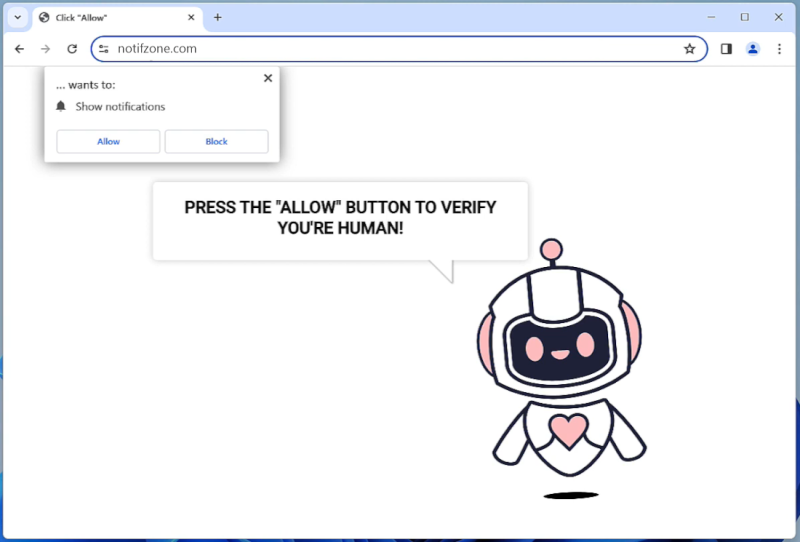
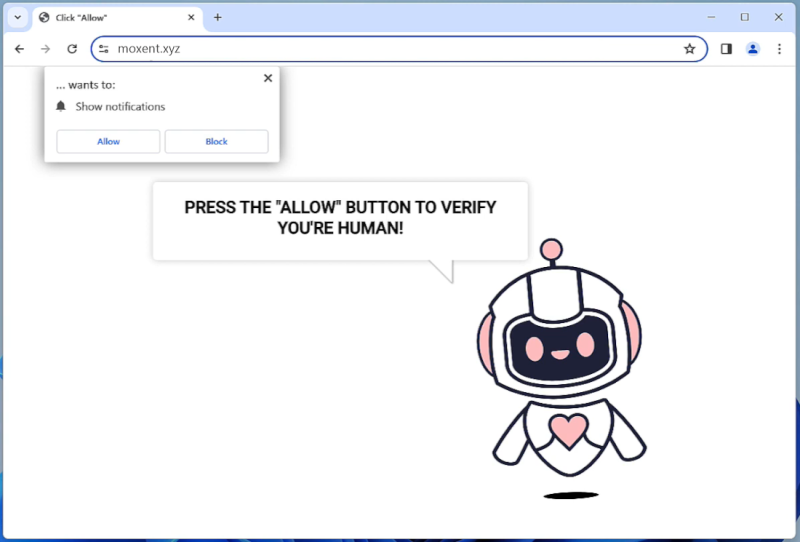
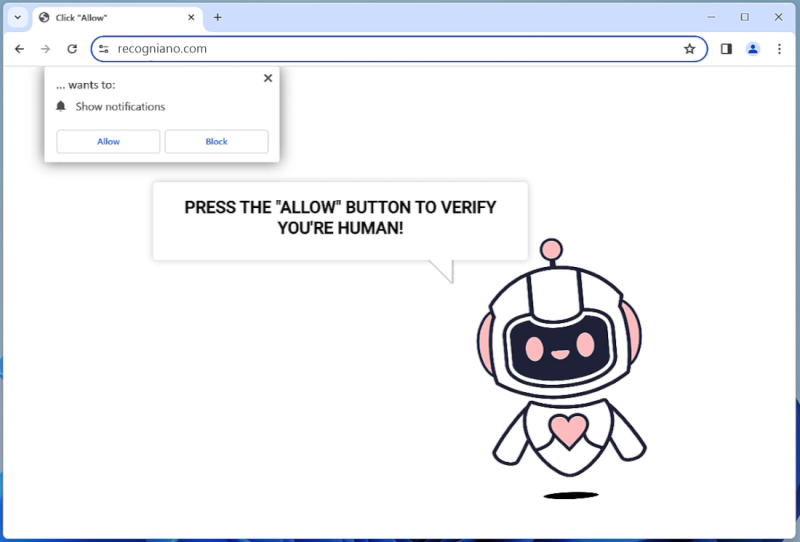
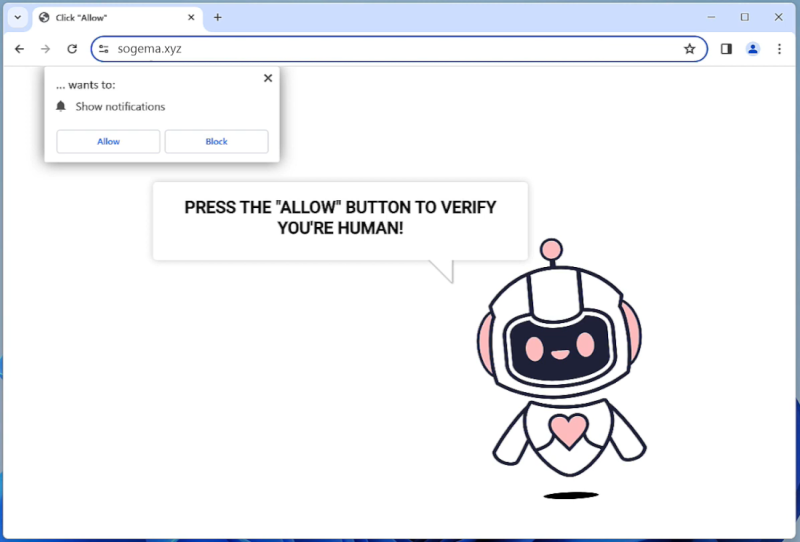
Notifzone.com is a potentially unwanted website that is known for its malicious behavior of exploiting browser notifications. It is categorized as an adware, which means it primarily aims to generate revenue through aggressive advertising techniques. Notifzone.com typically tricks users into subscribing to its push notifications by displaying deceptive pop-up messages. These messages may claim to provide exclusive content, offers, or updates, enticing users to click on the “Allow” button.
Once a user allows the notifications, Notifzone.com gains the ability to send unwanted advertisements directly to the user’s desktop or mobile device, even when the browser is closed. It can display various types of ads, such as pop-ups, banners, coupons, and sponsored links. This intrusive behavior can disrupt the user’s browsing experience and lead to privacy concerns, as the displayed ads may be misleading or contain malicious links.
Notifzone.com can infect various web browsers, including popular ones like Google Chrome, Mozilla Firefox, and Microsoft Edge. It can also affect both desktop and mobile devices, targeting users across different platforms. The adware’s creators employ various techniques to distribute Notifzone.com, such as bundling it with free software downloads, using misleading advertising campaigns, or redirecting users to infected websites. It is essential for users to be cautious while browsing the internet and to avoid clicking on suspicious pop-ups or allowing notifications from unknown sources to prevent infections such as Notifzone.com.