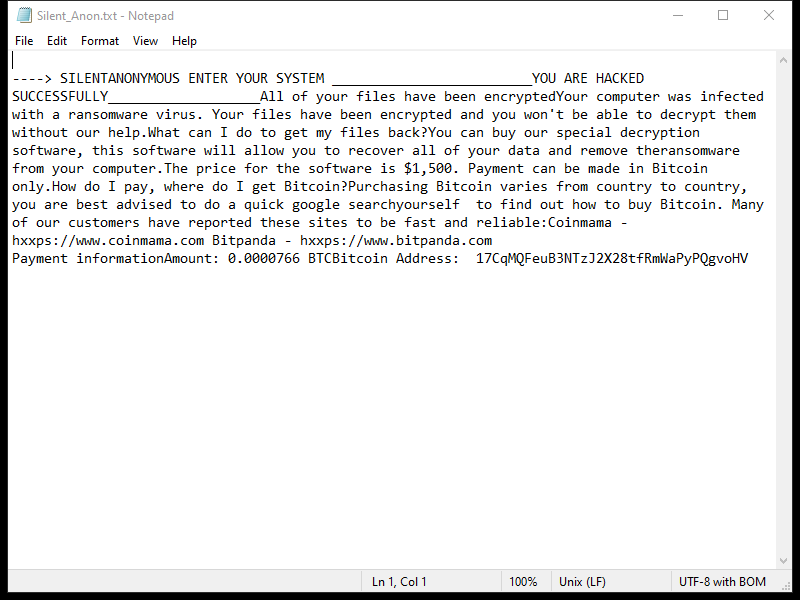
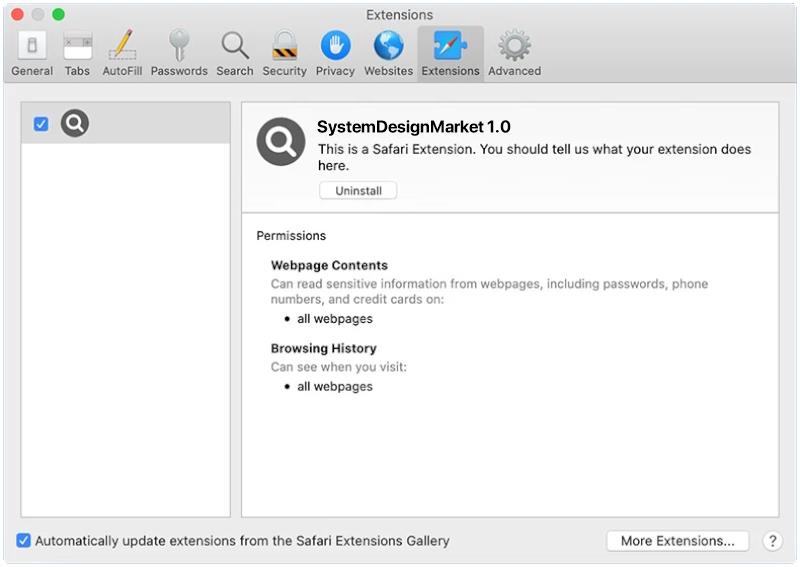
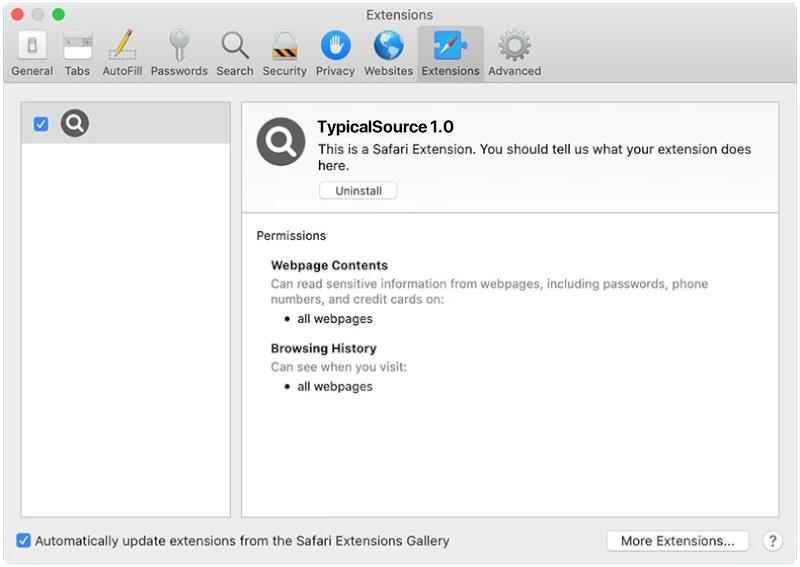
StandartSkill is a type of malware that specifically targets Mac operating systems. It is a Trojan horse that infects a user’s computer without their knowledge or consent. Once installed, StandartSkill can perform various malicious activities, compromising the security and privacy of the affected system.
StandartSkill often spreads through deceptive methods, such as disguising itself as a legitimate software download or a harmless email attachment. When users unknowingly execute the infected file, the Trojan gains access to the system and starts its malicious operations. Once infected, StandartSkill can perform tasks such as stealing sensitive data, recording keystrokes, taking screenshots, and hijacking webcams. It can also grant unauthorized remote access to the attacker, allowing them to control the infected Mac remotely and potentially carry out further malicious actions.
It is important for Mac users to stay vigilant and cautious while downloading software or opening email attachments to avoid falling victim to StandartSkill or any other malware. Keeping the operating system and security software up to date, utilizing strong passwords, and avoiding suspicious websites can help mitigate the risk of infection. Additionally, regularly scanning the system for malware and practicing safe browsing habits can further enhance the security of Mac devices.