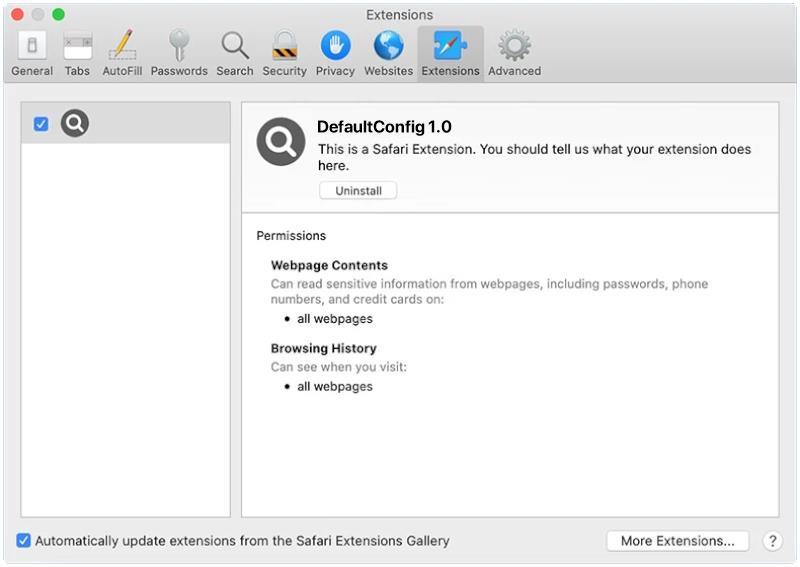
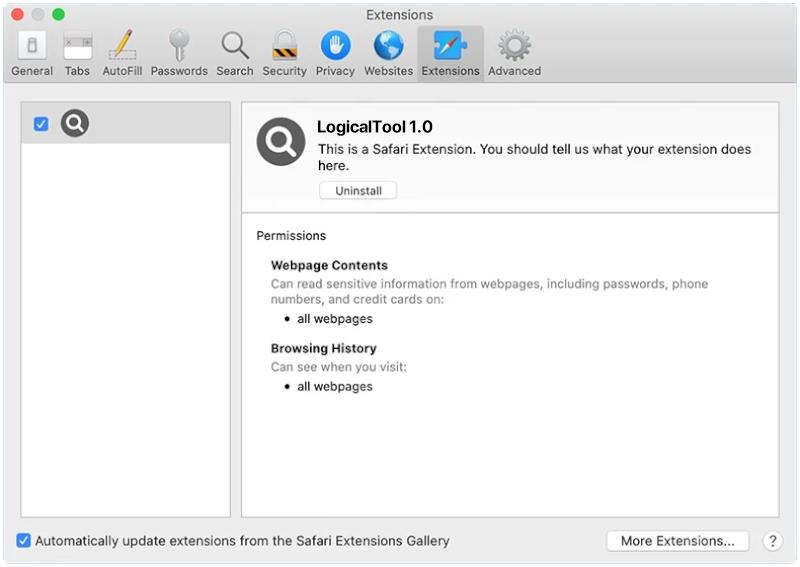
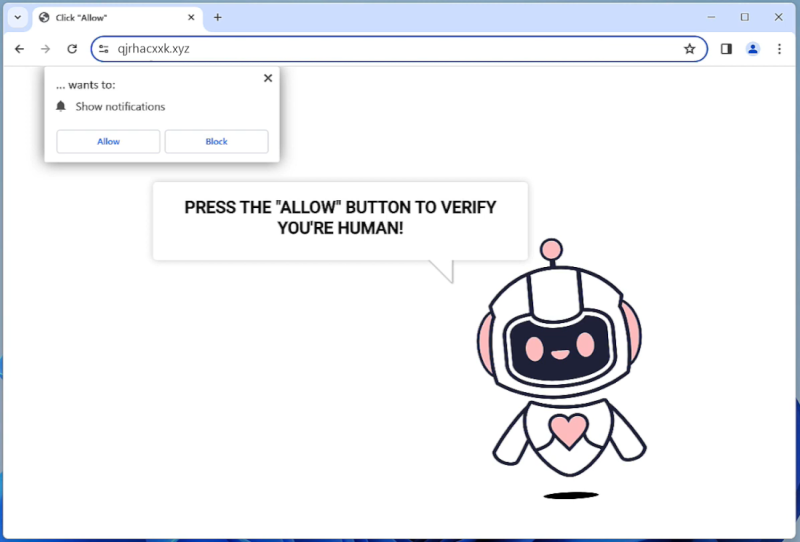
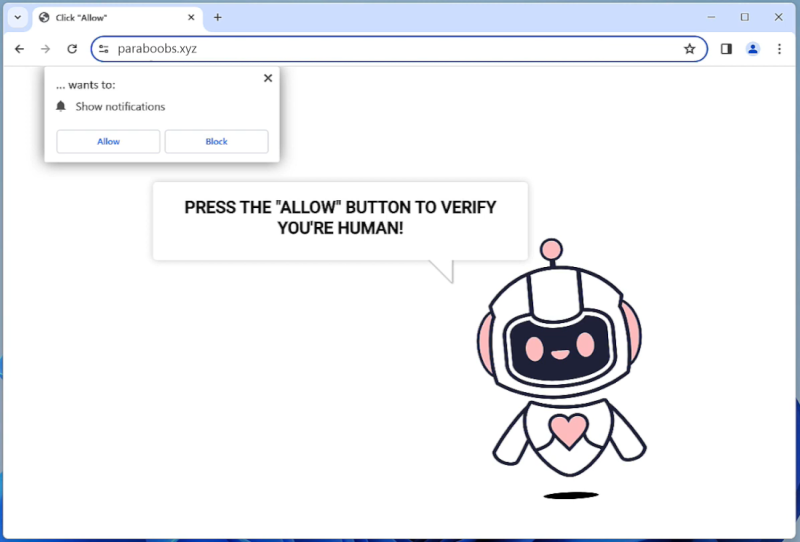
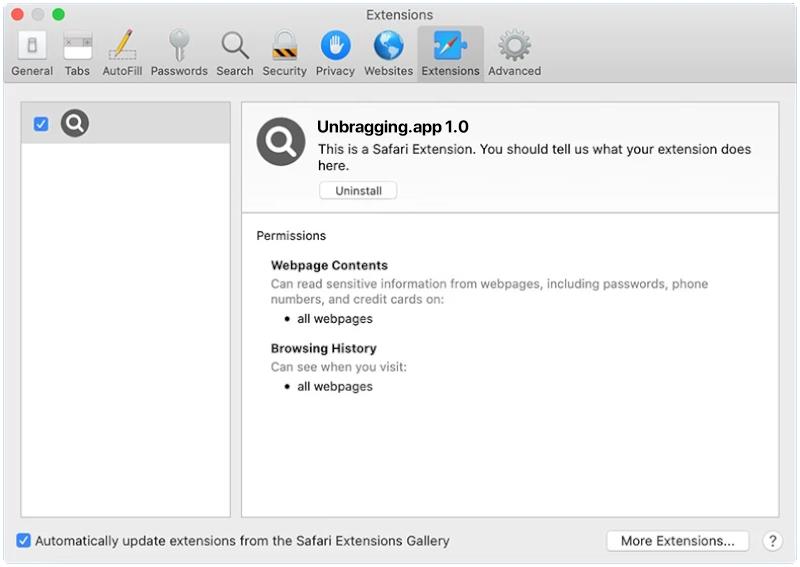
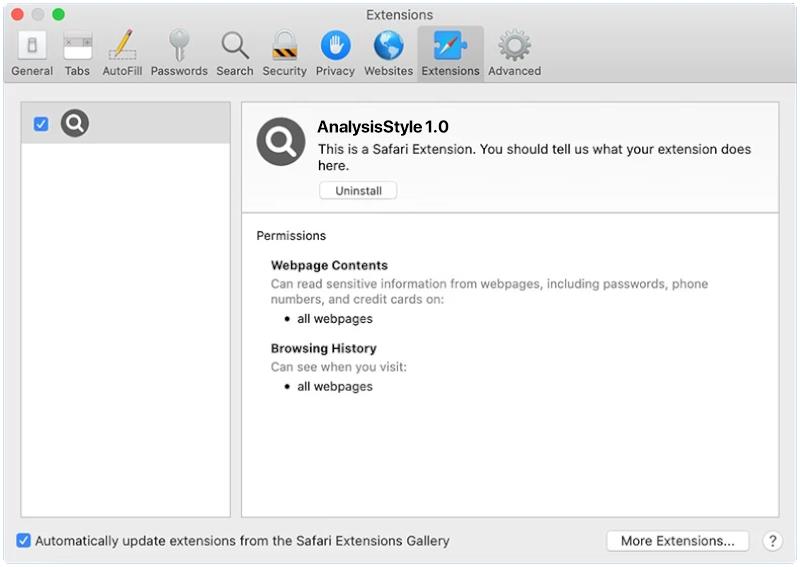
DefaultConfig is a type of malware that specifically targets Mac computers. This malicious software is designed to infect a Mac system and gain unauthorized access to sensitive information, such as personal data, login credentials, and financial information. DefaultConfig can also cause performance issues on the infected device, slowing down its speed and functionality.
DefaultConfig primarily infects Mac computers through phishing emails, malicious websites, or software downloads from untrusted sources. Once the malware is successfully installed on a Mac system, it can start collecting and transmitting personal data to remote servers controlled by cybercriminals. DefaultConfig can also create backdoors in the infected device, allowing hackers to remotely access and control the compromised Mac computer. To protect against DefaultConfig and other malware threats, Mac users should always be cautious when clicking on links or downloading files from unknown sources, and regularly update their security software to detect and remove any potential threats.