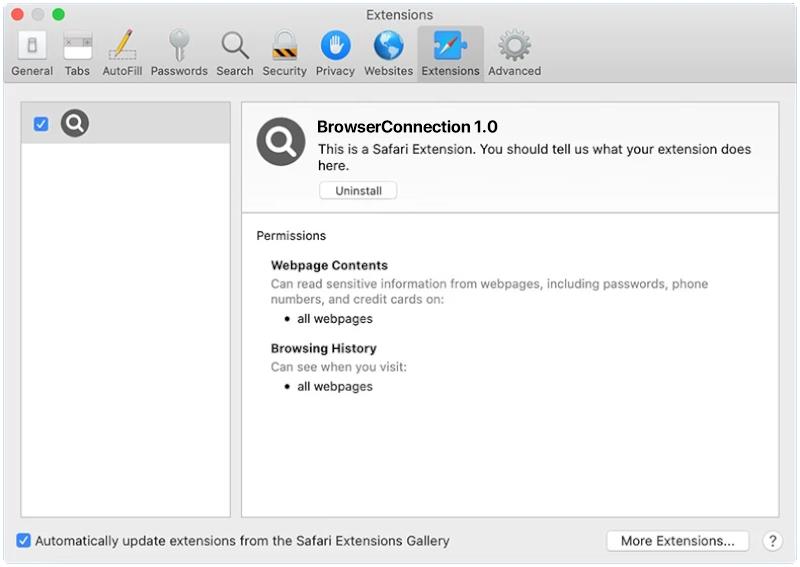
Recipesearchstore.com is adware that infiltrates computers and browsers without the user’s consent. It typically enters a system through bundling with free software downloads or by clicking on malicious ads or links. Once installed, Recipesearchstore.com displays intrusive pop-up ads, redirects users to sponsored websites, and collects browsing data to deliver targeted ads.
Recipesearchstore.com infects computers and browsers by exploiting vulnerabilities in the system or by tricking users into downloading and installing the adware unknowingly. It can also be spread through email attachments, fake software updates, or compromised websites. Once installed, Recipesearchstore.com modifies browser settings, injects unwanted ads into web pages, and tracks users’ online activities to generate revenue through pay-per-click advertising.