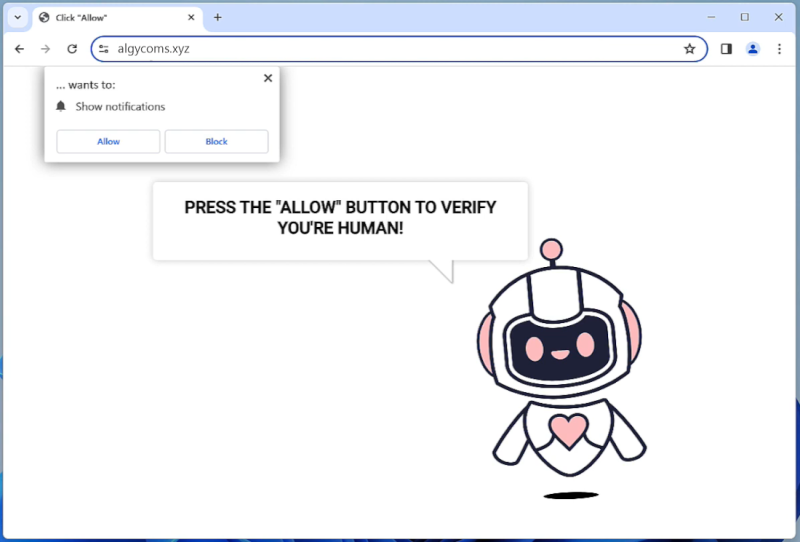
My Text Case is a type of adware that infects computers and web browsers by displaying intrusive advertisements and pop-ups on the user’s screen. This adware is often bundled with free software downloads and can be unknowingly installed on a user’s computer when they download and install other programs. Once installed, My Text Case will start displaying ads in the form of banners, pop-ups, or in-text links, disrupting the user’s browsing experience.
My Text Case adware can also track the user’s online activity and collect personal information such as browsing history, search queries, and login credentials. This information is then used to display targeted ads to the user and potentially sold to third-party advertisers. Additionally, My Text Case can slow down the computer’s performance and cause browser crashes. It is important for users to regularly scan their computer for adware and malware to prevent infections like My Text Case from compromising their online security and privacy.