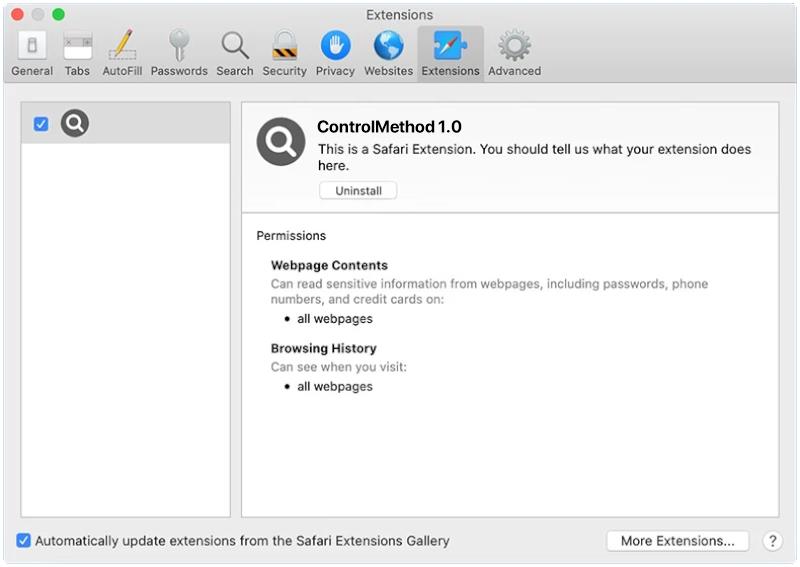
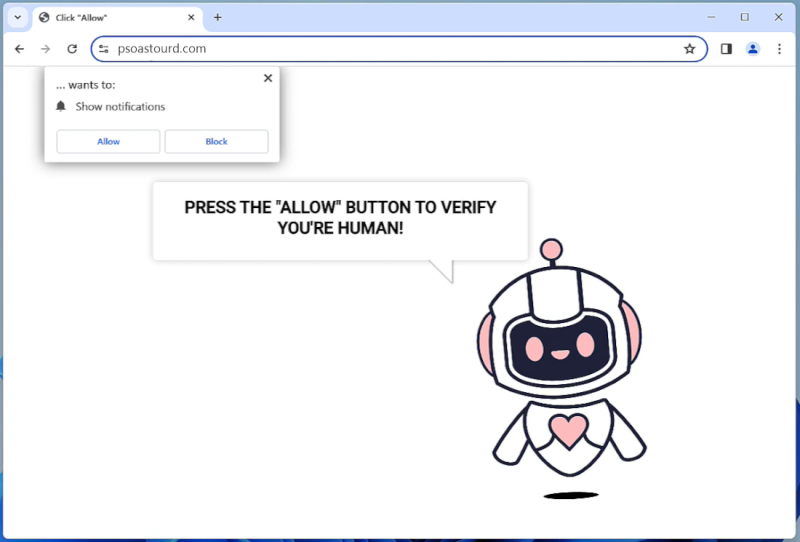
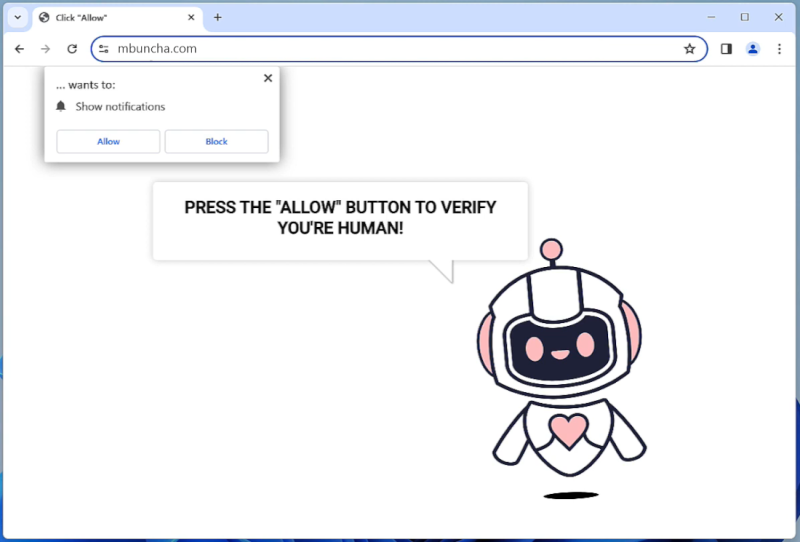
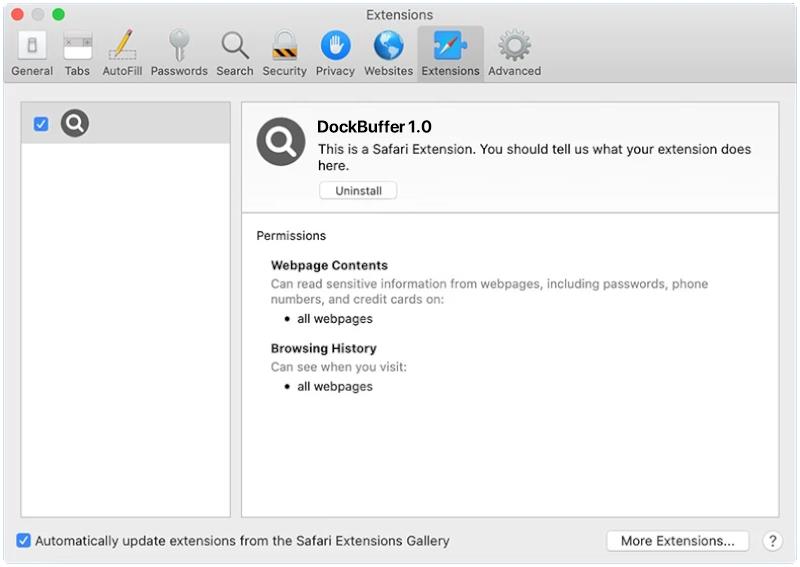
ControlMethod is a type of malware that infects Mac computers by exploiting vulnerabilities in the operating system or through social engineering tactics. Once installed on a system, ControlMethod has the ability to remotely control the infected computer, steal sensitive information, and perform malicious activities without the user’s knowledge or consent.
ControlMethod can infect a Mac computer through various means, such as phishing emails, malicious websites, or fake software downloads. Once the malware is installed, it can remain hidden on the system and evade detection by security software. ControlMethod can also spread to other devices on the same network, making it a dangerous threat to both individual users and organizations. It is important for Mac users to stay vigilant and ensure their systems are protected with up-to-date security software to prevent infections from malware like ControlMethod.