WeTransfer is a file-sharing service that allows users to send large files over the internet. It provides a simple and user-friendly interface, making it convenient for individuals and businesses to transfer files securely. WeTransfer offers both free and paid versions of its service, with additional features and benefits available to paid subscribers.
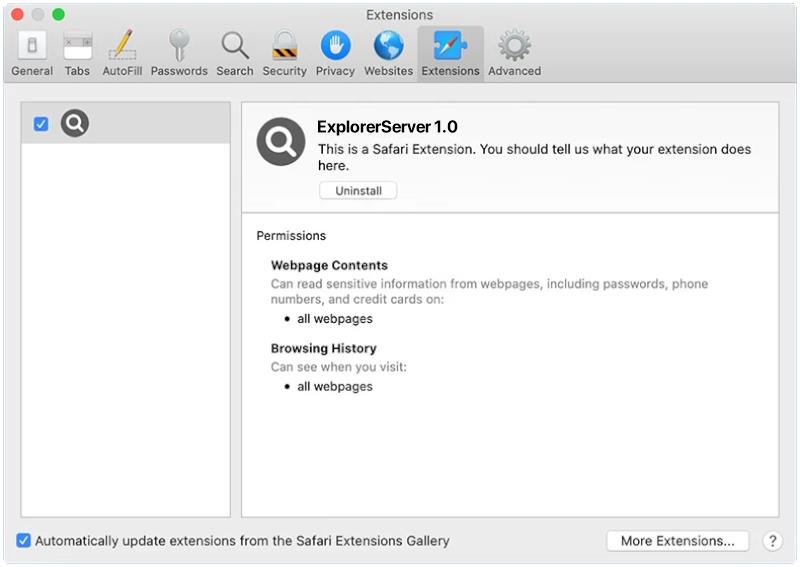
When WeTransfer – Order Specifications appears in browsers, it typically refers to a specific order or request made by a user on the WeTransfer platform. This could involve specifying certain preferences or requirements for the file transfer, such as setting an expiration date for the shared files, adding password protection, or requesting a notification when the recipient downloads the files. These order specifications ensure that the file transfer process meets the user’s needs and provides them with the necessary controls over their shared content. WeTransfer – Order Specifications appearing in browsers simply indicates that the user is customizing their file transfer process using the WeTransfer service.