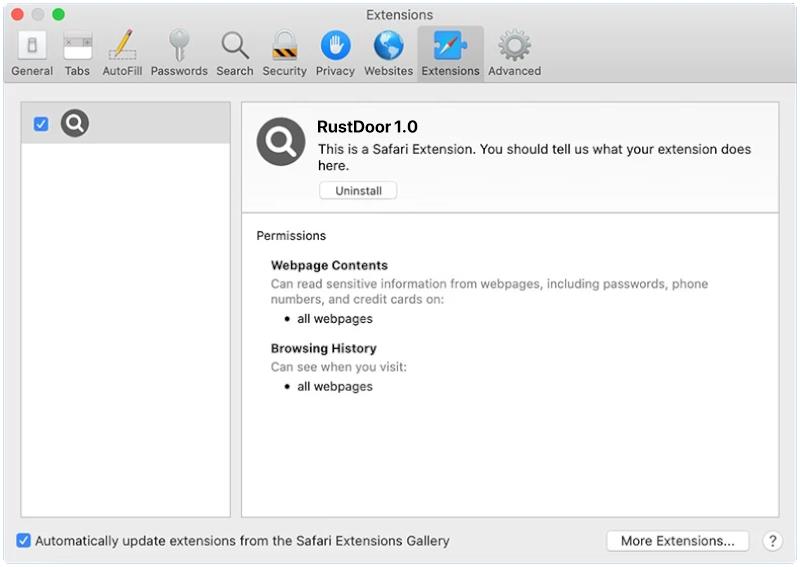
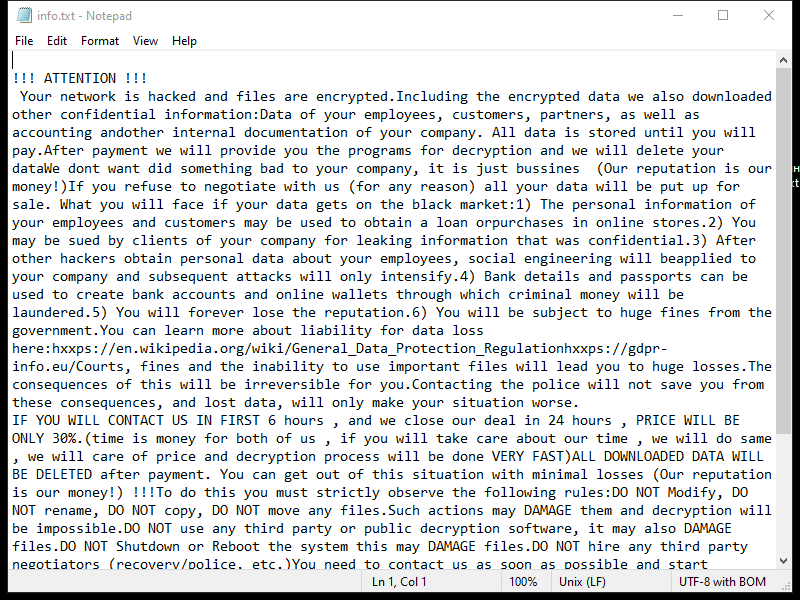
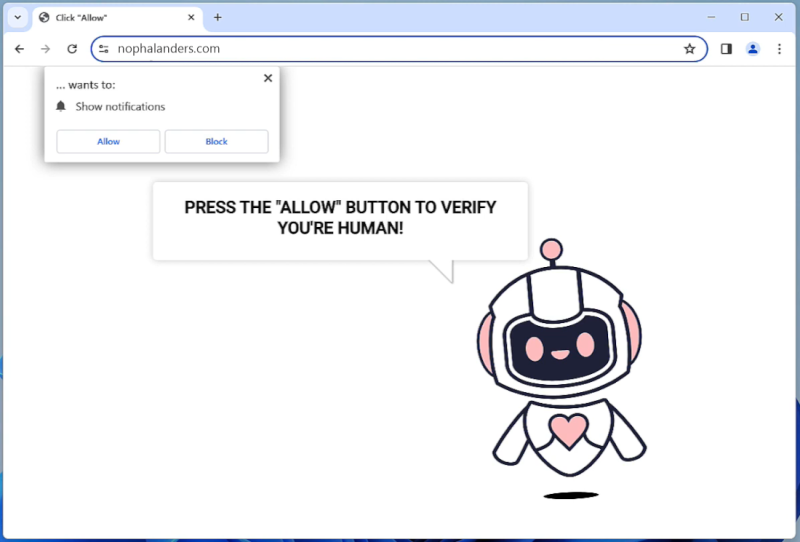
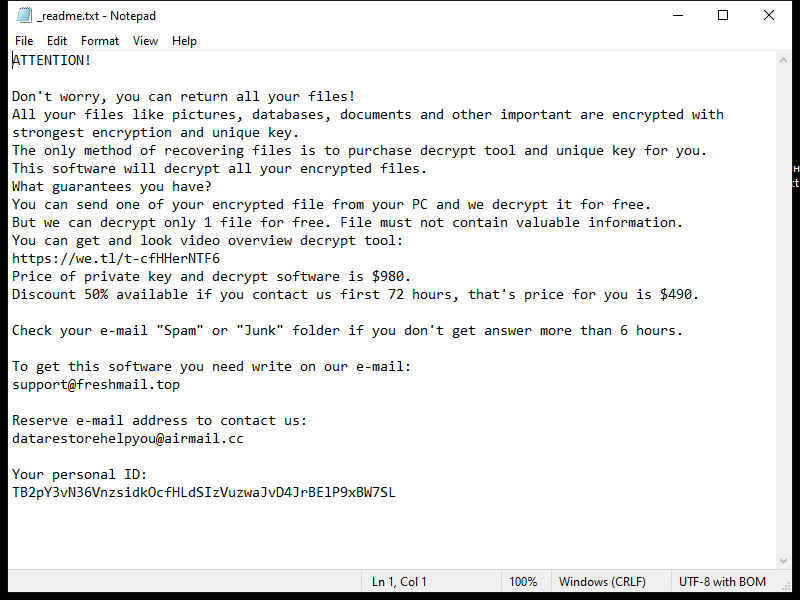
RustDoor is a type of malware that specifically targets Mac operating systems. It is a trojan horse that is designed to gain unauthorized access to a user’s computer and steal sensitive information. Once it infects a Mac, RustDoor establishes a backdoor, allowing remote attackers to control the compromised system and extract data without the user’s knowledge or consent.
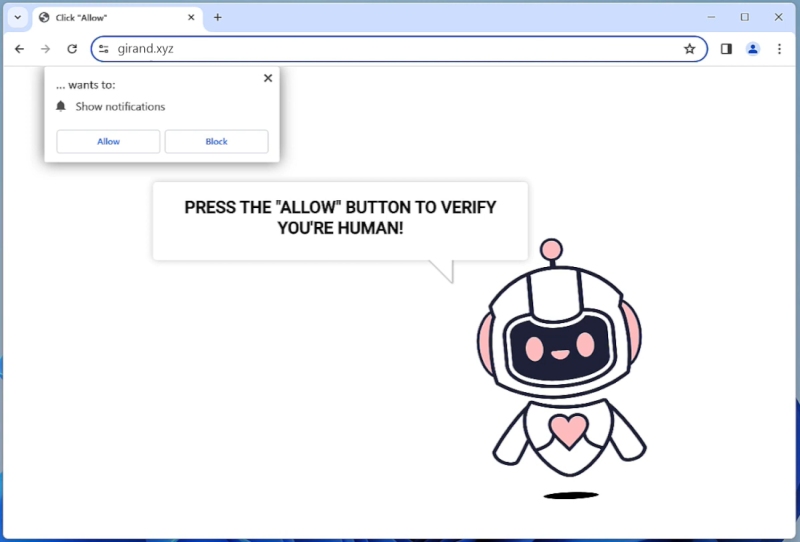
The infection process of RustDoor on Mac involves various techniques. It often exploits vulnerabilities in the operating system or applications installed on the computer. These vulnerabilities can be present in outdated software or through malicious files downloaded from untrusted sources. RustDoor may also spread through email attachments, software cracks, or fake software updates, tricking users into executing the malware unknowingly. Once inside the system, RustDoor starts collecting information such as login credentials, financial data, and other personal information, which can be used for identity theft or other malicious purposes. It operates silently in the background, making it difficult for users to detect its presence until the damage is done.