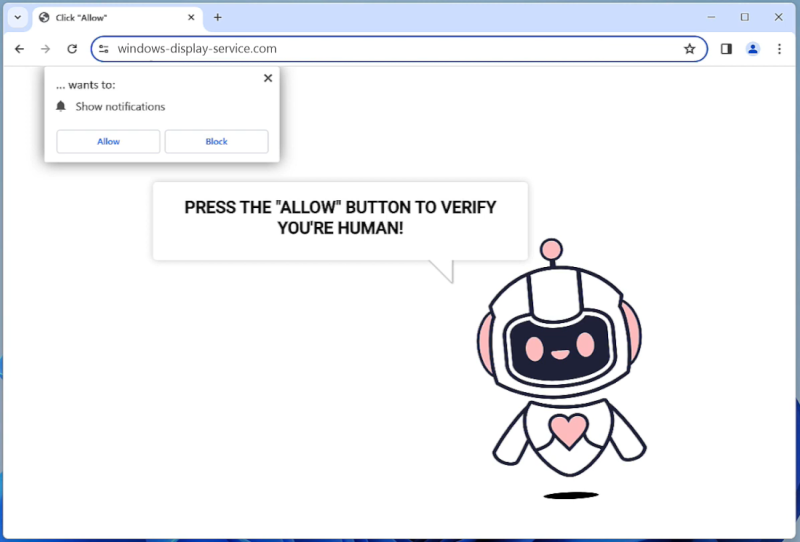
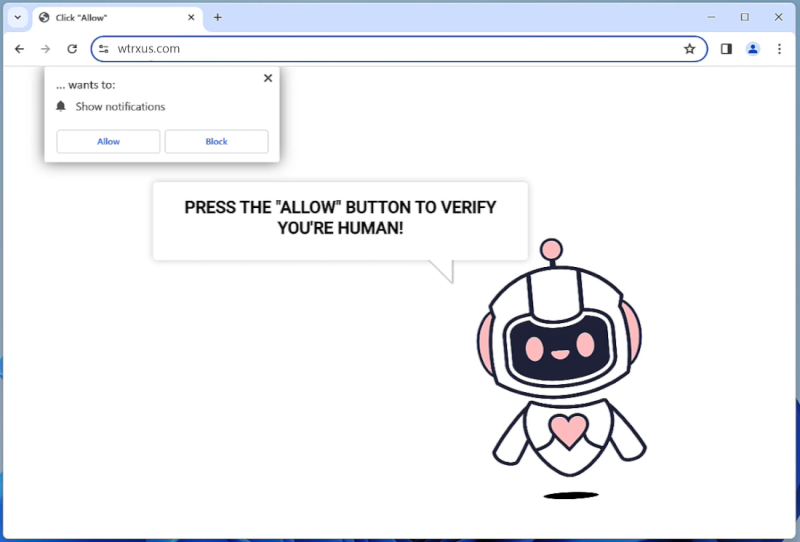
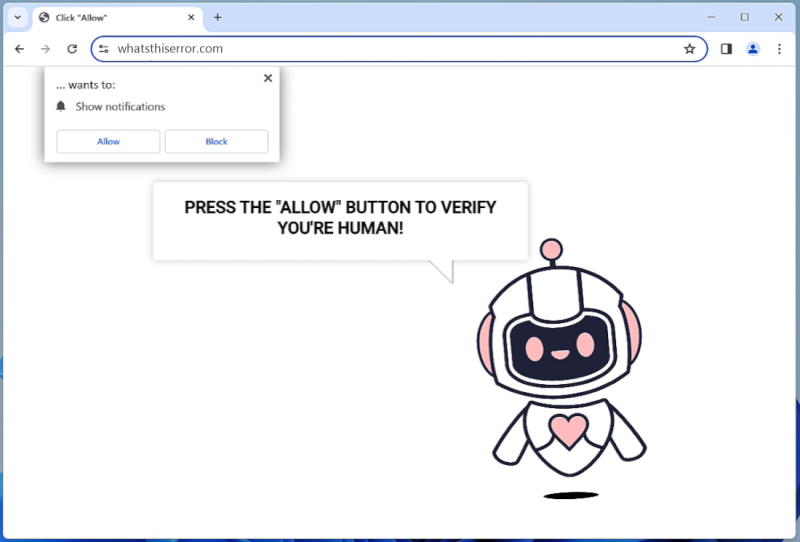
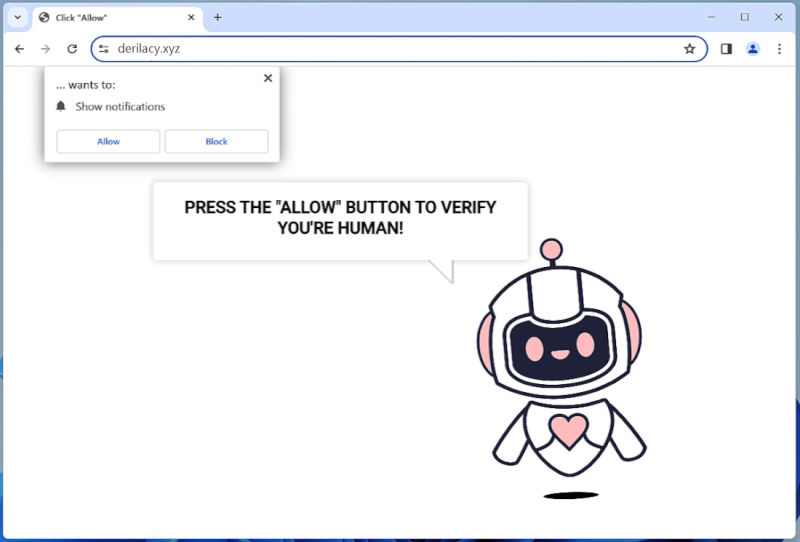
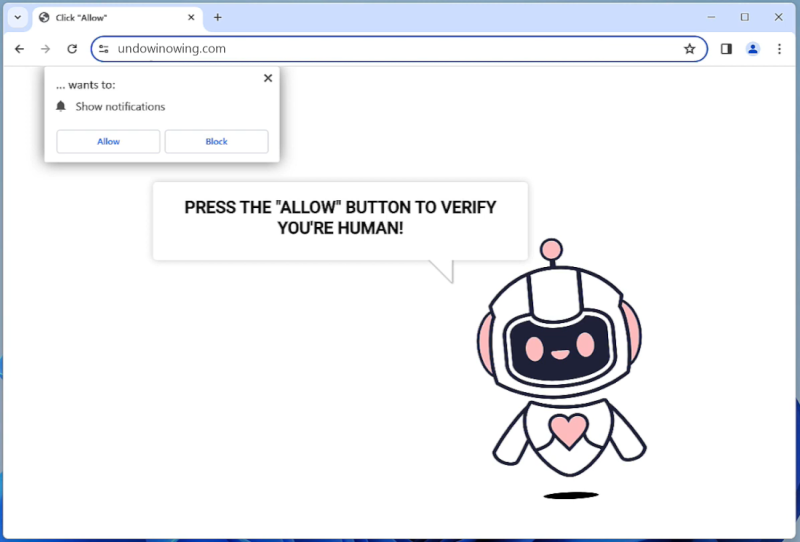
Windows-display-service.com is a malicious website that tricks users into allowing browser notifications, which are then used to display unwanted advertisements and redirect users to potentially harmful websites. This type of malware typically infects computers through deceptive tactics, such as fake software updates, spam emails, or malicious downloads. Once a user visits the infected website and agrees to receive notifications, the malware gains access to the browser and starts displaying intrusive pop-ups and ads.
Windows-display-service.com exploits browser notifications by using them to push out unwanted advertisements, fake alerts, and other malicious content to users. These notifications can appear even when the browser is closed, making it difficult for users to get rid of the malware. The website may also track users’ browsing habits and collect personal information, which can then be used for targeted advertising or sold to third parties. Windows-display-service.com can infect a variety of browsers, including Chrome, Firefox, and Safari, and can affect both desktop and mobile devices. Users are advised to be cautious when visiting unfamiliar websites and to avoid clicking on suspicious links or agreeing to receive notifications from unknown sources to prevent infection by this type of malware.