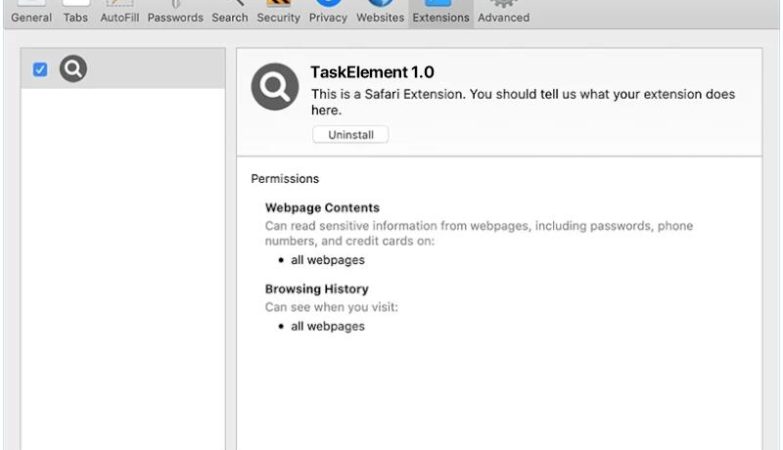
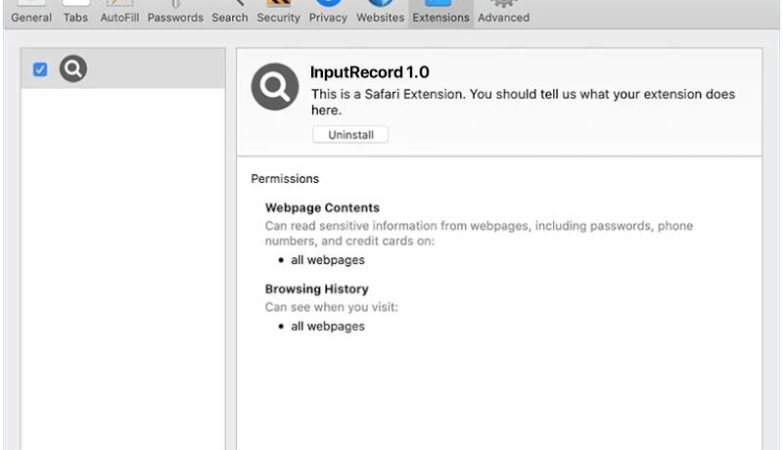
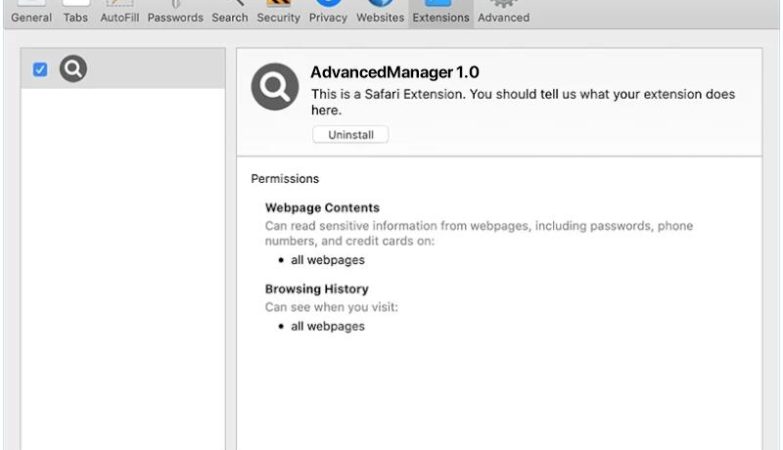
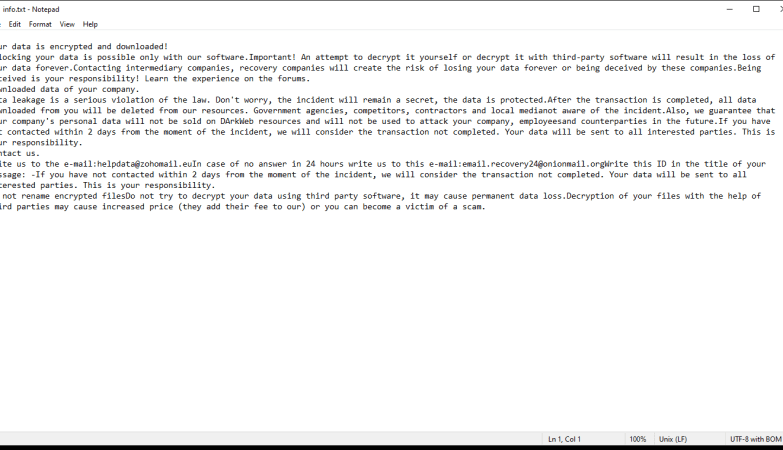
How to remove Save Turtle Tab
Save Turtle Tab adware is a potentially unwanted program (PUP) that can infect computers and browsers, causing unwanted advertisements to appear on the user’s screen. This adware typically gets installed on a user’s system without their consent and can modify browser settings to display intrusive ads. Save Turtle Tab is known to affect various browsers such as Google Chrome, Mozilla Firefox, and Internet Explorer.
Save Turtle Tab adware often enters a user’s computer through software bundling, where it is included in the installation package of legitimate software. Users unknowingly install the adware when they download and install freeware or shareware from untrustworthy sources. Once installed, Save Turtle Tab modifies the browser’s settings, such as the default search engine and homepage, to redirect the user to specific websites and display unwanted advertisements. These ads can be intrusive, covering the entire screen or appearing as pop-ups, banners, or in-text links. Save Turtle Tab adware not only disrupts the browsing experience but may also track the user’s online activities and collect sensitive information for marketing purposes.