Your Errors Team is a type of adware that can infect computers, typically without the user’s knowledge or consent. Adware is a computer software that automatically displays or downloads unwanted advertisements when a user is online. Your Errors Team adware often disguises itself as a legitimate program or is bundled with other software, tricking users into installing it. Once installed, it can interrupt the user’s browsing experience by displaying unsolicited ads, pop-ups and banners, typically injected into web pages that the user visits.
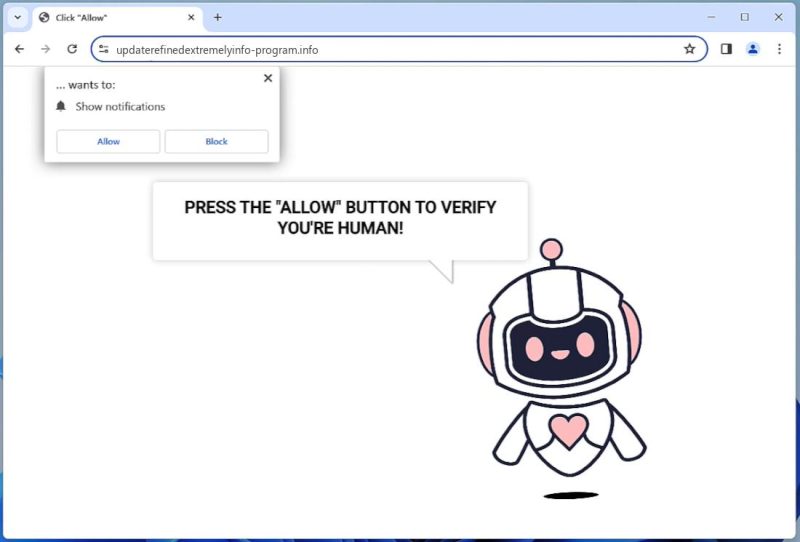
Your Errors Team adware typically infects computers through deceptive techniques known as bundling or through malicious websites. Bundling is a method where the adware is packaged with other software applications, often free ones, that the user downloads and installs. The adware is usually hidden in the ‘Advanced’ or ‘Custom’ installation options, which most users tend to ignore. Infections can also occur when a user visits a malicious website and clicks on a deceptive pop-up or link, which then downloads and installs the adware. Additionally, it can be spread through spam email attachments or infected USB drives.