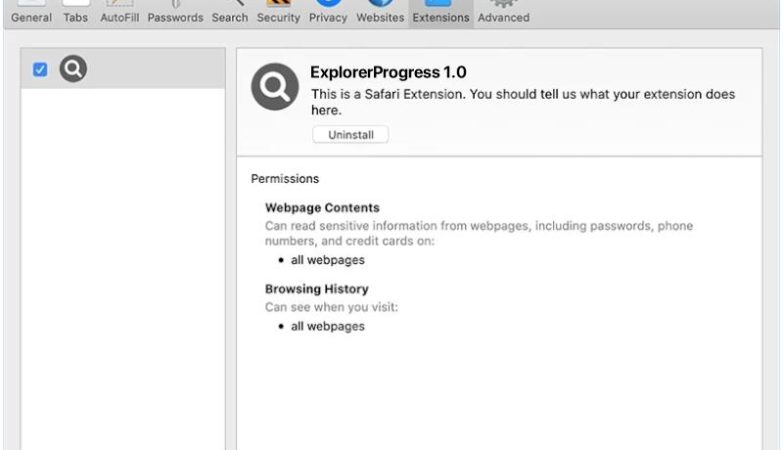
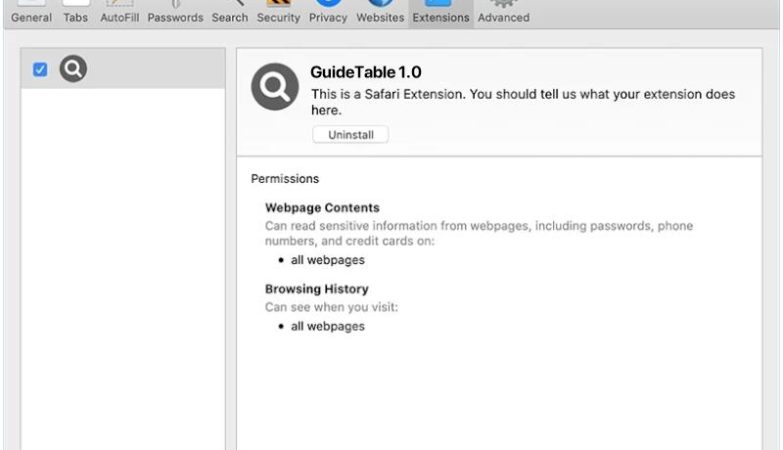
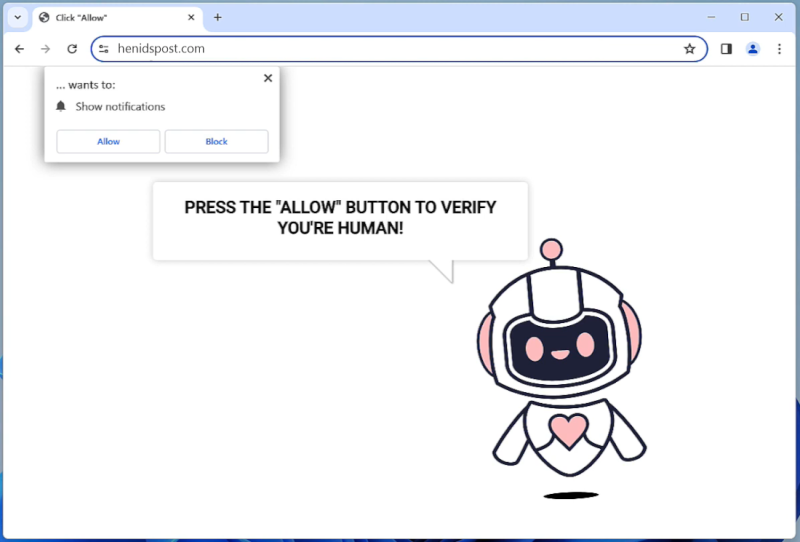
How to remove Henidspost.com
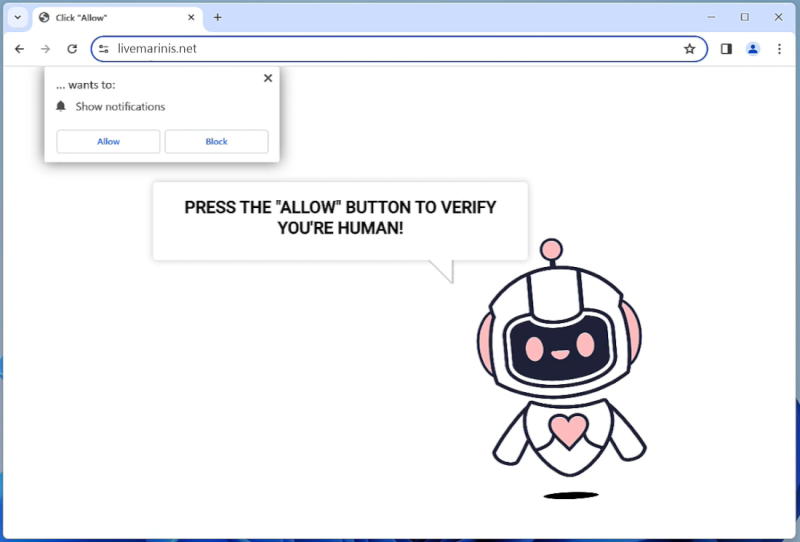
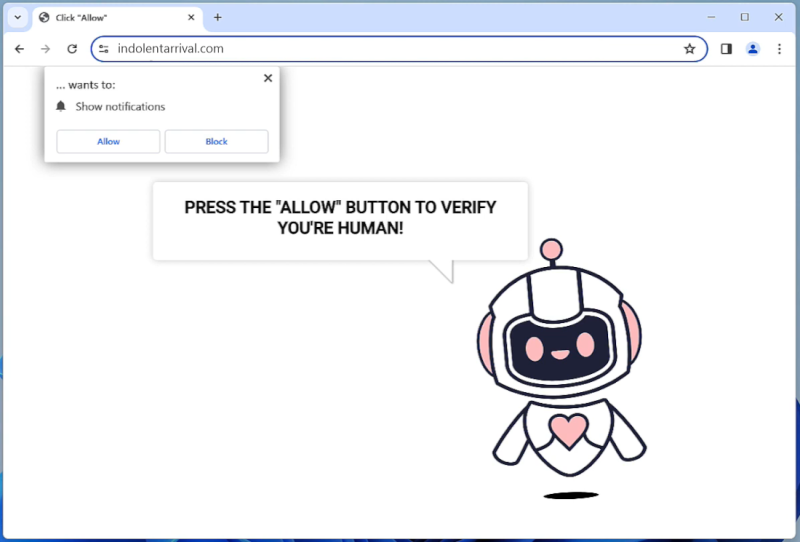
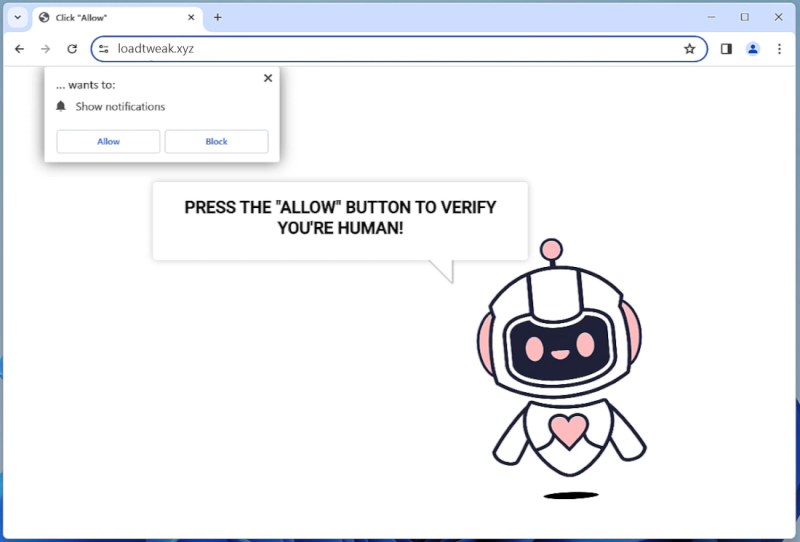
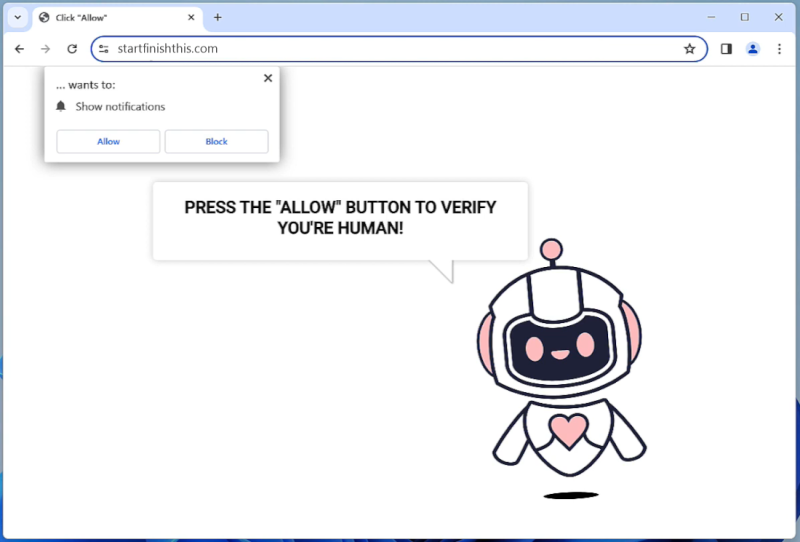
Henidspost.com is a malicious website that infects computers by tricking users into allowing browser notifications. Once users visit the site, they are prompted with a message asking them to click “Allow” to enable notifications. If the user clicks on this, they unwittingly grant permission for Henidspost.com to send push notifications to their browser.
Henidspost.com then exploits these browser notifications to bombard users with intrusive ads, pop-ups, and potentially harmful links. This can disrupt the user’s browsing experience, slow down their device, and expose them to further malware or phishing attacks. Henidspost.com is known to target a variety of browsers and devices, including Google Chrome, Mozilla Firefox, and Safari on both desktop and mobile platforms. Users should be cautious when encountering this website and avoid clicking on any prompts to enable notifications to prevent their devices from being infected.