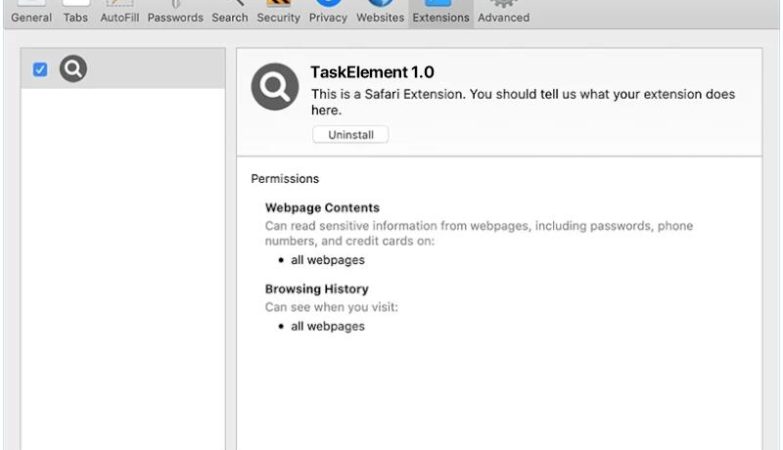
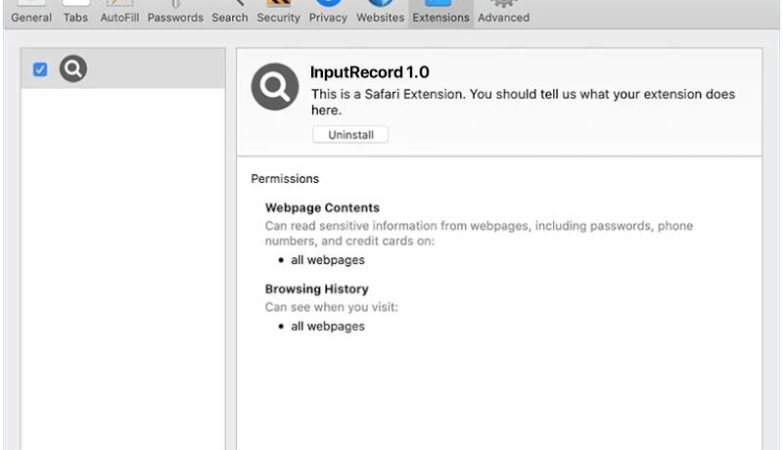
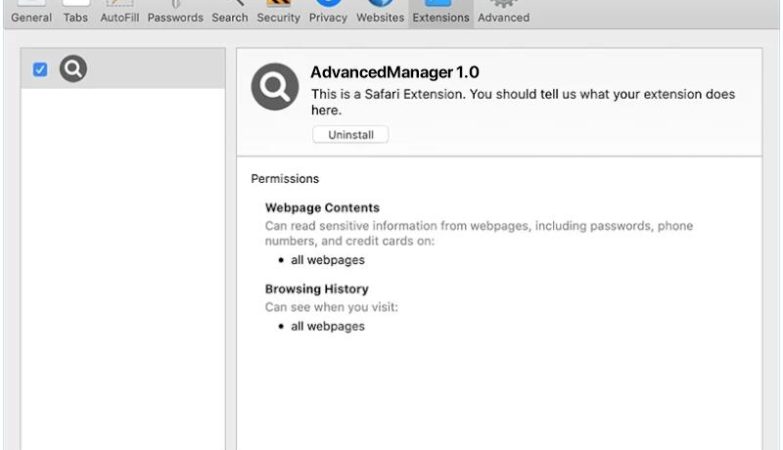
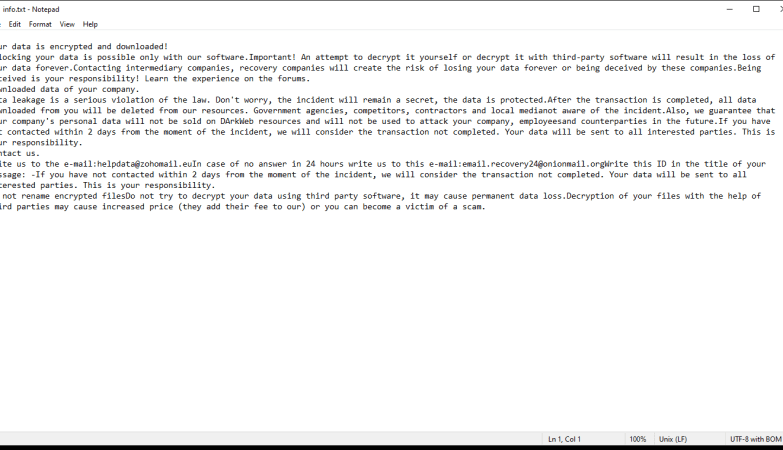
How to remove Backdoor:Win32/Xtrat.B
Backdoor:Win32/Xtrat.B is a type of malicious software, also known as malware, that belongs to the category of backdoor Trojan horses. It is designed to gain unauthorized access to a computer system and allow remote control and administration by an attacker.
Backdoor:Win32/Xtrat.B can infect computers in several ways, including:
1. Email attachments: It may be distributed through malicious email attachments disguised as legitimate files, such as documents or images. When users open these attachments, the malware gets executed.
2. Infected websites: Visiting compromised websites or clicking on malicious ads can lead to the automatic download and installation of Backdoor:Win32/Xtrat.B onto the user’s computer.
3. Software vulnerabilities: Exploiting security vulnerabilities in outdated or unpatched software can provide an entry point for Backdoor:Win32/Xtrat.B to infect a computer.
4. Peer-to-peer networks: It can be distributed through file-sharing networks where users unknowingly download infected files shared by others.
Once infected, Backdoor:Win32/Xtrat.B can perform various malicious activities, including stealing sensitive information, logging keystrokes, capturing screenshots, downloading additional malware, and providing a remote attacker with unauthorized access to the infected computer.
To protect your computer from this and other malware infections, it is essential to keep your operating system and software up-to-date, use a reliable antivirus program, exercise caution when opening email attachments or visiting unknown websites, and avoid downloading files from untrustworthy sources.