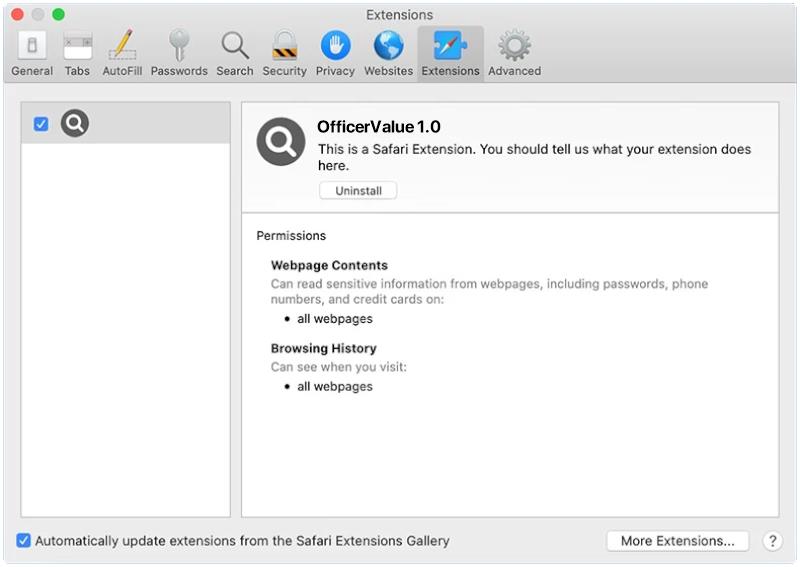
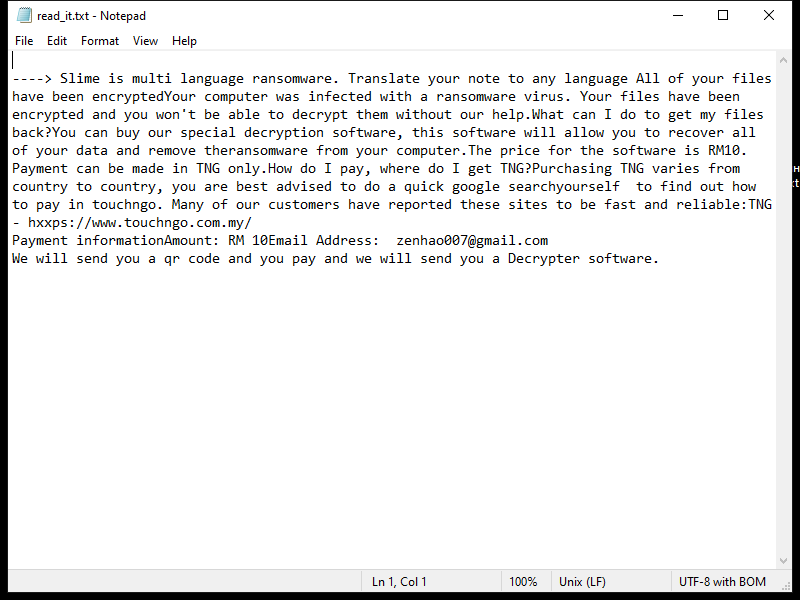
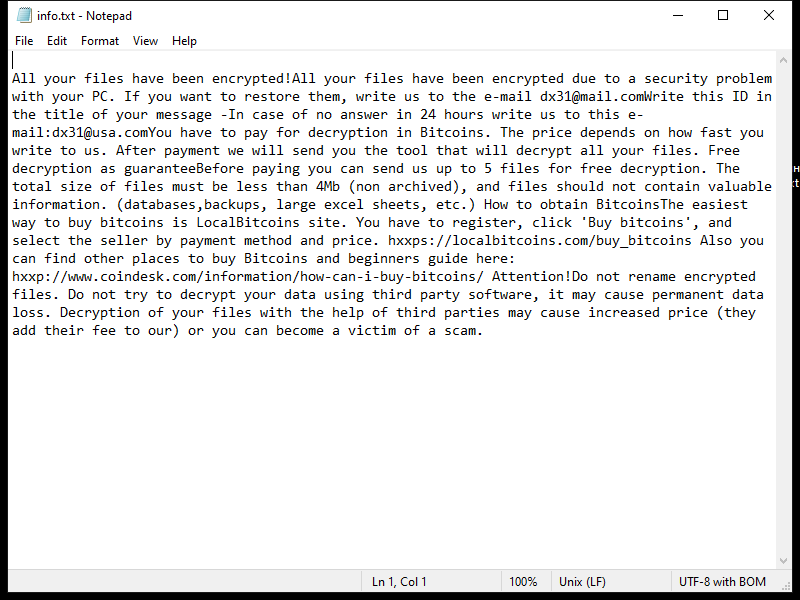
OfficerValue is a type of malware that primarily targets Mac operating systems. It is a sophisticated and stealthy Trojan that is designed to infect a Mac computer and gain unauthorized access to the system. Once it infiltrates a Mac, OfficerValue can perform a range of malicious activities without the user’s knowledge or consent.
The primary method of infecting a Mac with OfficerValue is through deceptive tactics such as social engineering or exploiting vulnerabilities in the system. It often disguises itself as a legitimate software or application, tricking users into downloading and installing it. Once installed, the malware establishes a connection with a remote server, allowing attackers to remotely control the infected Mac. This enables them to steal sensitive information, monitor user activities, or even inject additional malware onto the system.
OfficerValue is particularly dangerous as it can evade detection by security software and remain hidden on the Mac for extended periods. It can modify system settings, disable security features, and persistently run in the background without the user’s knowledge. To protect against this type of malware, it is crucial to exercise caution while downloading software from untrusted sources, keep the operating system and security software up to date, and regularly scan the Mac for any signs of malicious activity.