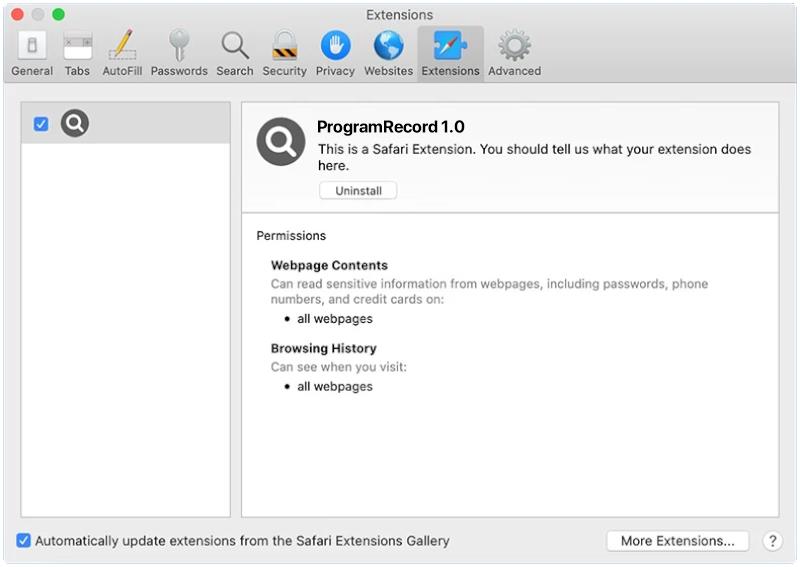
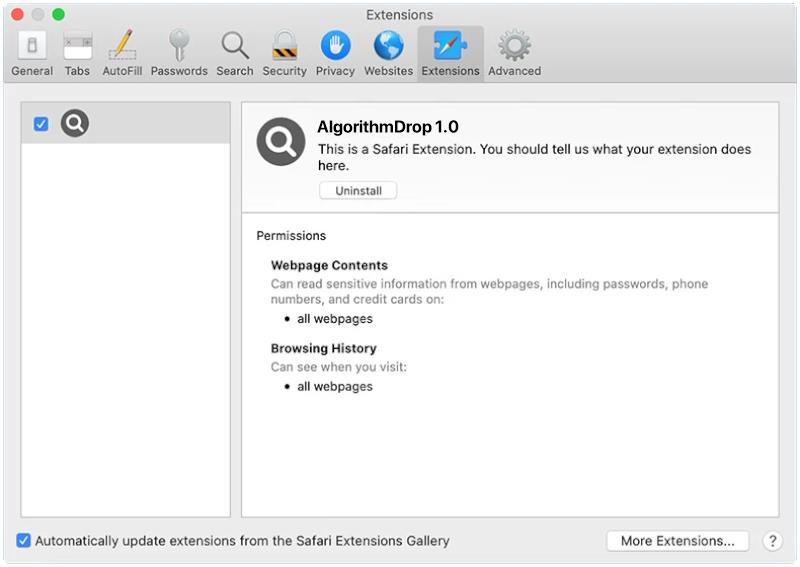
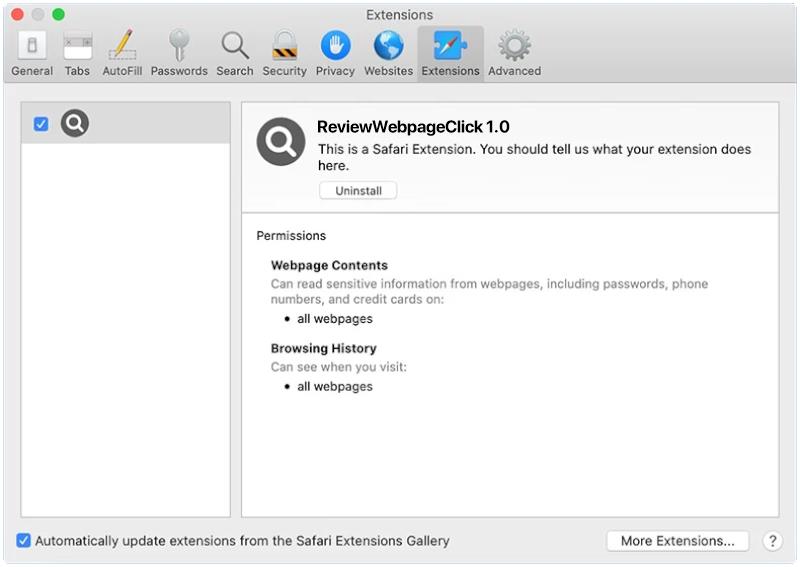
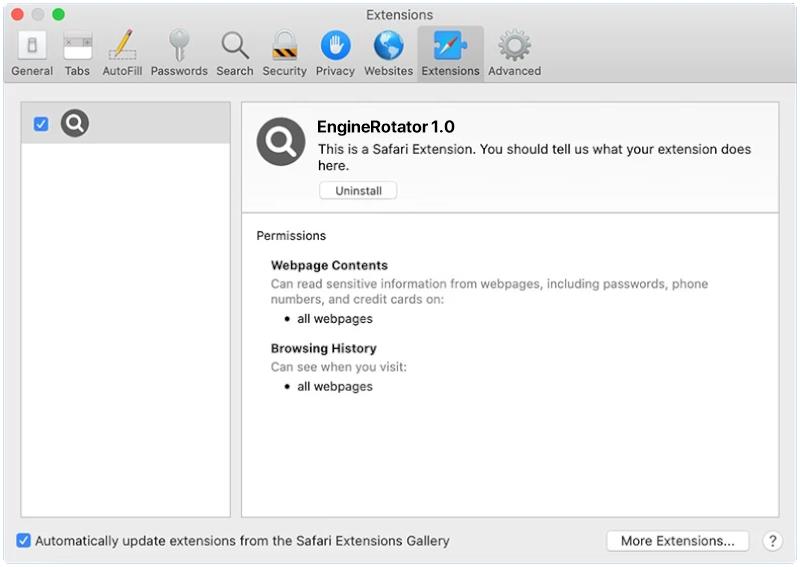
ProgramRecord is a type of malware that specifically targets Mac computers. It is a malicious program that infiltrates Mac systems and performs various malicious activities without the knowledge or consent of the user. ProgramRecord is designed to gather sensitive information, such as login credentials, banking details, and personal data, which can then be exploited for financial gain or other malicious purposes.
When ProgramRecord infects a Mac computer, it often disguises itself as a legitimate software or application, tricking users into downloading and installing it. It commonly spreads through malicious websites, email attachments, or software bundles that users download from untrusted sources. Once installed, ProgramRecord starts running in the background, silently collecting data and sending it to the attacker’s servers. The malware may also modify system settings, inject malicious code into legitimate processes, or create new files and folders to maintain its persistence on the infected system.
To protect against ProgramRecord and similar malware, it is crucial to practice safe browsing habits and avoid downloading software from questionable sources. Regularly updating the operating system and installed applications can also help mitigate the risk of infection. Additionally, installing a reliable antivirus or anti-malware program can provide an extra layer of defense against ProgramRecord and other types of malware.