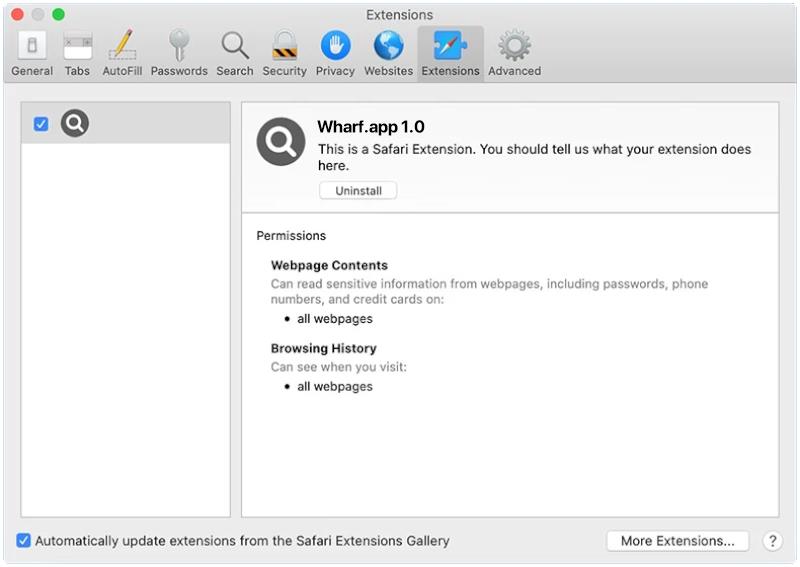
Wharf.app is a potentially unwanted application (PUA) that is known to infect Mac computers. It is categorized as adware, which means it displays unwanted advertisements and pop-ups to generate revenue for its creators. Wharf.app can get installed on a Mac system through various methods, such as software bundling, malicious websites, or fake software updates.
Once Wharf.app infects a Mac, it may start displaying intrusive advertisements, redirecting web searches, and causing browser slowdowns. It can also track the user’s online activities and collect personal information for targeted advertising. Additionally, Wharf.app may make changes to the system settings and preferences without the user’s consent, making it difficult to remove the adware completely. Users should be cautious when downloading software from unknown sources and regularly update their security software to prevent infections like Wharf.app from infiltrating their Mac systems.