Title: Understanding Y-Cleaner: Its Nature and Impact on Computer Systems
Introduction:
In an age where computer security has become a paramount concern, it is essential to shed light on various malware threats that can compromise the integrity and functionality of our digital devices. One such notorious malware is Y-Cleaner. This article aims to provide an insight into what Y-Cleaner is, how it infects computers, and the potential risks associated with this malicious software.
Y-Cleaner: An Overview
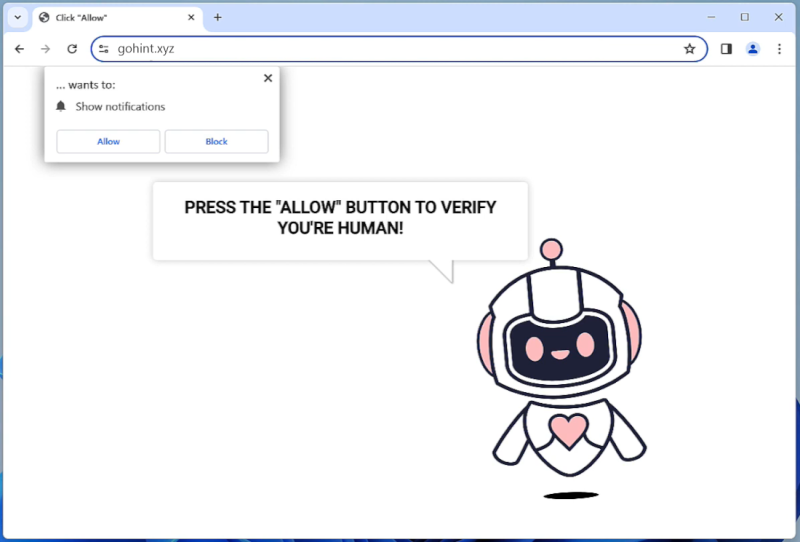
Y-Cleaner is classified as a potentially unwanted program (PUP), specifically categorized as a rogue system cleaner. It claims to optimize the performance of computers by removing unnecessary files, junk data, and unwanted applications. At first glance, this may seem like a legitimate utility; however, Y-Cleaner often employs deceptive tactics to trick users into installing it.
Infection Methods:
Y-Cleaner typically infects computers through deceptive distribution techniques, including software bundling and misleading advertisements. It commonly piggybacks on freeware or shareware applications that users download from unofficial or unreliable sources. When users install these bundled applications without carefully reviewing the installation process, Y-Cleaner secretly installs itself alongside the desired software.
Upon successful installation, Y-Cleaner starts executing its malicious activities. It may initiate a system scan that falsely identifies numerous issues, such as unnecessary files, registry errors, or malware infections. These false positives aim to create a sense of urgency and convince users to purchase the full version of Y-Cleaner to resolve the alleged problems. However, the promised optimization and cleaning capabilities are often ineffective or even non-existent.
Risks and Impact:
Although Y-Cleaner may claim to improve system performance, its actual impact is quite the opposite. Instead of optimizing the computer, it may lead to a range of adverse consequences. Firstly, Y-Cleaner can consume system resources, causing computers to slow down significantly. Additionally, it may display intrusive pop-up ads, redirect users to malicious websites, or track their online activities, jeopardizing privacy and security. Users who fall victim to Y-Cleaner’s deceptive tactics may also face financial losses if they purchase the full version, which is essentially a scam.
Conclusion:
In conclusion, Y-Cleaner is a potentially unwanted program that disguises itself as a system cleaner while employing deceptive tactics to infect computers. By understanding the nature and impact of Y-Cleaner, users can be better equipped to identify and protect themselves against this malware threat. It is crucial to exercise caution when downloading software from untrusted sources and to regularly update and use reliable anti-malware software to detect and remove such threats promptly.



![How to remove Win32:Ransomx-Gen [Ransom]](https://malwarewarrior.com/wp-content/uploads/2024/02/win32-ransomx-gen-ransom--1170x669.png)