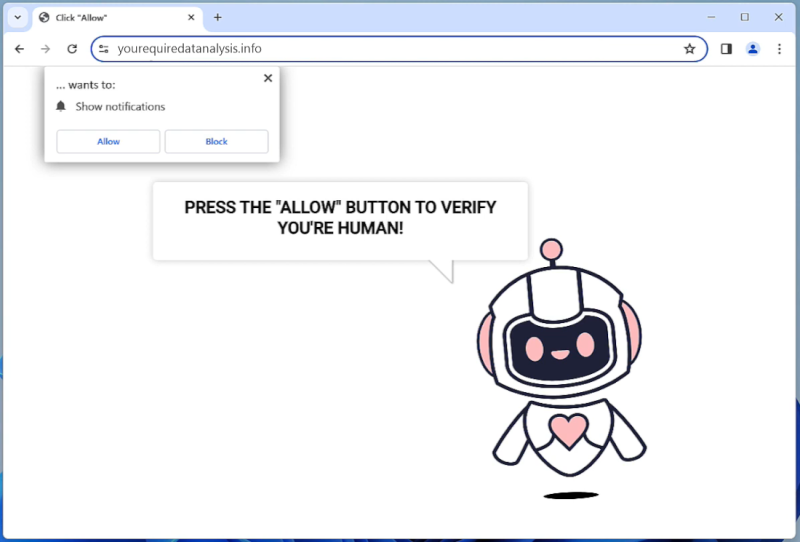
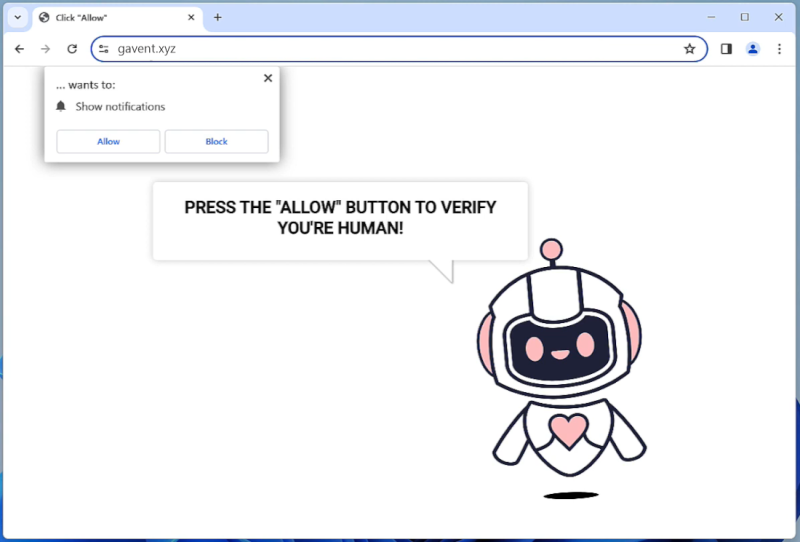
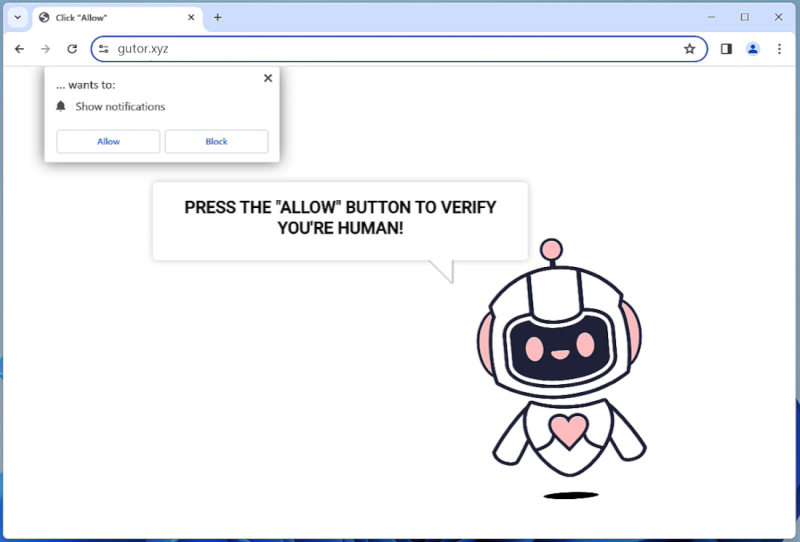
Yourequiredatanalysis.info is a malicious website that is known for infecting computers through various means such as malicious ads, fake software updates, and bundled software downloads. Once a user visits the website, it may prompt them to allow browser notifications, claiming that it is necessary to access the content on the site. However, by allowing these notifications, the user opens the door for the website to bombard them with unwanted pop-up ads and redirect them to other malicious websites.
This website is designed to exploit browser notifications as a way to generate revenue through advertising. By tricking users into allowing notifications, Yourequiredatanalysis.info can display ads directly on the user’s desktop even when the browser is closed. This can be extremely intrusive and annoying for users, and can also lead to further infections as the ads may redirect them to more malicious websites. This malicious website can infect a variety of browsers including Google Chrome, Mozilla Firefox, and Microsoft Edge, as well as various devices such as desktops, laptops, and mobile phones. It is important for users to be cautious when browsing the internet and to avoid clicking on suspicious links or allowing notifications from unfamiliar websites to prevent infections from websites like Yourequiredatanalysis.info.