Extreamfanv5 is a type of malware that infects computers by exploiting vulnerabilities in software or by tricking users into downloading and installing it unknowingly. Once installed, Extreamfanv5 can perform a variety of malicious activities, such as stealing sensitive information, disrupting system operations, and spreading to other connected devices on the network. Users should be cautious when downloading files or clicking on suspicious links to avoid infection by Extreamfanv5.
Author: admin
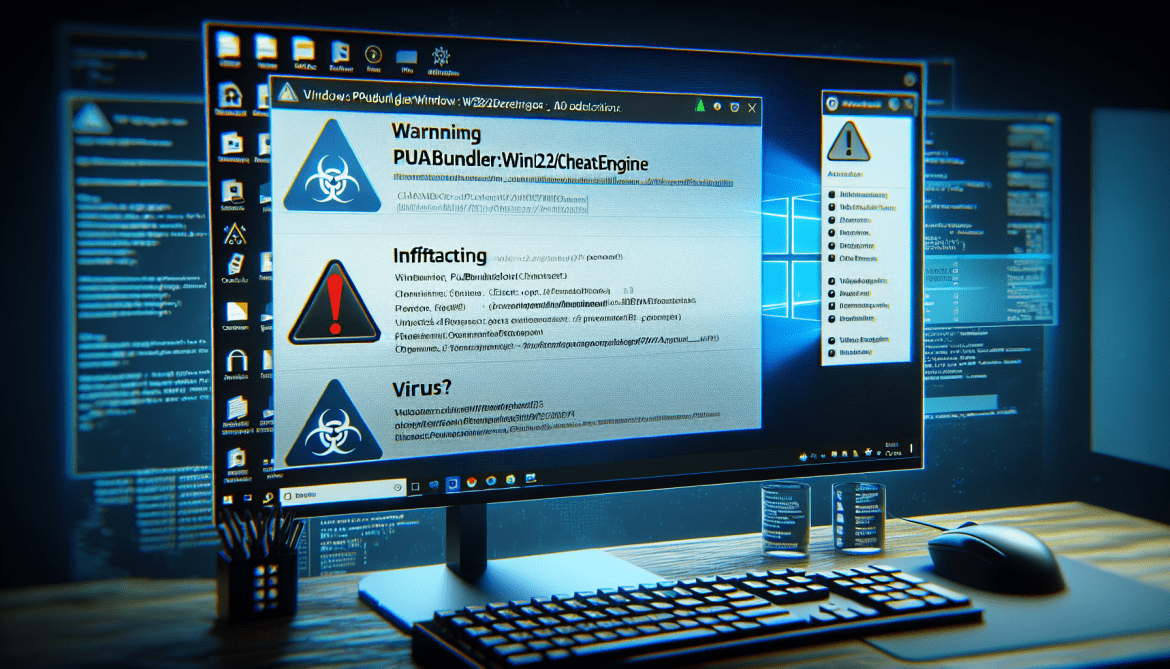
How to remove Puabundler:Win32/Cheatengine
Puabundler:Win32/Cheatengine is a potentially unwanted application that is designed to bundle with legitimate software and install on a user’s computer without their knowledge or consent. Once installed, Puabundler:Win32/Cheatengine may display unwanted advertisements, collect personal information, or perform other malicious activities.
Puabundler:Win32/Cheatengine can infect computers through various methods, such as being bundled with freeware or shareware programs, disguised as a legitimate software update, or distributed through malicious websites or email attachments. Users should be cautious when downloading and installing software from the internet to avoid inadvertently installing Puabundler:Win32/Cheatengine or other potentially unwanted programs.
How to remove Trojan:Bat/Alien.Rpa!Mtb
Trojan:Bat/Alien.Rpa!Mtb is a type of Trojan malware that infects computers by disguising itself as a legitimate file or program. Once the Trojan is executed on the system, it can perform various malicious activities such as stealing sensitive information, corrupting files, and allowing remote hackers to gain unauthorized access to the infected computer.
Trojan:Bat/Alien.Rpa!Mtb can infect computers through various means, including email attachments, malicious websites, and software downloads. It may also spread through infected USB drives or other removable storage devices. Once the Trojan has infiltrated a computer, it can be difficult to detect and remove, as it often operates silently in the background without the user’s knowledge.
To protect against Trojan:Bat/Alien.Rpa!Mtb and other types of malware, it is important to use reputable antivirus software, keep operating systems and software up to date, avoid clicking on suspicious links or downloading files from unknown sources, and regularly back up important data.
How to remove Trojan:Msil/Lazy!Mtb
Trojan:Msil/Lazy!Mtb is a type of malicious software, commonly known as a Trojan horse, that infects computers by disguising itself as a legitimate program or file. Once it infiltrates a system, Trojan:Msil/Lazy!Mtb can perform various harmful activities, such as stealing sensitive information, corrupting files, or allowing unauthorized access to the infected computer.
Trojan:Msil/Lazy!Mtb can infect computers through various means, including email attachments, malicious websites, or software downloads from untrusted sources. Once a user unknowingly downloads and executes the Trojan, it can start its malicious activities in the background without the user’s knowledge.
To prevent infection by Trojan:Msil/Lazy!Mtb and other types of malware, it is essential to exercise caution when downloading files or programs from the internet, avoid clicking on suspicious links or email attachments, and regularly update antivirus software to detect and remove any potential threats.
How to remove Trojan:Win32/Lazy!Mtb
Trojan:Win32/Lazy!Mtb is a type of malicious software that falls under the category of Trojans. This particular Trojan is known for its ability to infect computers and steal sensitive information such as login credentials, financial data, and personal information.
Trojan:Win32/Lazy!Mtb typically infects computers through various methods, including:
1. Email attachments: The Trojan may be disguised as an email attachment that appears to be legitimate but actually contains the malicious code.
2. Infected websites: Visiting malicious websites or clicking on malicious links can also lead to the installation of Trojan:Win32/Lazy!Mtb on a computer.
3. Peer-to-peer file sharing: Downloading files from unreliable sources or using peer-to-peer file sharing programs can expose a computer to Trojans like Trojan:Win32/Lazy!Mtb.
Once installed on a computer, Trojan:Win32/Lazy!Mtb can perform a variety of harmful actions, such as stealing sensitive information, spying on user activities, and allowing remote access to the infected system. It is important for computer users to have up-to-date security software and to exercise caution when downloading files or clicking on links to prevent infection by this Trojan and other malware.
How to remove Victoria Pigments
Victoria Pigments is a type of malicious software, also known as malware, that infects computers and mobile devices. It typically spreads through email attachments, infected websites, or by exploiting vulnerabilities in software or operating systems.
Once installed on a device, Victoria Pigments can steal sensitive information, such as login credentials, credit card numbers, and personal data. It can also disrupt the normal functioning of the infected device, causing it to slow down, crash, or become unresponsive.
To protect against Victoria Pigments and other malware, it is important to regularly update software and operating systems, use strong and unique passwords, and be cautious when clicking on links or downloading attachments from unknown sources. Additionally, installing reputable antivirus software can help detect and remove malware infections.
How to remove Wintrackersp
Wintrackersp is a type of adware that infects computers by bundling itself with other software downloads or by tricking users into clicking on malicious links or ads. Once installed, Wintrackersp bombards the user with unwanted advertisements and may also track their browsing activity to gather personal information for targeted advertising. It can slow down the computer’s performance and may also lead to other malware infections. It is important to have a reputable antivirus program installed on your computer to prevent and remove Wintrackersp and other adware infections.
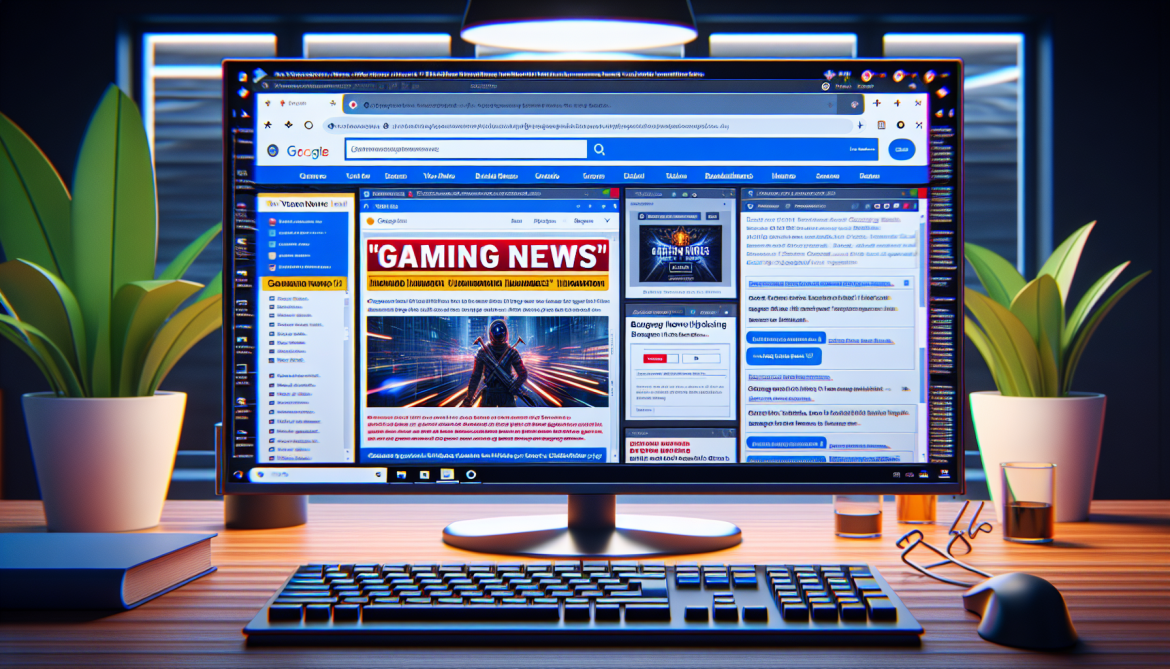
How to remove Gaming News Tab
Gaming News Tab adware is a type of malicious software that displays unwanted advertisements and pop-ups on a user’s computer or web browser. This adware is designed to generate revenue for the creators by redirecting users to sponsored websites and promoting various products or services. Gaming News Tab can be installed on a computer without the user’s knowledge or consent, often bundled with free software downloads or through malicious websites.
Gaming News Tab infects computers and browsers by exploiting vulnerabilities in the system or by tricking users into installing it unknowingly. Once installed, the adware may change browser settings, inject ads into web pages, and track the user’s online activities to display targeted advertisements. Gaming News Tab can slow down the computer’s performance, cause browser crashes, and compromise the user’s privacy and security. It is important for users to be cautious when downloading software or clicking on suspicious links to prevent infection by adware like Gaming News Tab.
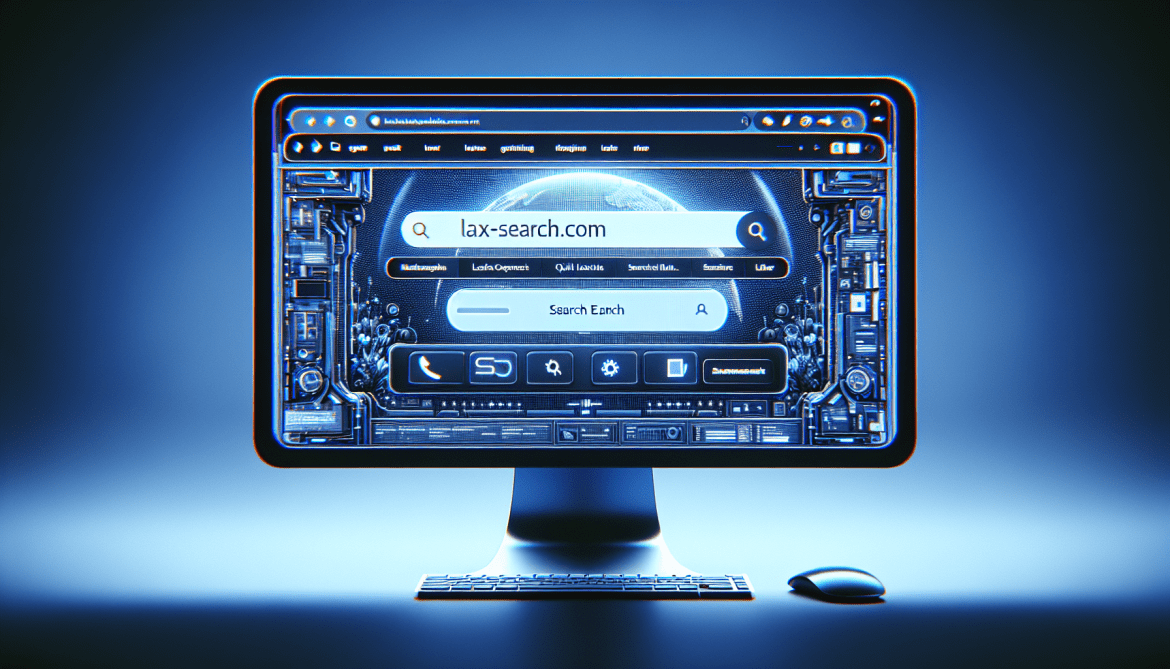
How to remove Lax-Search.com
Lax-Search.com is a type of adware that infects computers and web browsers by displaying intrusive advertisements and redirecting users to unwanted websites. This adware typically installs itself on a user’s computer without their knowledge or consent, often bundled with freeware or shareware programs. Once installed, Lax-Search.com will start displaying pop-up ads, banners, and in-text advertisements on the affected browser, making it difficult for users to browse the internet without interruption.
In addition to displaying advertisements, Lax-Search.com may also track users’ online activities and collect personal information, such as browsing history and search queries. This data is often used for targeted advertising purposes, as well as potentially being sold to third parties. To remove Lax-Search.com adware from a computer, users may need to run a reputable antivirus or anti-malware program and reset their browser settings to default. Additionally, users should be cautious when downloading and installing software from the internet to avoid inadvertently installing adware programs like Lax-Search.com.
How to remove Search.crowdsearch.net
Search.crowdsearch.net is a type of adware that infects computers and browsers by redirecting users’ search queries to its own search engine. This adware typically gets installed on a user’s computer without their knowledge or consent, often bundled with freeware or shareware downloads. Once installed, Search.crowdsearch.net modifies browser settings and injects unwanted advertisements into search results, leading to a poor browsing experience for the user.
Search.crowdsearch.net can infect computers and browsers through various means, such as malicious websites, fake software updates, or email attachments. Once installed, it can track users’ browsing habits, collect personal information, and display targeted advertisements based on this data. In addition, Search.crowdsearch.net may also cause browser instability, slow down system performance, and expose users to potential security risks. It is important for users to regularly scan their computers for adware and malware to prevent such infections.