Title: Understanding VajraSpy RAT: An Android Infection Vector
Introduction:
In the realm of cyber threats, the emergence of Remote Access Trojans (RATs) has significantly increased the risks faced by Android devices. VajraSpy RAT is one such malicious software that poses a severe threat to the security and privacy of Android users. This expert article aims to shed light on what VajraSpy RAT is and how it infects Android devices, providing valuable insights into this stealthy malware.
Paragraph 1:
VajraSpy RAT, also known as Android/Vajraspy, is a highly sophisticated Remote Access Trojan that specifically targets Android devices. It acts as a powerful surveillance tool, allowing cybercriminals to gain unauthorized access to infected devices remotely. Once installed, this malicious software remains hidden and operates silently in the background, evading detection from the device owner. VajraSpy RAT is capable of gathering sensitive information, such as call logs, text messages, GPS coordinates, contacts, and even audio recordings, ultimately compromising the victim’s privacy. Furthermore, it can also intercept and manipulate various communication channels, making it a potent tool for cyber espionage.
Paragraph 2:
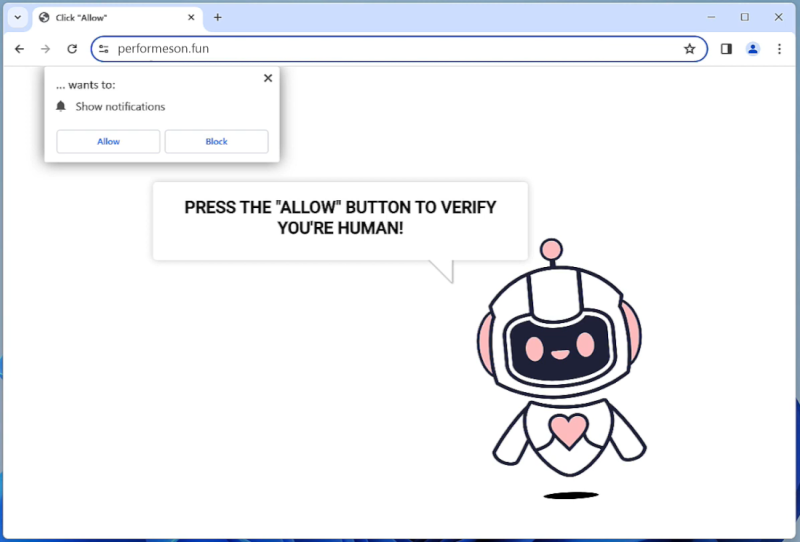
The infection of Android devices by VajraSpy RAT typically occurs through various deceptive techniques employed by cybercriminals. One common method is through the downloading of infected applications from untrusted sources or third-party app stores. These apps are often disguised as legitimate and attractive applications, enticing users to download and install them. Once installed, the RAT gains root access to the device, enabling it to execute privileged operations without the user’s knowledge or consent. Additionally, VajraSpy RAT can also exploit software vulnerabilities, enabling attackers to remotely install the malware onto targeted devices. This method, known as a “drive-by download,” can occur through malicious URLs or infected websites that automatically trigger the download and installation process, further complicating the detection and prevention of this malware.
In conclusion, the rise of VajraSpy RAT presents a significant threat to Android devices, compromising user privacy and enabling unauthorized access to sensitive information. As cybercriminals continue to evolve their tactics, it is crucial for Android users to remain vigilant and take proactive measures to protect their devices. Staying informed about the latest malware threats, avoiding untrusted app sources, and regularly updating device software are essential steps in safeguarding against VajraSpy RAT and similar malicious software.
Read more