Hacktool:Powershell/Empiregetscreenshot is a type of hacking tool that is used to capture screenshots on infected computers. It is typically spread through phishing emails, malicious websites, or exploiting vulnerabilities in software. Once installed on a computer, Hacktool:Powershell/Empiregetscreenshot can run in the background without the user’s knowledge, capturing sensitive information and sending it to the attacker. It is important for users to be cautious when clicking on links or downloading attachments from unknown sources to prevent infection by this hacking tool.
Author: admin
How to remove Hacktool:Powershell/Inveigh
Hacktool:Powershell/Inveigh is a type of hacking tool that is used to perform network-based man-in-the-middle attacks and gather sensitive information from network traffic. It is typically deployed by cybercriminals to intercept and steal data, such as usernames and passwords, from unsuspecting users on a network.
Hacktool:Powershell/Inveigh infects computers by exploiting vulnerabilities in the network infrastructure or by being manually installed by an attacker who has gained unauthorized access to the system. Once installed, it runs in the background and begins intercepting network traffic, allowing the attacker to eavesdrop on communications and steal sensitive information.
To protect against Hacktool:Powershell/Inveigh and similar threats, it is important to keep software and systems up to date with the latest security patches, use strong passwords, and employ network security measures such as firewalls and intrusion detection systems. Regularly monitoring network traffic and conducting security audits can also help detect and mitigate potential threats from tools like Hacktool:Powershell/Inveigh.
How to remove Creso Rewards pop-ups
Creso Rewards is a potentially unwanted program (PUP) that functions as adware, displaying pop-up advertisements and coupons on web browsers. It is often bundled with other free software downloads and installed without the user’s knowledge or consent. Creso Rewards may also track users’ browsing activities and collect personal information for targeted advertising purposes.
When Creso Rewards appears in browsers, it can disrupt the user’s browsing experience by displaying intrusive ads and slowing down the performance of the browser. Users may also notice an increase in the number of pop-up windows and redirects to unfamiliar websites. To remove Creso Rewards from the browser, users should uninstall any suspicious programs from their computer and reset their browser settings to default. It is important to be cautious when downloading free software to avoid installing unwanted programs like Creso Rewards.
How to remove XploitSPY Malware (Android)
XploitSPY Malware is a type of malicious software that is designed to secretly infiltrate Android devices in order to steal sensitive information and spy on the device’s user. This malware is often distributed through malicious websites, email attachments, or fake apps, and once it infects a device, it can run in the background without the user’s knowledge. XploitSPY Malware is capable of logging keystrokes, capturing screenshots, recording audio and video, and accessing personal data such as passwords, financial information, and personal messages.
One common way that XploitSPY Malware infects Android devices is through phishing attacks, where users are tricked into clicking on a malicious link or downloading a fake app. Once the malware is installed on the device, it can exploit vulnerabilities in the Android operating system to gain access to sensitive information. Additionally, XploitSPY Malware can also spread through infected USB drives, Wi-Fi networks, or by disguising itself as a legitimate app in the Google Play Store. To protect against XploitSPY Malware, users should be cautious when clicking on links or downloading apps from unknown sources, keep their devices up to date with the latest security patches, and use reputable antivirus software to scan for and remove any malicious software.
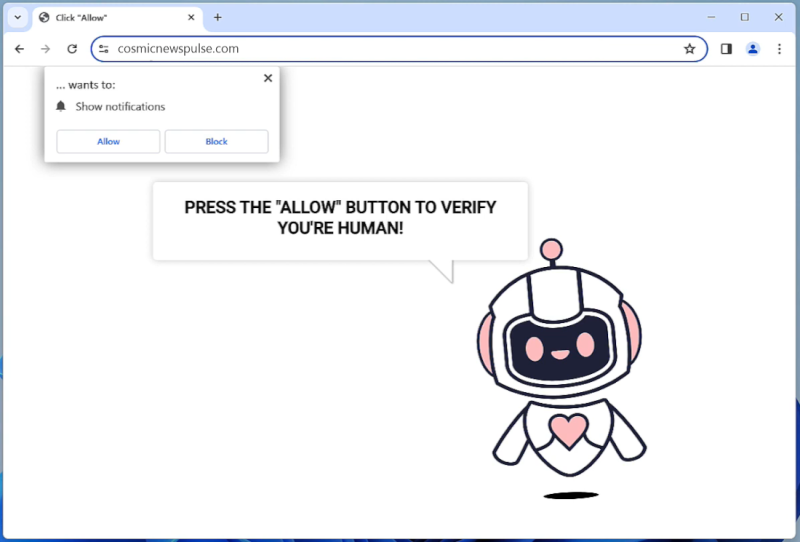
How to remove Cosmicnewspulse.com
Cosmicnewspulse.com is a malicious website that infects computers through various methods such as deceptive ads, fake software updates, or bundled with other software downloads. Once a user visits the website, it may prompt them to allow browser notifications. If the user grants permission, Cosmicnewspulse.com can then send unwanted and potentially harmful notifications directly to the user’s desktop or mobile device.
This website exploits browser notifications to push unwanted ads, fake alerts, or redirect users to malicious websites. It can affect a wide range of browsers including Google Chrome, Mozilla Firefox, Safari, and Microsoft Edge. Cosmicnewspulse.com is also capable of infecting various devices such as desktop computers, laptops, smartphones, and tablets. Users should be cautious when encountering such websites and avoid granting permission for notifications from unknown or suspicious sources to prevent unwanted infections and potential security risks.
How to remove Solana Mobile pop-ups
Solana Mobile is a browser-based cryptocurrency wallet that allows users to store, send, and receive digital assets on the Solana blockchain. It is designed to be user-friendly and secure, making it easy for individuals to manage their cryptocurrency holdings on-the-go. With Solana Mobile, users can access their funds anytime, anywhere, without the need for a separate hardware wallet or desktop software.
Solana Mobile may appear in browsers as a result of users accessing their cryptocurrency holdings through web-based applications or wallets. By using Solana Mobile in a browser, users can easily manage their digital assets without the need for additional downloads or installations. This can be convenient for individuals who prefer to access their cryptocurrency holdings through a web browser rather than a separate app or software platform.
How to remove AgentLocator (Mac)
AgentLocator is a type of malware that specifically targets Mac computers. This malware is designed to infiltrate Mac systems and gather sensitive information such as passwords, bank account details, and personal data. AgentLocator is often distributed through malicious websites, phishing emails, or software downloads from untrustworthy sources.
Once AgentLocator infects a Mac computer, it can run in the background without the user’s knowledge, silently collecting data and sending it to remote servers controlled by cybercriminals. This malware can also install additional malicious software or make changes to system settings, further compromising the security and privacy of the infected device. To protect against AgentLocator and other malware threats, Mac users should always be cautious when downloading software, avoid clicking on suspicious links or emails, and regularly update their operating system and security software.
How to remove Myhoroscopepro.com
Myhoroscopepro.com adware is a type of malicious software that displays unwanted advertisements, pop-ups, and redirects users to suspicious websites. This adware is often disguised as a legitimate horoscope or astrology website, tricking users into unknowingly installing it on their computers. Once installed, Myhoroscopepro.com adware collects user data, such as browsing history and search queries, to display targeted advertisements.
Myhoroscopepro.com adware typically infects computers through deceptive software bundling, where it is packaged with legitimate software downloads and installed without the user’s consent. It can also infect computers through malicious websites or email attachments. Once installed, Myhoroscopepro.com adware modifies browser settings and injects advertisements into web pages, causing a disruption in the user’s browsing experience. It is important for users to regularly scan their computers for adware and avoid downloading software from untrusted sources to prevent infection.
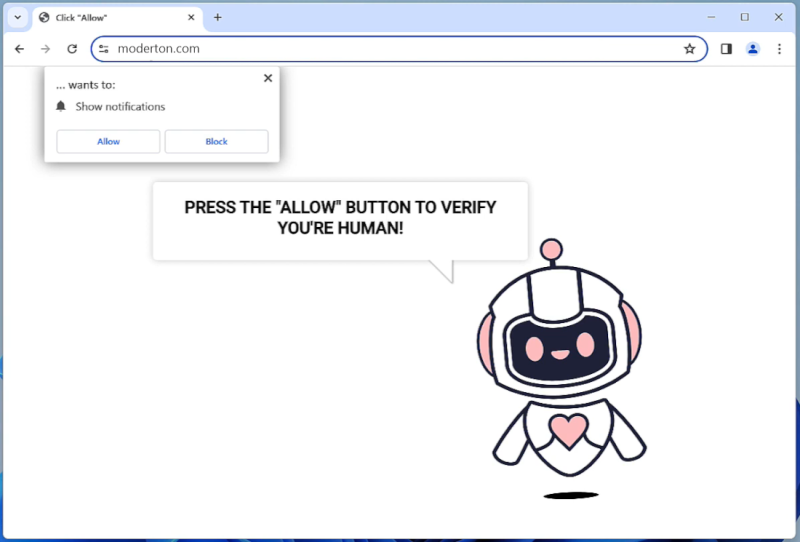
How to remove Moderton.com
Moderton.com is a malicious website that infects computers by tricking users into allowing notifications through their web browser. Once permission is granted, the website bombards the user with unwanted notifications that can contain malicious links or advertisements. These notifications can be very difficult to get rid of, as they continue to pop up even after closing the browser.
Moderton.com exploits browser notifications by using social engineering tactics to deceive users into clicking on the “Allow” button. The website may claim that notifications are necessary to access certain content or that they are required for security reasons. Once permission is granted, Moderton.com can continue to send notifications even when the browser is closed. This can be very annoying and disruptive for users, as well as potentially exposing them to malware or other online threats. Moderton.com can infect various web browsers such as Google Chrome, Mozilla Firefox, and Safari, and it can target devices running on Windows, MacOS, Android, and iOS. Users should be cautious when visiting unfamiliar websites and avoid granting unnecessary permissions to prevent falling victim to this type of malware.
How to remove BTCMining pop-ups
BTCMining is a process where individuals or groups use powerful computers to solve complex mathematical equations in order to validate and secure transactions on the Bitcoin network. In exchange for their efforts, miners are rewarded with newly created bitcoins. This process is crucial for the functioning of the Bitcoin network as it ensures the integrity of transactions and the overall security of the system.
BTCMining may appear in browsers as a result of websites running scripts that use visitors’ computer processing power to mine bitcoins without their knowledge or consent. This practice, known as cryptojacking, is often used by malicious actors to generate revenue by exploiting the processing power of unsuspecting users. In some cases, users may notice their computer slowing down or their device’s battery draining quickly, which can be a sign that BTCMining is taking place. Users can protect themselves by using ad blockers or antivirus software that can detect and block cryptojacking scripts.