Ransom:Win32/Filecoder.Aa!Mtb is a type of ransomware that infects computers, encrypts files, and demands a ransom from the victim in order to regain access to their files. Ransomware is a malicious software that typically gains access to a computer through various means, such as:
1. Email attachments: The malware may be disguised as a legitimate file attachment in an email. When the victim opens the attachment, the ransomware gets executed and starts encrypting files on the computer.
2. Malicious websites: Visiting compromised or malicious websites can expose the computer to drive-by downloads, where the ransomware is automatically downloaded and executed without the user’s knowledge.
3. Exploit kits: Ransomware can exploit vulnerabilities in outdated software or operating systems to gain access to the computer. These vulnerabilities are typically patched by software developers, so it is essential to keep software up to date.
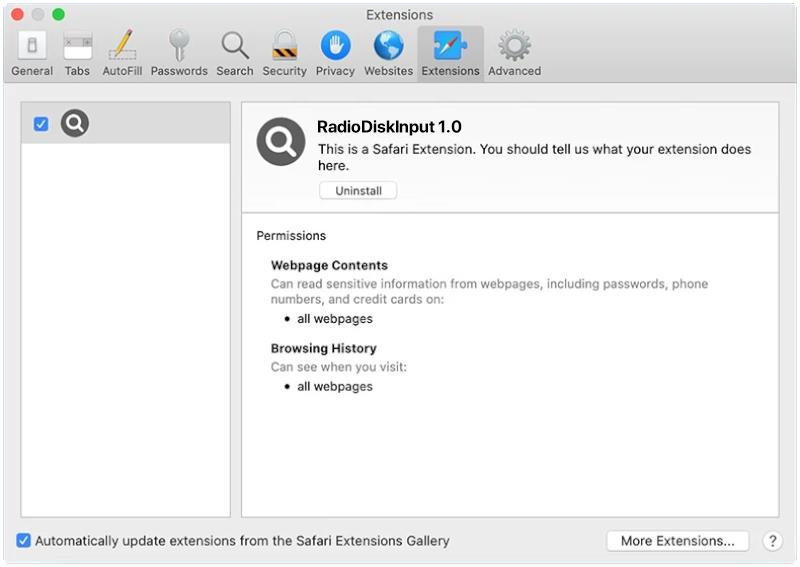
4. Infected software installers: Sometimes, ransomware is packaged with legitimate software installers. When the user installs the software, the ransomware also gets installed silently in the background.
Once the Ransom:Win32/Filecoder.Aa!Mtb ransomware infects a computer, it starts encrypting the victim’s files, making them inaccessible. It then typically displays a ransom note, demanding a sum of money, usually in cryptocurrency, to be paid within a specific timeframe. The ransom note provides instructions on how to make the payment and regain access to the encrypted files.
It is important to note that paying the ransom does not guarantee that the files will be decrypted or that the malware will be removed from the computer. It is generally recommended to avoid paying the ransom, as it encourages cybercriminals and does not guarantee a solution. Instead, victims should report the incident to law enforcement and seek assistance from cybersecurity professionals to mitigate the impact of the ransomware attack.