Unfortunately, I couldn’t find any specific information about a ransomware called “New24” as of my knowledge cutoff in October 2021. It’s possible that this ransomware might be a new or lesser-known variant, or it might have a different name. However, I can provide you with some general information about ransomware in general:
Ransomware is a type of malicious software that encrypts files on a victim’s computer or network, rendering them inaccessible. The attackers then demand a ransom payment, usually in cryptocurrency, in exchange for the decryption key. The encryption used by different ransomware variants can vary.
Ransomware can infect computers through various methods, including:
1. Phishing emails: Attackers send emails with malicious attachments or links that, when clicked or opened, execute the ransomware.
2. Exploit kits: These are malicious programs that exploit vulnerabilities in software or operating systems to deliver ransomware.
3. Malvertising: Attackers use malicious advertisements on legitimate websites to redirect users to websites hosting ransomware.
4. Remote Desktop Protocol (RDP) attacks: Attackers can exploit weak or default RDP credentials to gain access to a system and deploy ransomware.
The file extensions that ransomware adds to encrypted files can vary depending on the variant. Attackers often choose unique extensions to identify their ransomware. However, it is important to note that the absence of an identifiable extension does not necessarily mean the files are not encrypted.
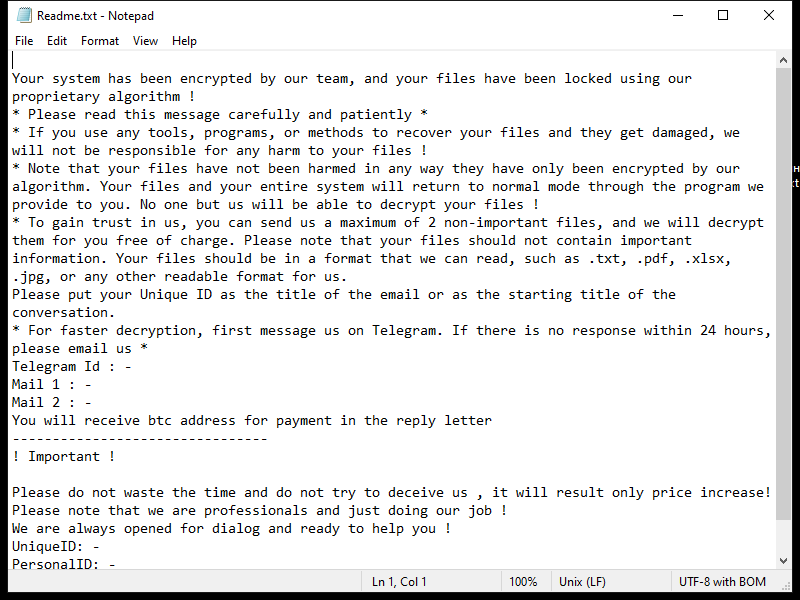
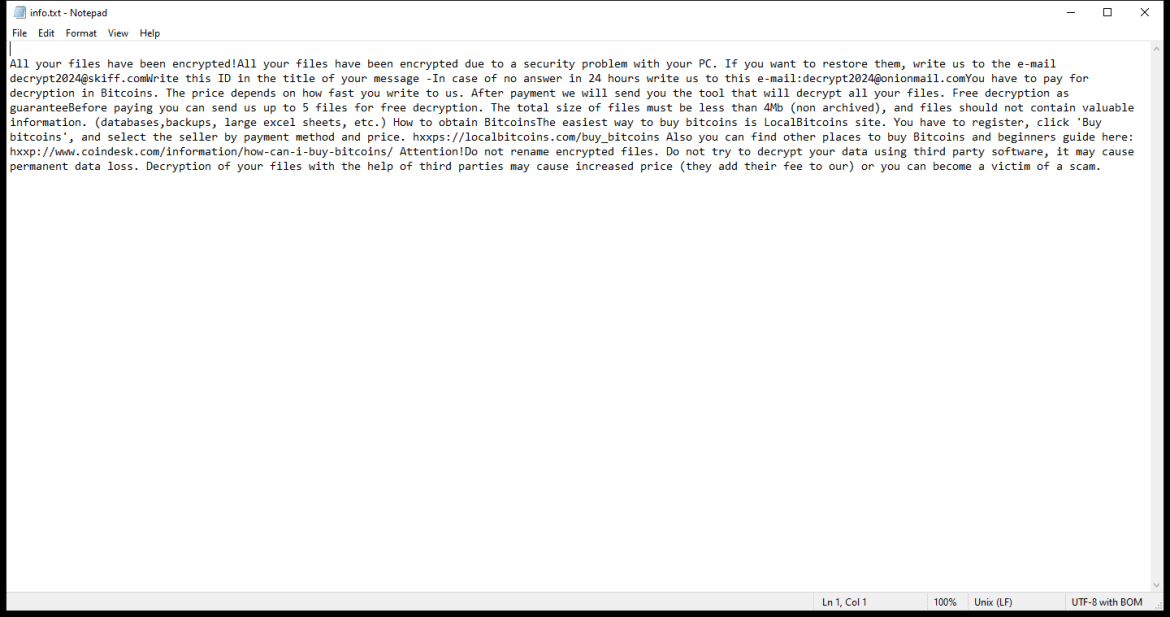
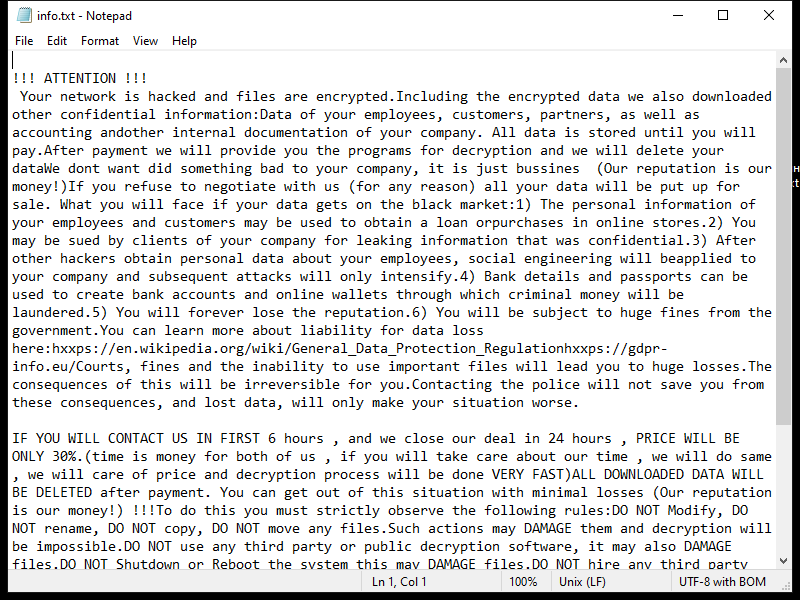
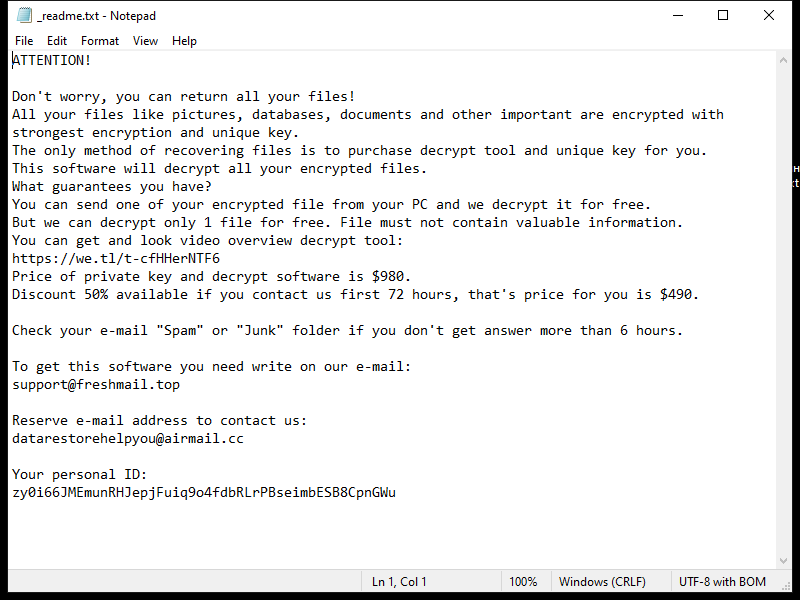
Ransomware typically leaves a ransom note that informs the victim about the attack and provides instructions on how to pay the ransom. The ransom note can be in the form of a text file, image, or even a pop-up message. The location of the ransom note can also vary, but it is commonly placed on the desktop or within folders containing encrypted files.
Decrypting ransomware-encrypted files without the decryption key is extremely difficult. In some cases, cybersecurity companies or law enforcement agencies may release decryption tools for certain ransomware variants. However, there is no guarantee that a decryption tool exists for a specific variant, especially if it is new or not widely distributed.
If you have become a victim of ransomware, it is generally recommended to report the incident to law enforcement and seek assistance from a reputable cybersecurity professional or organization. They may be able to provide guidance or potentially help with the decryption process if any tools are available.
Remember, prevention is crucial when it comes to ransomware. Regularly backing up important files, keeping software up to date, using strong and unique passwords, and being cautious of suspicious emails or websites can help protect against ransomware attacks.
Read more