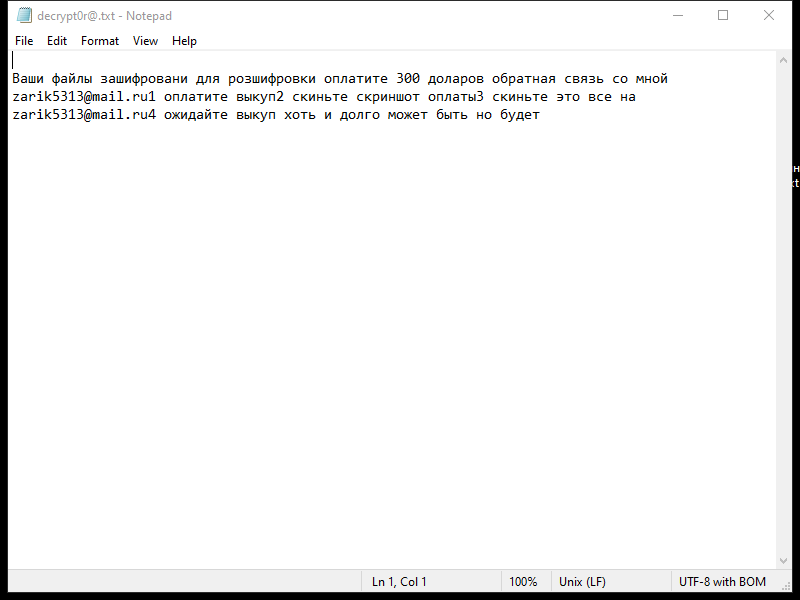
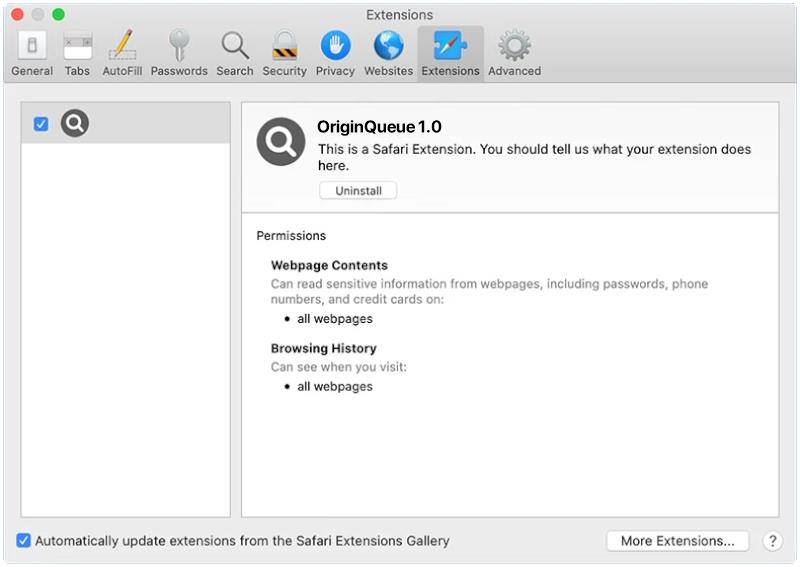
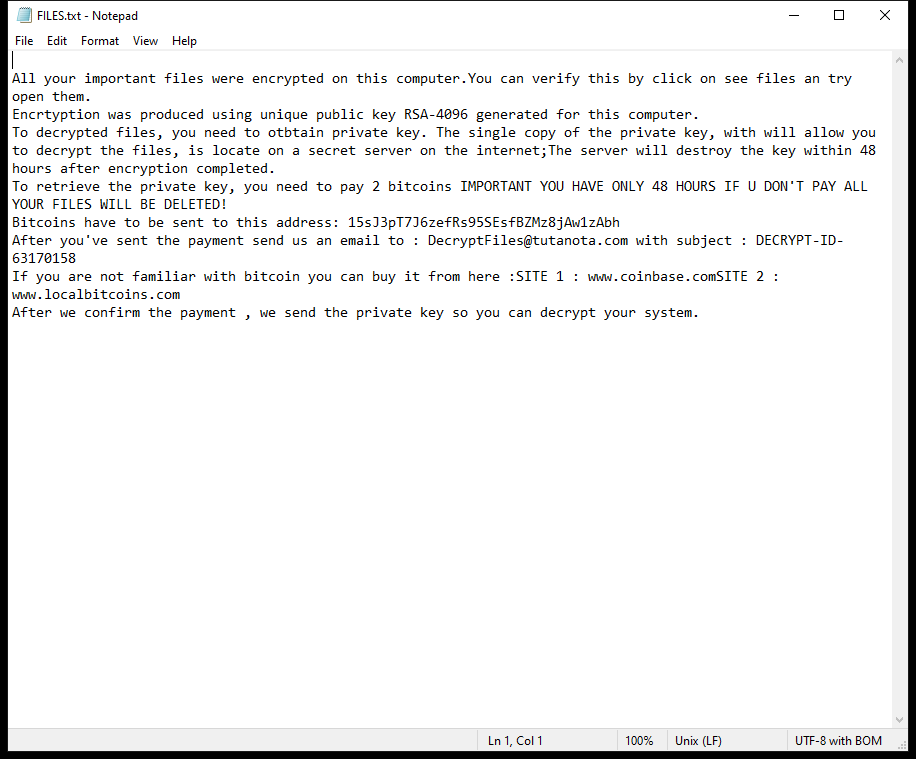
Planet is a type of malware, specifically a trojan horse, that infects computers and allows attackers to gain unauthorized access to the infected system. Once a computer is infected with Planet, the malware can steal sensitive information, monitor user activity, and potentially allow for remote control of the infected computer.
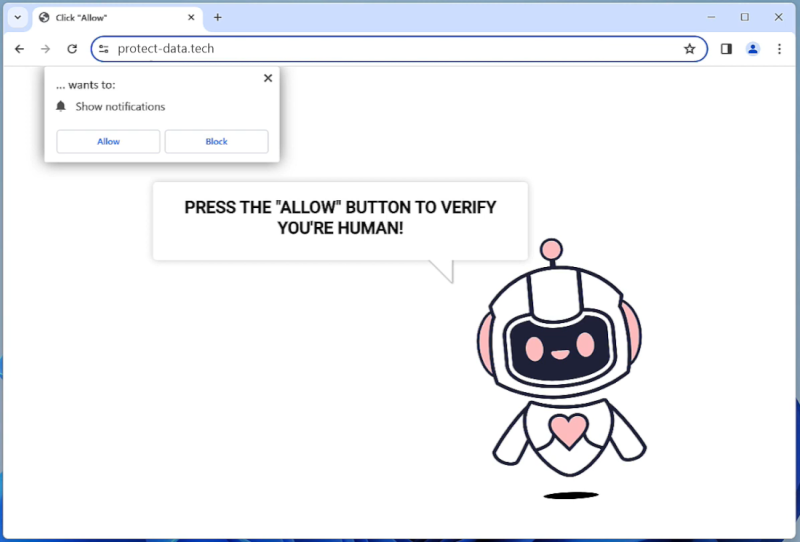
Planet typically infects computers through malicious email attachments, fake software downloads, or through vulnerabilities in outdated software. Once the malware is installed on a computer, it can spread to other systems on the same network and potentially cause widespread damage.
To protect against Planet and other malware infections, it is important to regularly update software, use strong passwords, and be cautious when opening email attachments or downloading software from unknown sources. Additionally, using reputable antivirus software can help detect and remove malware infections before they can cause harm.