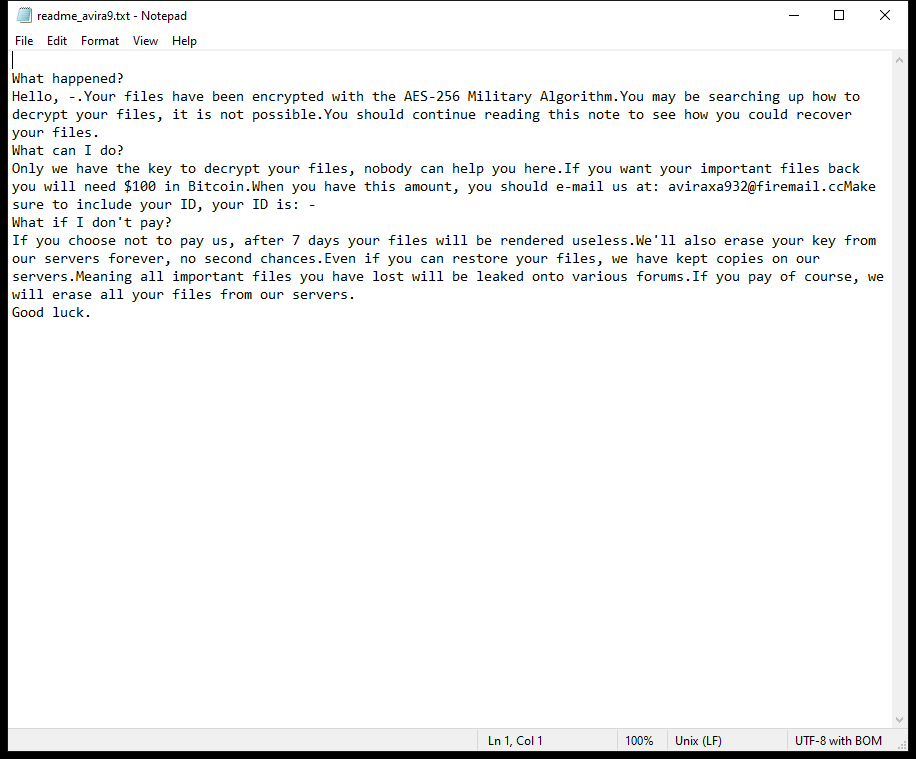
Backdoor:Win32/Drateam.B is a type of malware categorized as a backdoor Trojan. This malicious software is designed to provide unauthorized access to a computer system, allowing cybercriminals to remotely control the infected machine and carry out various malicious activities.
Backdoor:Win32/Drateam.B can infect computers through various methods, including:
1. Phishing emails: Cybercriminals may send phishing emails containing malicious attachments or links that, when clicked, download and execute the backdoor Trojan onto the victim’s computer.
2. Drive-by downloads: Backdoor:Win32/Drateam.B can also be installed through drive-by downloads, where malware is automatically downloaded and installed when a user visits a compromised or malicious website.
3. Exploiting vulnerabilities: The backdoor Trojan may exploit security vulnerabilities in software or operating systems to gain access to the computer system.
4. Social engineering: Cybercriminals may use social engineering tactics to trick users into downloading and installing the malware by disguising it as legitimate software or files.
Once installed, Backdoor:Win32/Drateam.B can perform various malicious activities, such as stealing sensitive information, monitoring user activities, downloading additional malware, and initiating denial of service attacks. It is important for users to have up-to-date security software and practice safe browsing habits to protect against such threats.