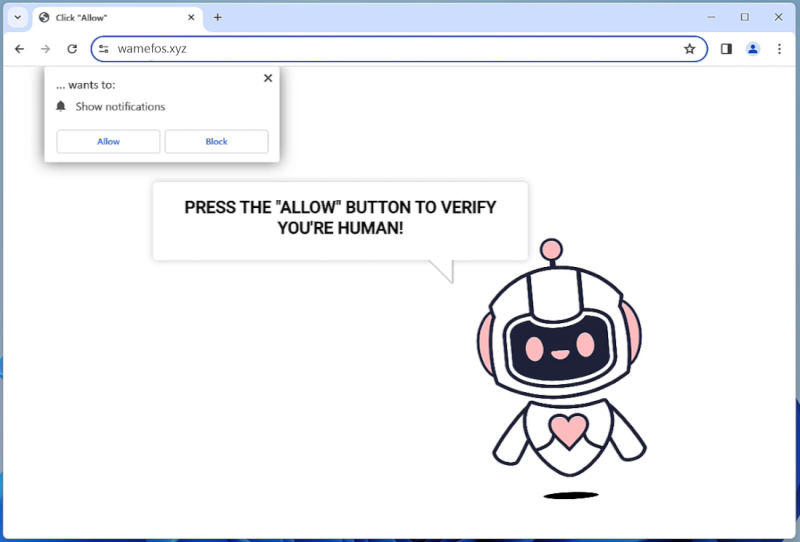
DarkMe is a type of malware that infects computers and is designed to steal sensitive information, such as personal data and financial details. This malware can be spread through malicious email attachments, infected websites, or by exploiting vulnerabilities in software and operating systems.
Once DarkMe infects a computer, it can run in the background without the user’s knowledge, collecting data and sending it to remote servers controlled by cybercriminals. It can also open backdoors on the infected computer, allowing hackers to access the system and carry out further malicious activities.
To protect against DarkMe and other types of malware, users should regularly update their software, use strong passwords, and be cautious when clicking on links or downloading attachments from unknown sources. It is also recommended to install reputable antivirus software and regularly scan your computer for malware.