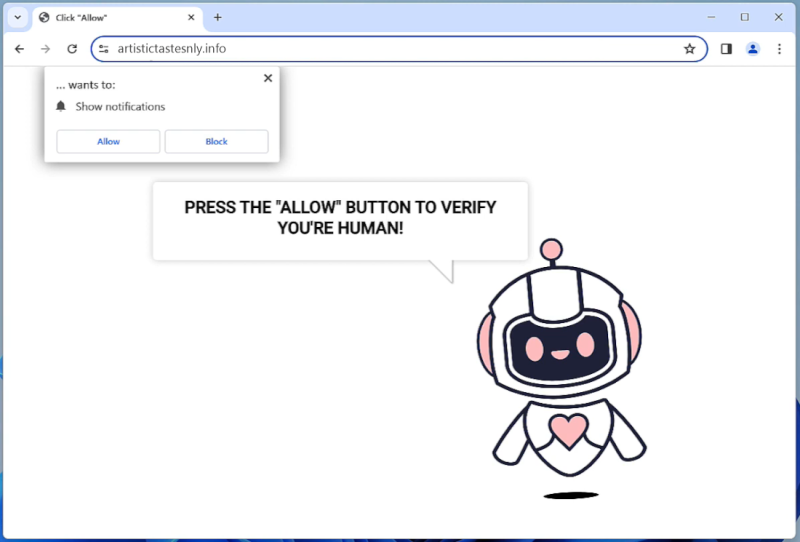
BlackRockFund is a financial institution that offers a wide range of investment products and services to individuals and institutional clients. They provide mutual funds, exchange-traded funds (ETFs), and other investment options to help clients achieve their financial goals. BlackRockFund is known for its expertise in investment management and its commitment to helping clients build and protect their wealth.
BlackRockFund may appear in browsers as a result of targeted advertising or marketing efforts by the company. They may use online advertising to promote their products and services to potential clients who are searching for investment options. Additionally, individuals who have visited the BlackRockFund website or expressed interest in their offerings may see targeted ads when browsing the internet.