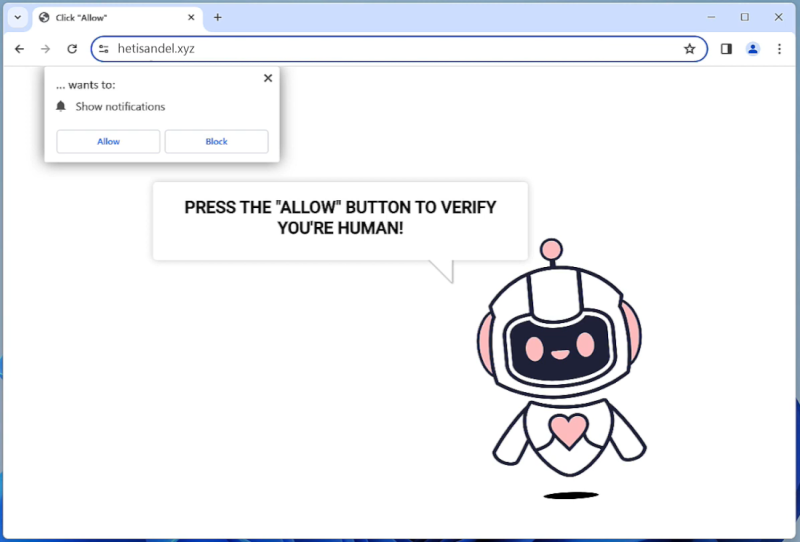
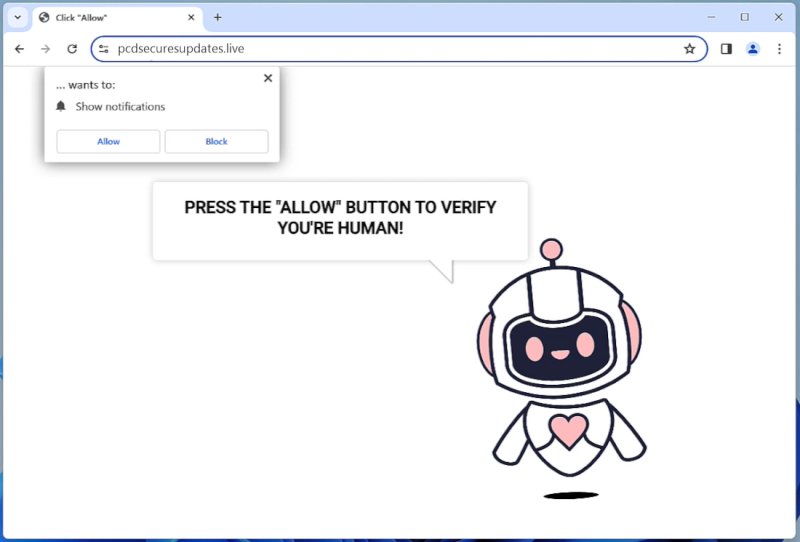
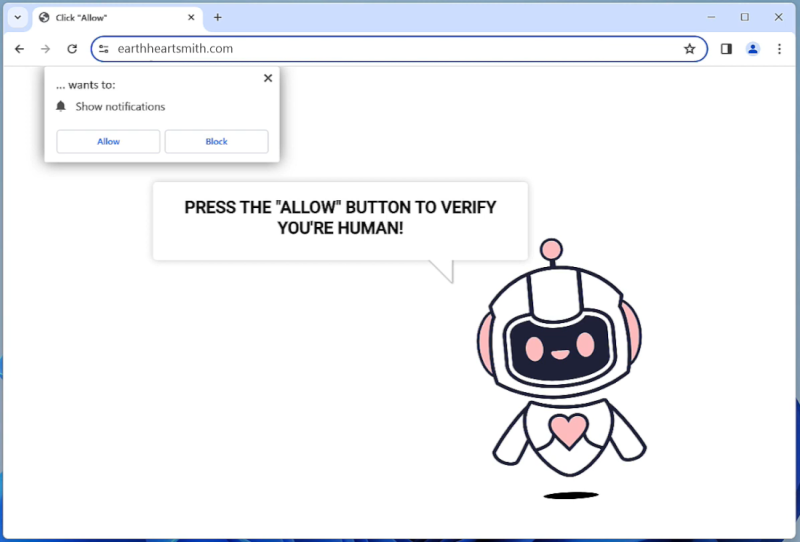
Hetisandel.xyz is a malicious website that often infects computers through deceptive pop-up ads or by bundling itself with free software downloads. Once a user visits the site, they may be prompted to allow browser notifications, which can then be used to display unwanted advertisements or redirect the user to other malicious websites. This type of tactic is commonly used to generate revenue through ad clicks or to gather personal information from unsuspecting users.
Hetisandel.xyz primarily targets desktop browsers such as Google Chrome, Mozilla Firefox, and Microsoft Edge, but it can also affect mobile browsers on devices such as smartphones and tablets. The website may exploit vulnerabilities in the browser or operating system to gain access to the device and display intrusive notifications. Users are advised to be cautious when visiting unfamiliar websites and to avoid clicking on pop-up ads or allowing notifications from suspicious sources to help prevent infection from malicious sites like Hetisandel.xyz.