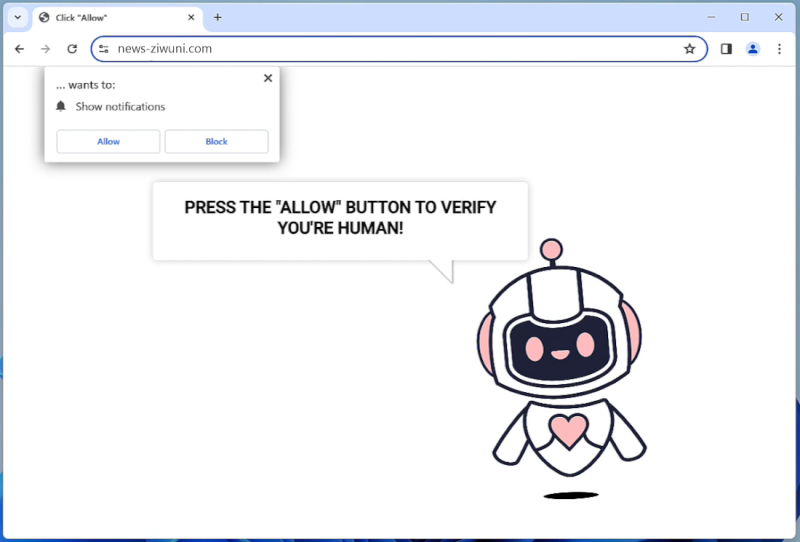
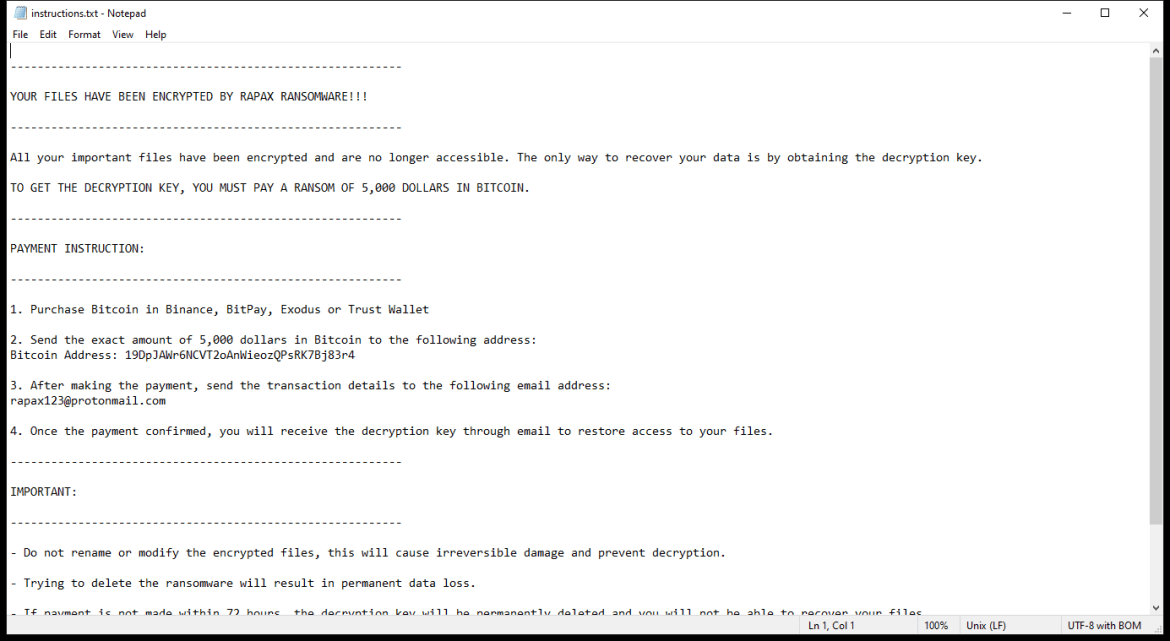
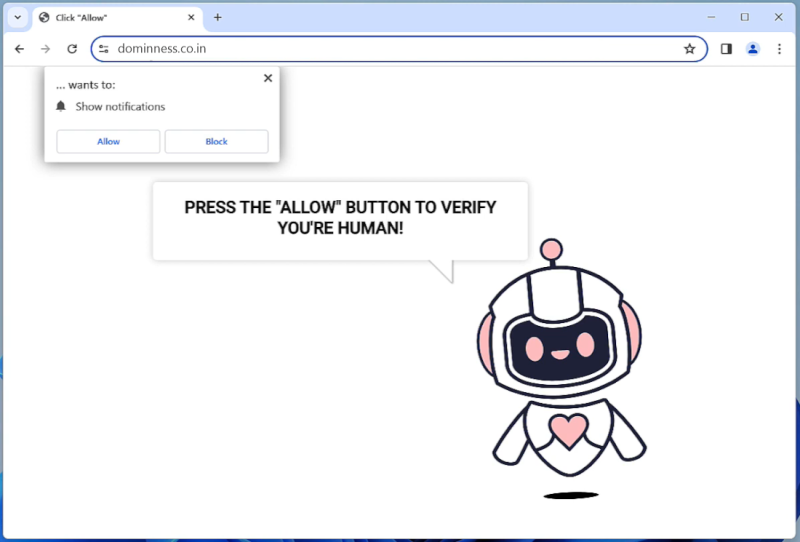
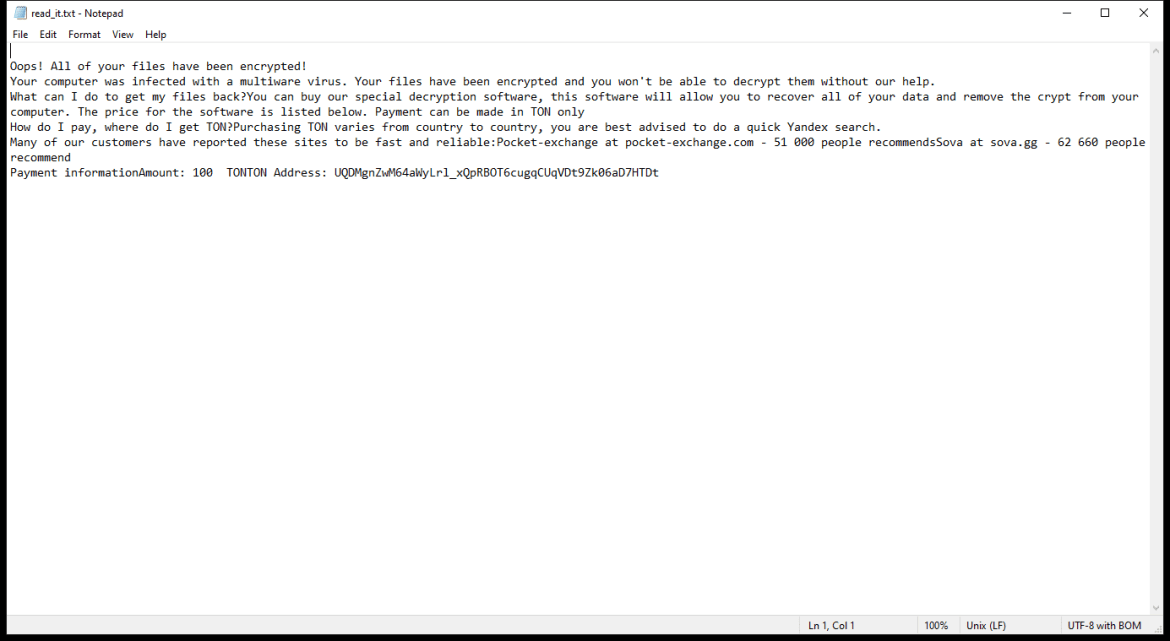
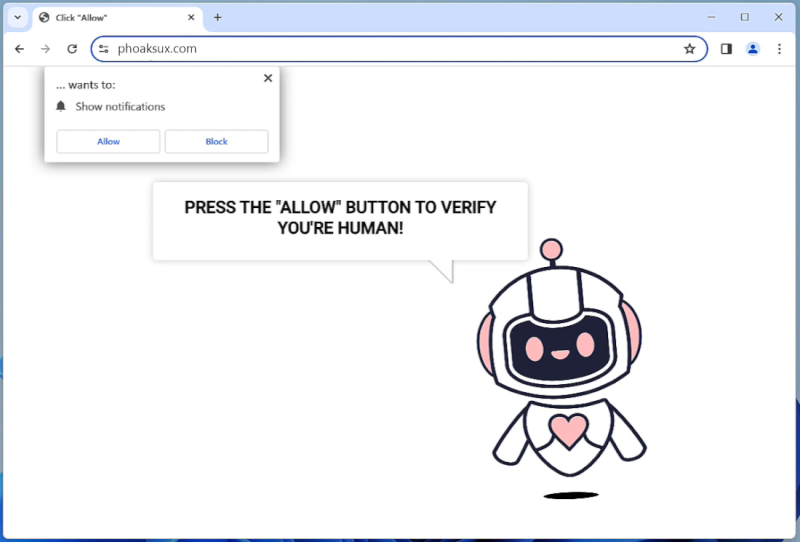
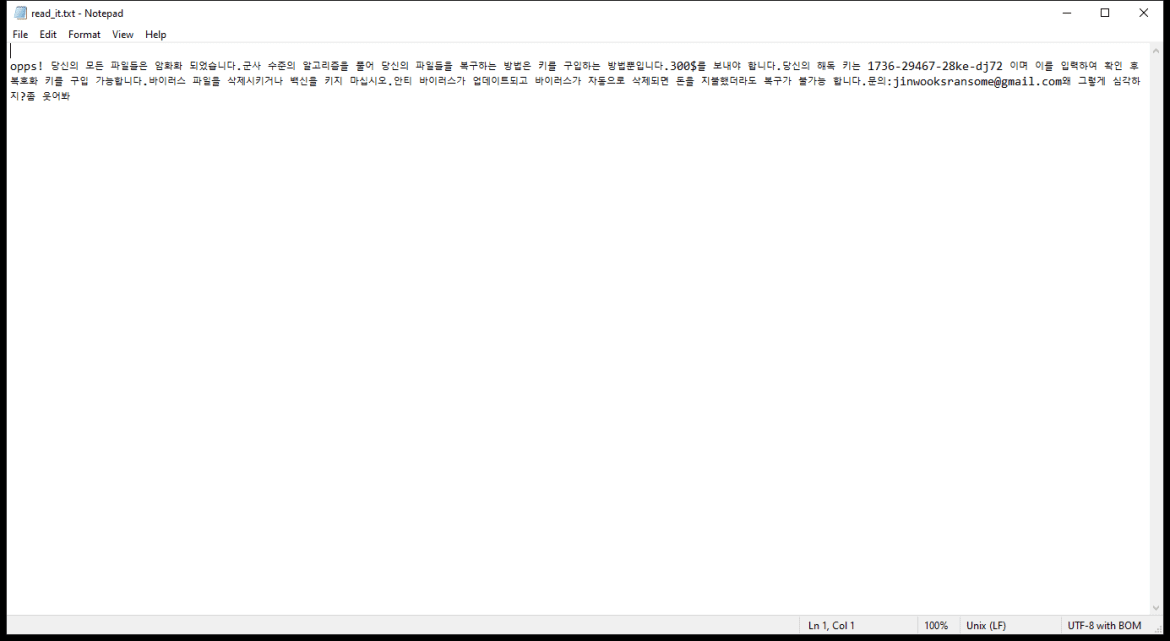
HelioNanoen is a type of adware that infects computers by displaying unwanted advertisements and pop-ups on the user’s web browser. This adware usually gets installed on a computer when the user unknowingly downloads and installs a software bundle that includes the HelioNanoen adware. Once installed, HelioNanoen starts displaying advertisements, redirects the user to sponsored websites, and tracks the user’s browsing behavior to deliver targeted ads.
HelioNanoen can also infect computers through malicious websites, email attachments, or fake software updates. It can be difficult to remove HelioNanoen from a computer as it may disguise itself as a legitimate program or hide in the system files. Users are advised to be cautious when downloading software from the internet and to regularly scan their computer for any signs of adware infections.