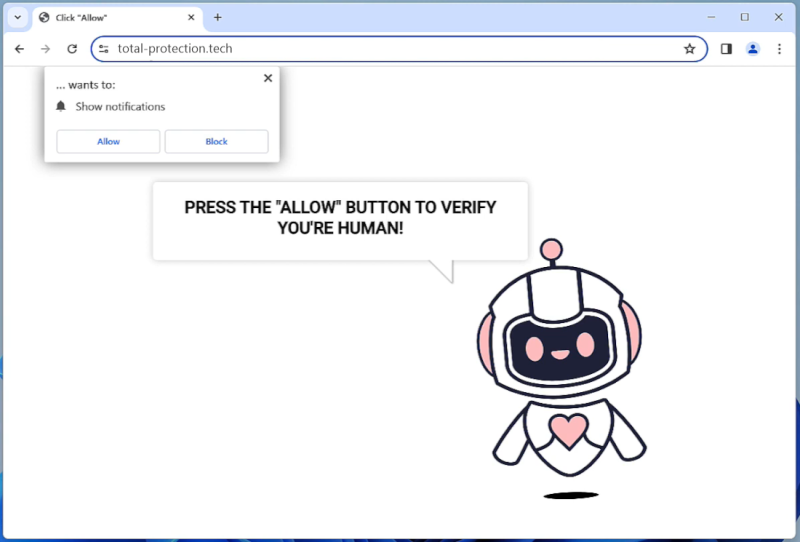
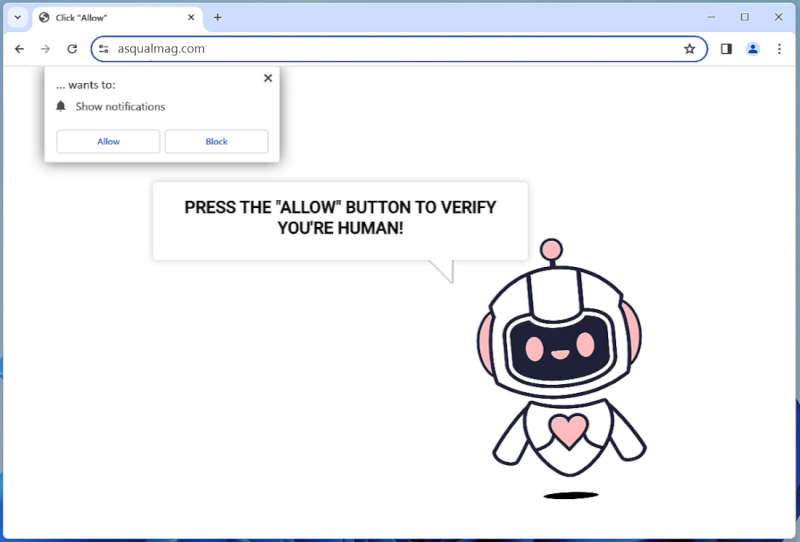
Total-protection.tech is a malicious website that poses as a legitimate security tool to deceive users into allowing browser notifications. Once users grant permission, the website bombards them with intrusive pop-up notifications containing misleading and potentially harmful content. This can lead to the installation of malware, adware, or other unwanted software on the infected computer.
Total-protection.tech exploits vulnerabilities in web browsers to display fake security alerts and trick users into downloading malicious software. It primarily targets popular browsers such as Google Chrome, Mozilla Firefox, and Microsoft Edge on various devices, including desktops, laptops, and mobile devices. Users should be cautious when encountering suspicious websites like Total-protection.tech and avoid granting permission for browser notifications to prevent potential security risks and protect their devices from malware infections.