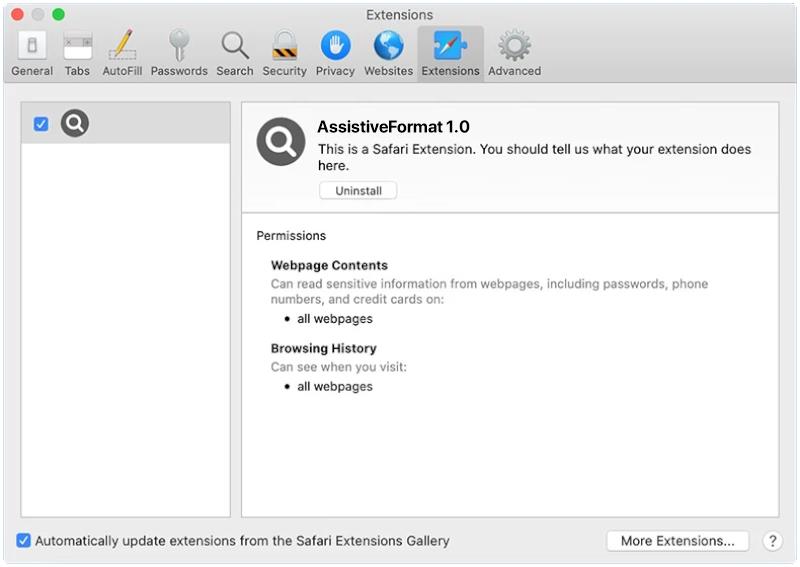
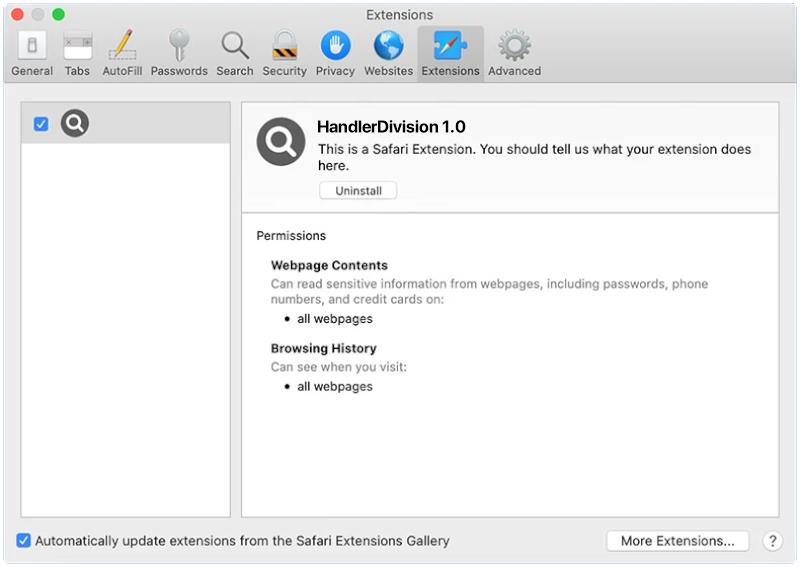
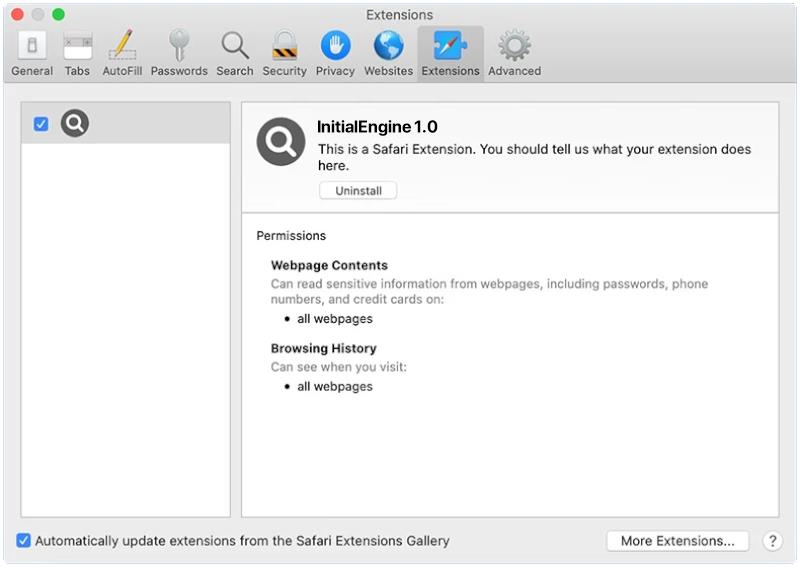
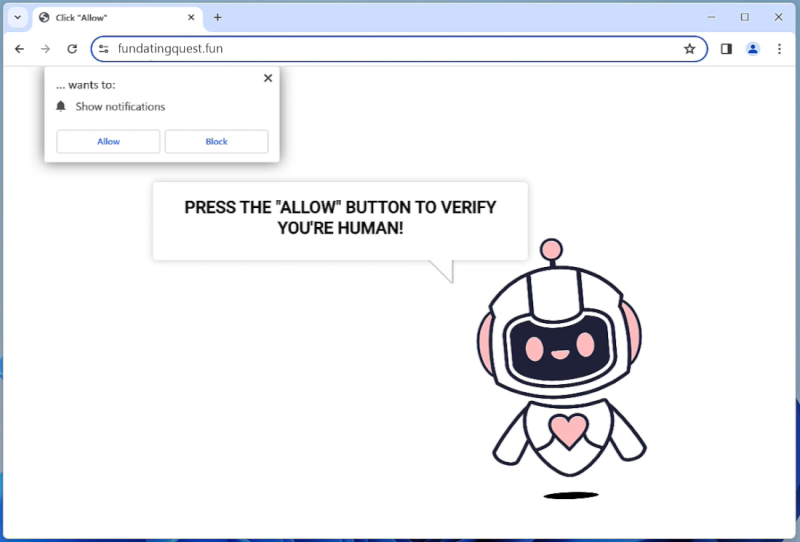
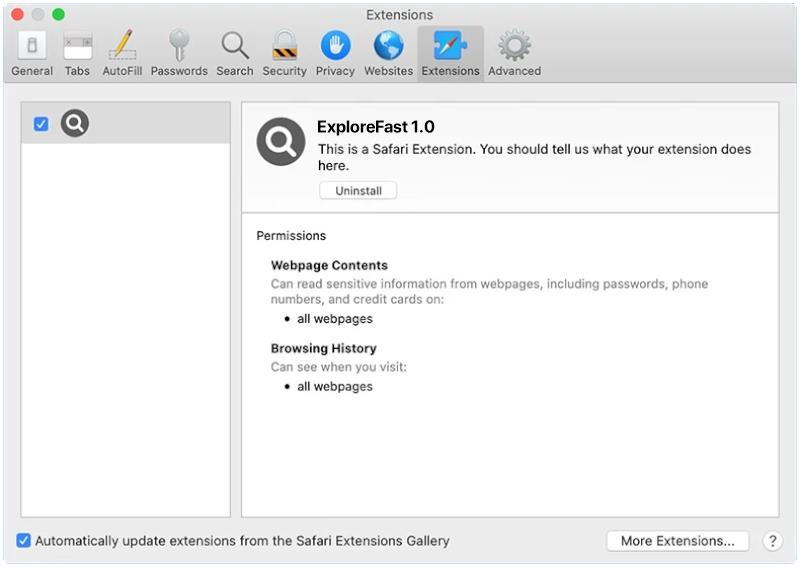
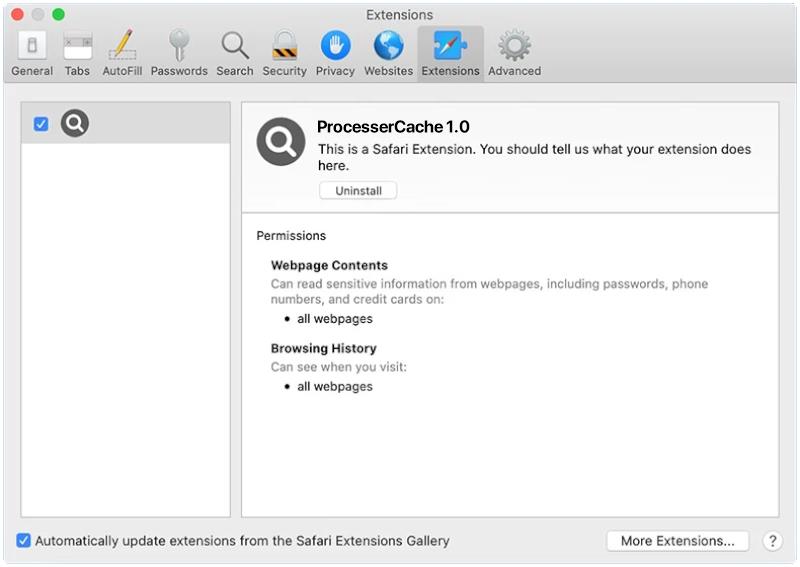
AssistiveFormat is a type of malware that specifically targets Mac computers. It is a form of adware that infects the system and displays intrusive advertisements, redirects webpages, and collects user data for malicious purposes. AssistiveFormat typically spreads through deceptive techniques such as bundled software installers, fake software updates, or malicious email attachments.
Once installed on a Mac, AssistiveFormat modifies the browser settings, injecting unwanted ads into webpages, and redirecting users to sponsored websites. It may also cause the browser to become sluggish or crash frequently. The malware collects user information, such as browsing habits and personal data, which can then be sold to third-party advertisers or used for identity theft. AssistiveFormat can be difficult to remove as it often hides its files and processes deep within the system, making manual removal challenging for users without advanced technical knowledge. It is essential to use reputable antivirus software to detect and remove this type of malware effectively.