How to remove Trojan:Win32/Smokeloader.Ww!Mtb
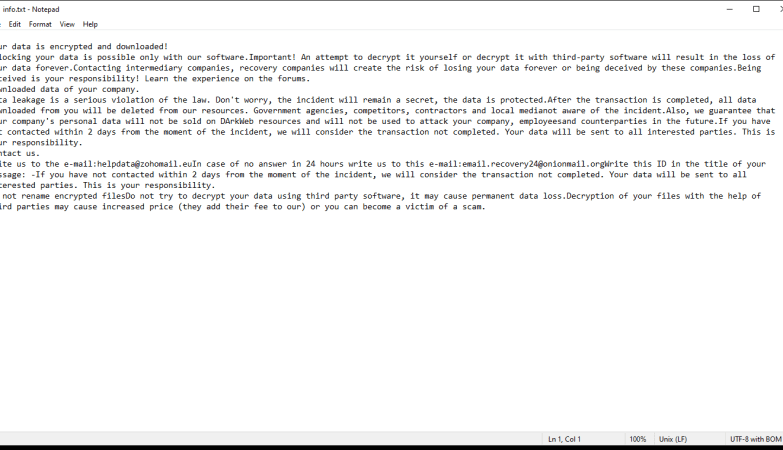
Trojan:Win32/Smokeloader.Ww!Mtb is a type of Trojan horse malware that infects computers by disguising itself as a legitimate file or program in order to gain access to the system. Once installed, it can perform various malicious activities such as stealing sensitive information, downloading additional malware, or causing system instability.
Trojan:Win32/Smokeloader.Ww!Mtb can infect computers through various means, including:
1. Email attachments: The Trojan may be disguised as an attachment in an email, prompting users to download and open the file.
2. Malicious websites: Visiting compromised websites or clicking on malicious links can also lead to the download and installation of the Trojan.
3. Software vulnerabilities: Exploiting vulnerabilities in software or operating systems can also be used by the Trojan to infect computers.
To protect against Trojan:Win32/Smokeloader.Ww!Mtb and other malware, it is important to keep your operating system and software up to date, avoid clicking on suspicious links or downloading attachments from unknown sources, and use reputable antivirus software to scan and remove any potential threats.