How to remove Greenbean Banking Trojan (Android)
Greenbean Banking Trojan: Understanding its Functionality and Android Infection
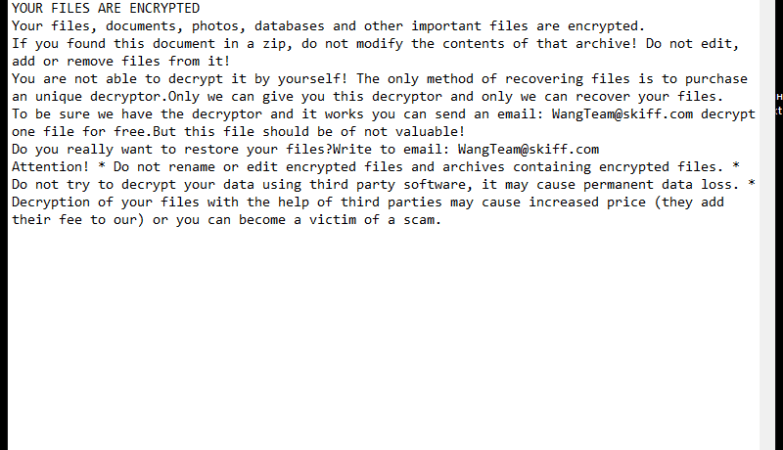
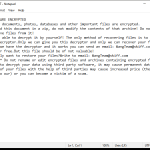
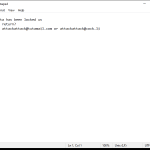
The Greenbean Banking Trojan is a malicious software program that specifically targets Android devices, seeking to exploit vulnerabilities and gain unauthorized access to users’ financial information. This sophisticated Trojan is designed to steal sensitive data, such as login credentials, credit card details, and other personal information, ultimately leading to financial losses and identity theft.
The Greenbean Banking Trojan primarily infects Android devices through various means, including but not limited to malicious websites, infected email attachments, and third-party app stores. Once the Trojan successfully infiltrates a device, it discreetly runs in the background, often evading detection by antivirus software. It then proceeds to monitor the user’s online activities, seeking opportunities to intercept sensitive data during financial transactions, banking activities, and other online operations.
To infect an Android device, the Greenbean Banking Trojan often uses social engineering techniques, deceiving users into downloading and installing infected applications or clicking on malicious links. Additionally, it can exploit vulnerabilities in outdated operating systems or apps, allowing it to gain root access and control over the device. Once established, the Trojan can intercept and modify communication between the user and legitimate banking apps, redirecting sensitive information to the attacker’s server without the user’s knowledge.
In conclusion, the Greenbean Banking Trojan poses a significant threat to Android users, leveraging various infection methods and exploiting vulnerabilities to access and steal sensitive financial information. To mitigate the risk of infection, users should exercise caution when downloading apps or clicking on links, especially from unknown or untrusted sources. Keeping devices and apps updated with the latest security patches is also crucial in preventing such Trojan infections. Additionally, it is recommended to use reliable antivirus software that can detect and remove potential threats, thus ensuring a safer online banking experience.