Importantpurchase.click is a malicious website that is known for its intrusive and deceptive behavior. It typically infects computers through various methods such as drive-by downloads, malicious email attachments, fake software updates, or bundled with other software downloads. Once a user visits or interacts with a compromised website or downloads infected content, the malware associated with Importantpurchase.click can be installed without the user’s knowledge or consent.
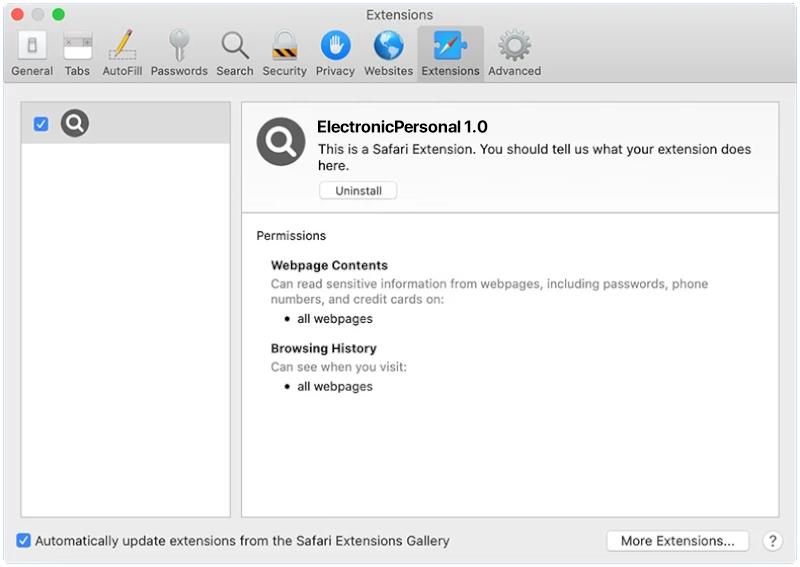
Once the computer is infected, Importantpurchase.click exploits browser notifications to further its malicious activities. It tricks users into allowing the website to send push notifications to their browsers. These notifications are then used to display intrusive advertisements, redirect users to other malicious websites, or prompt them to download additional malware disguised as legitimate software. This deceptive technique not only compromises the user’s browsing experience but also exposes them to potentially harmful content and poses a risk to their online privacy and security.
Importantpurchase.click can infect various browsers, including popular ones such as Google Chrome, Mozilla Firefox, Microsoft Edge, and Safari. It can also target different operating systems like Windows, macOS, Linux, and Android devices. This wide range of compatibility allows the malware to target a large number of users across different platforms, increasing its potential impact and reach. It is crucial for users to stay vigilant, keep their browsers and operating systems up to date, and employ reliable security software to protect themselves from such malicious websites and prevent their devices from getting infected.