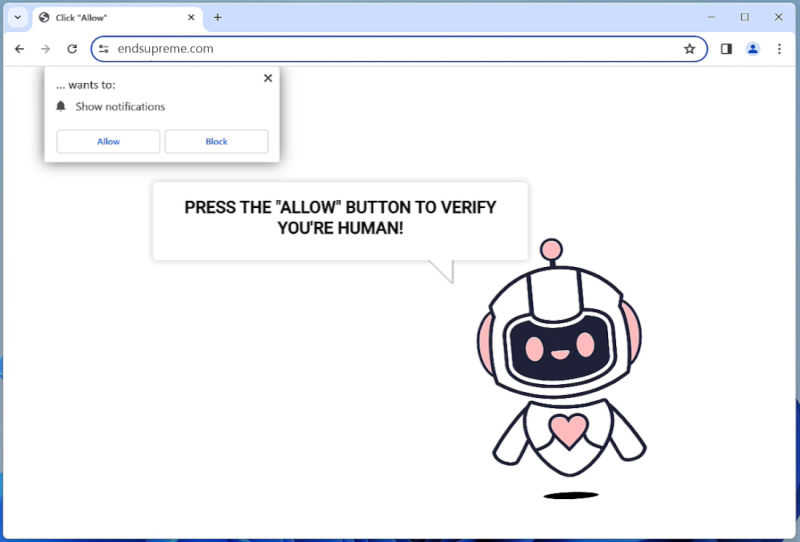
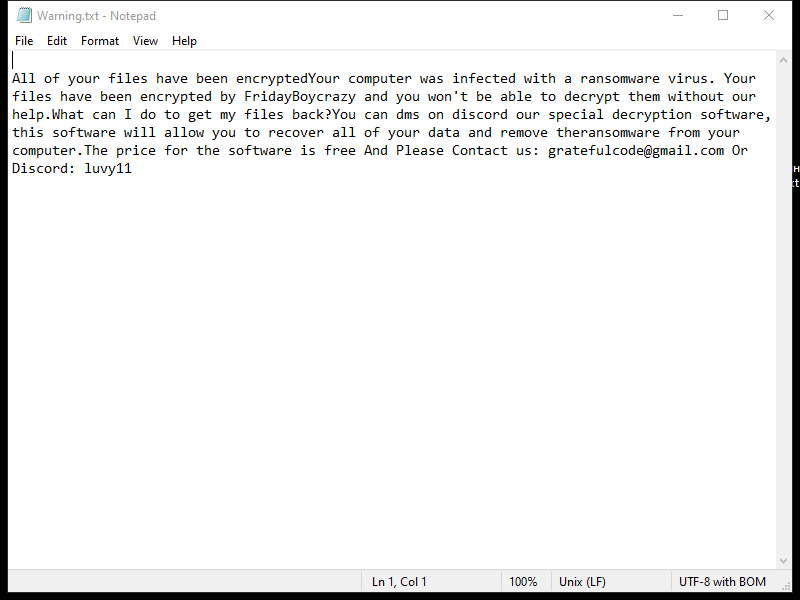
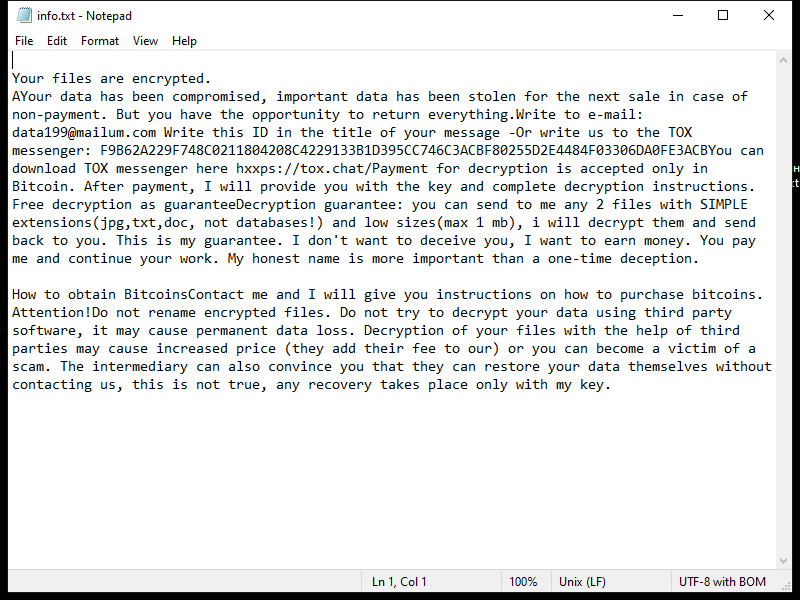
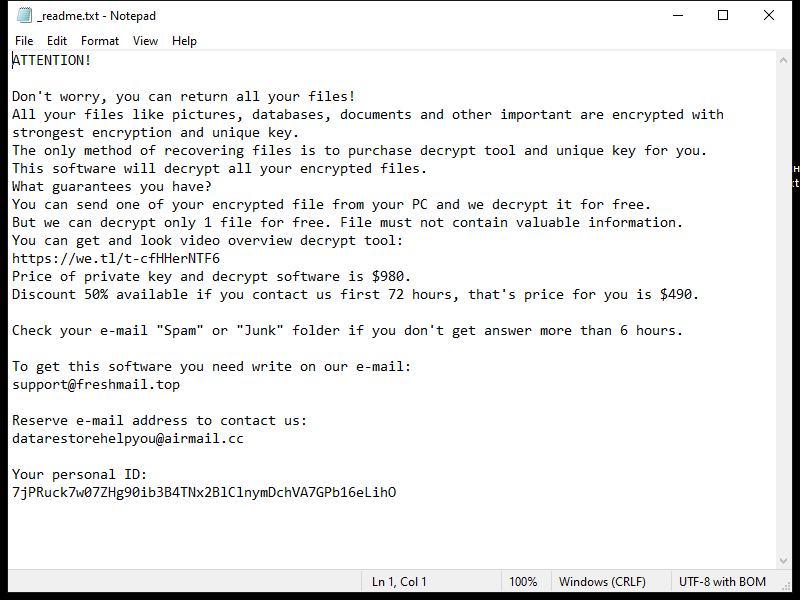
Finderssearching.com is a type of adware that infiltrates computers and internet browsers to display unwanted advertisements and redirect users to sponsored websites. This adware typically gets installed on a computer without the user’s knowledge or consent, often bundled with freeware or shareware downloads. Once installed, Finderssearching.com modifies browser settings and injects advertisements into webpages, disrupting the user’s browsing experience.
Finderssearching.com can infect computers through malicious websites, fake software updates, or spam email attachments. It may also be distributed through misleading advertisements or pop-ups that trick users into clicking on them. Once installed, Finderssearching.com collects user data and browsing habits to display targeted ads. To protect against Finderssearching.com and other adware, users should be cautious when downloading software from unfamiliar sources and regularly update their anti-virus software.