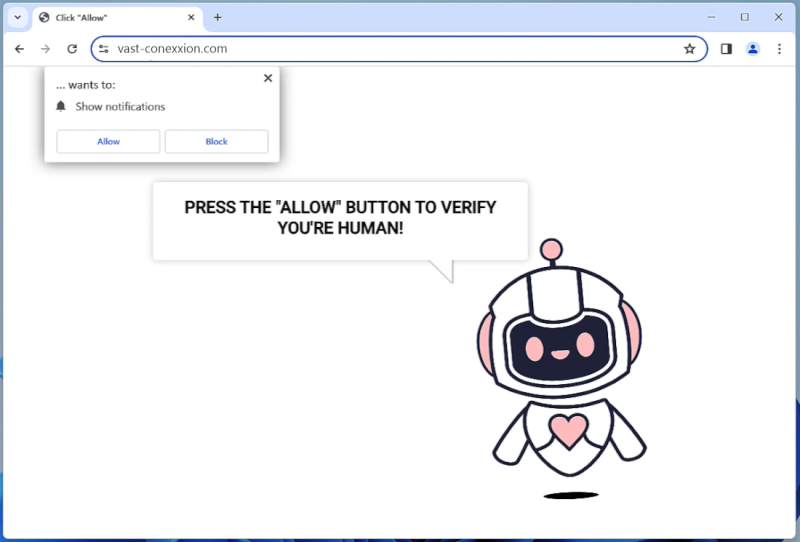
Vast-conexxion.com is a malicious website that infects computers with adware and potentially unwanted programs (PUPs). It typically spreads through software bundling, where the adware is hidden within free software downloads. Once installed on a computer, Vast-conexxion.com will display intrusive pop-up ads, redirect users to sponsored websites, and track their online activities for targeted advertising purposes.
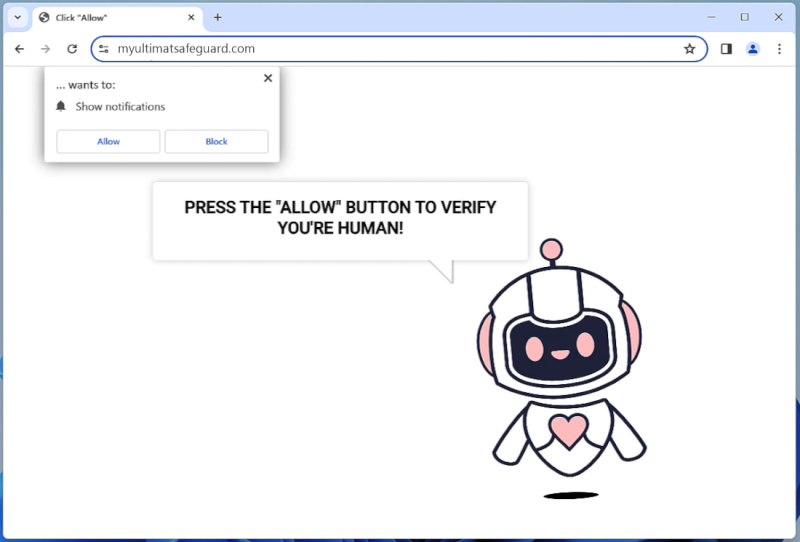
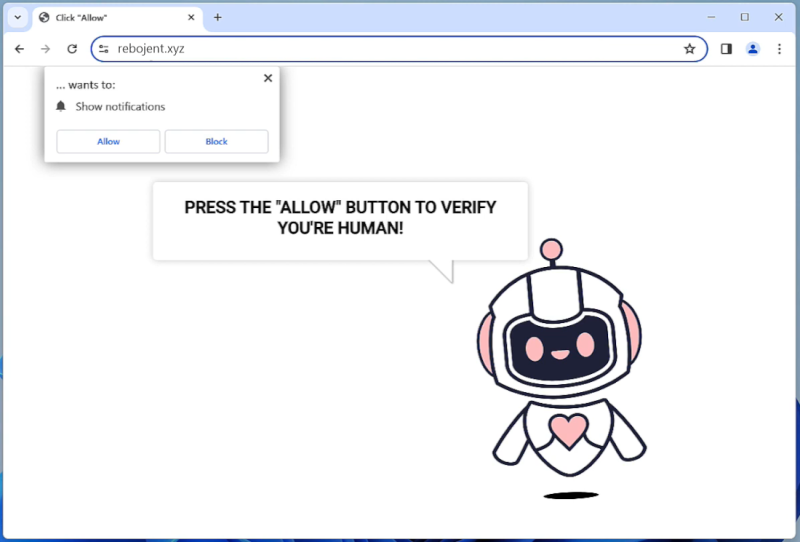
One of the tactics used by Vast-conexxion.com to exploit users is through browser notifications. It tricks users into allowing notifications, which then bombard them with more unwanted ads and notifications. This can be very annoying and disruptive to users’ browsing experience. Vast-conexxion.com can infect various web browsers such as Google Chrome, Mozilla Firefox, and Microsoft Edge, as well as different devices including PCs, laptops, and mobile phones. Users should be cautious when downloading free software and avoid clicking on suspicious links to prevent getting infected by Vast-conexxion.com and other similar adware.