Recipe Saver adware is a type of malicious software that commonly infiltrates computers through deceptive means and then delivers unwanted ads to users. It is usually disguised as a useful tool for saving and organizing recipes. This adware is notorious for displaying intrusive pop-up advertisements, redirecting users to suspicious websites, and tracking users’ online activities. It can affect various browsers such as Google Chrome, Mozilla Firefox, and Internet Explorer by changing browser settings or installing unwanted extensions.
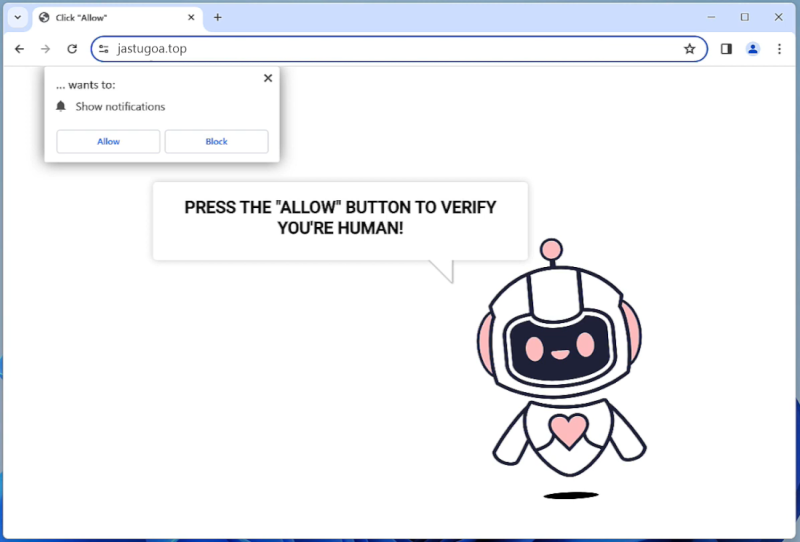
Recipe Saver typically infects computers and browsers through bundling, a method where it is included with other software that users download and install. Users inadvertently install the adware when they do not opt out of additional offers during the installation process of the main software. It can also infect computers through malicious email attachments, fake updates, or by clicking on infected ads or links. Once installed, Recipe Saver adware can decrease overall system performance, increase web traffic, and compromise user privacy by tracking personal information.