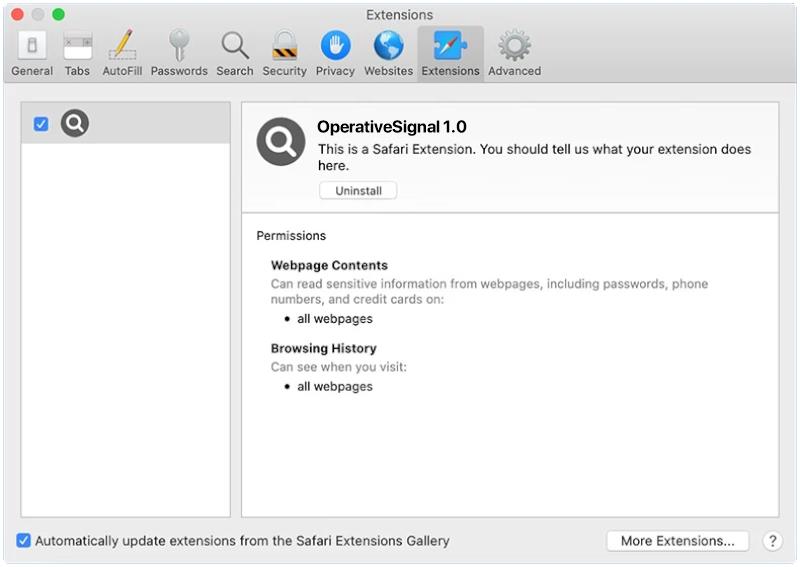
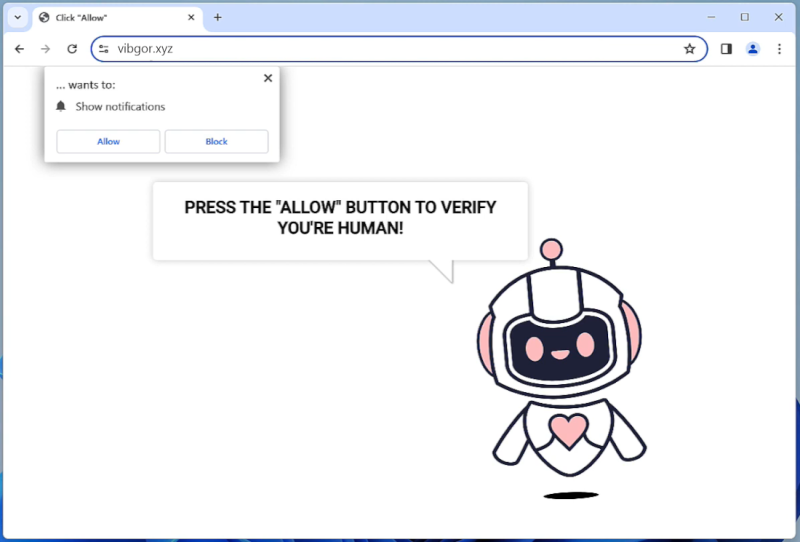
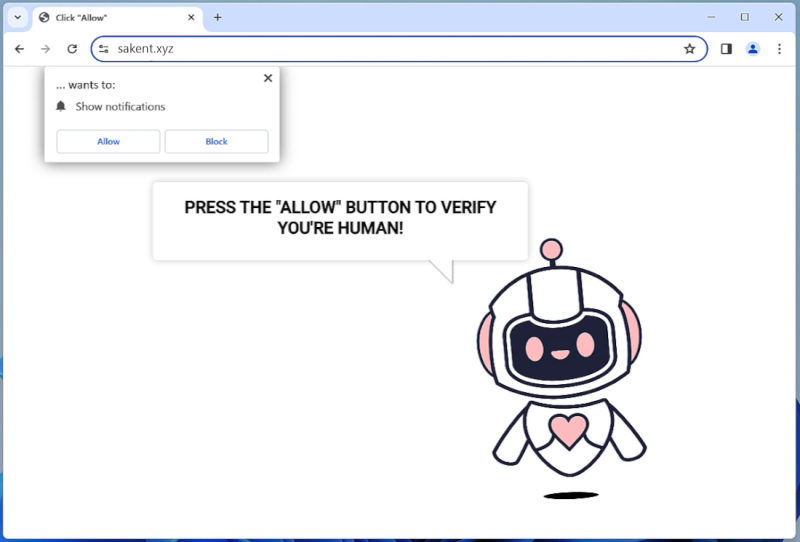
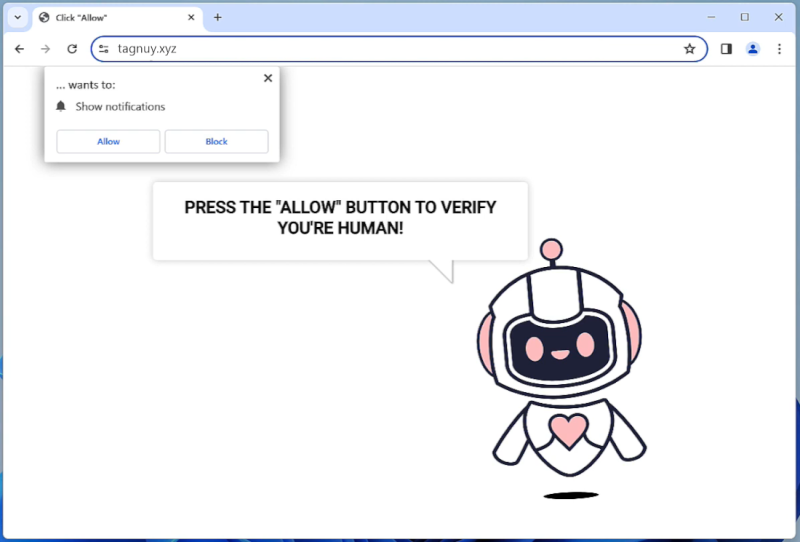
OperativeSignal is a type of malware that specifically targets Mac operating systems. It is a sophisticated and stealthy malware that infects Mac computers, compromising their security and potentially gaining unauthorized access to sensitive information. OperativeSignal is designed to operate silently in the background, making it difficult for users to detect its presence.
Once a Mac is infected with OperativeSignal, it can perform various malicious activities. This malware typically installs keyloggers, which record every keystroke made by the user. This allows the attackers to capture sensitive information such as login credentials, credit card details, or personal information. OperativeSignal may also enable remote access to the infected Mac, allowing the attackers to take control of the system and perform unauthorized actions. It is important for Mac users to regularly update their security software and exercise caution when downloading files or visiting suspicious websites to prevent being infected by OperativeSignal or similar malware.