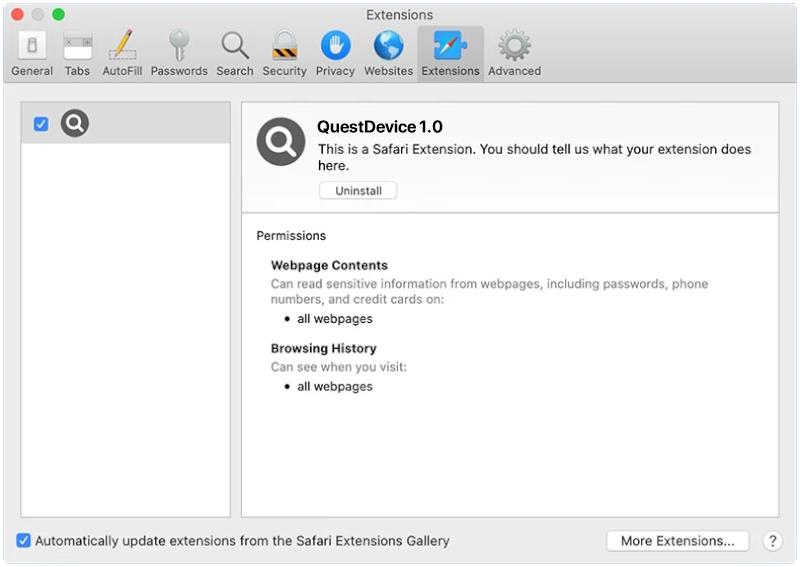
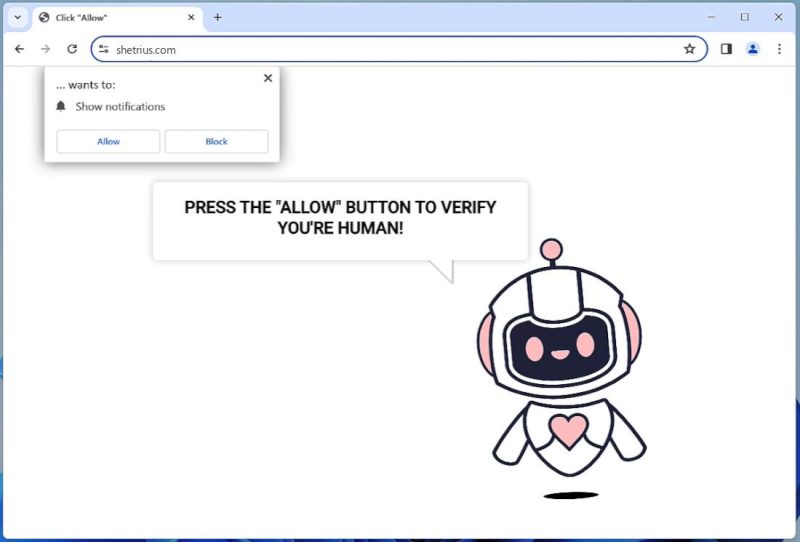
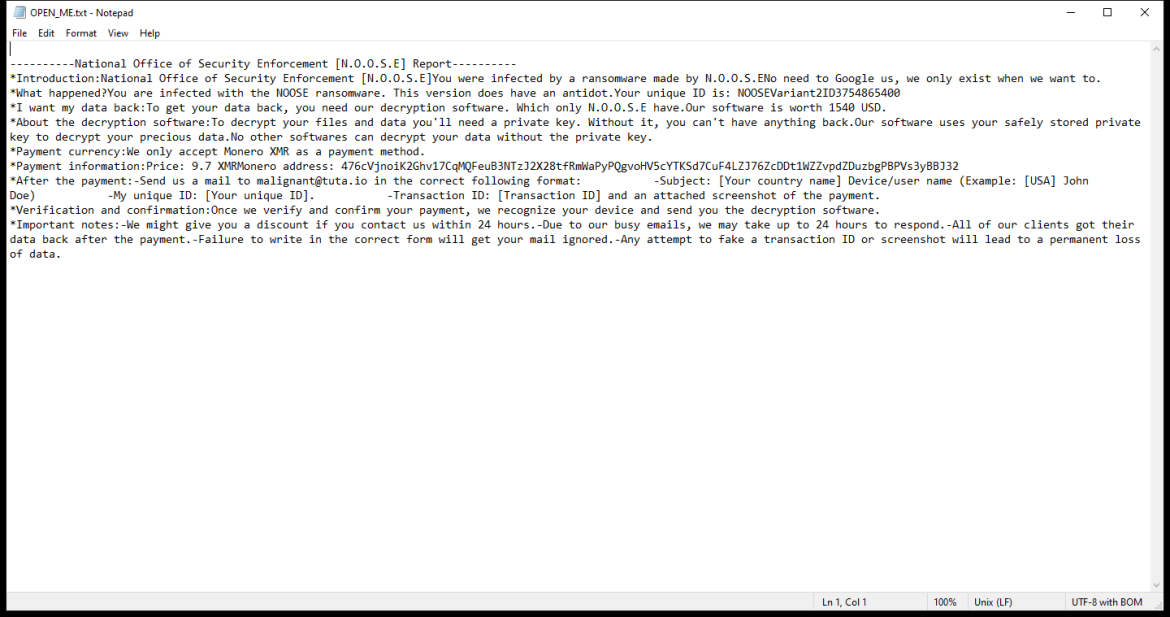
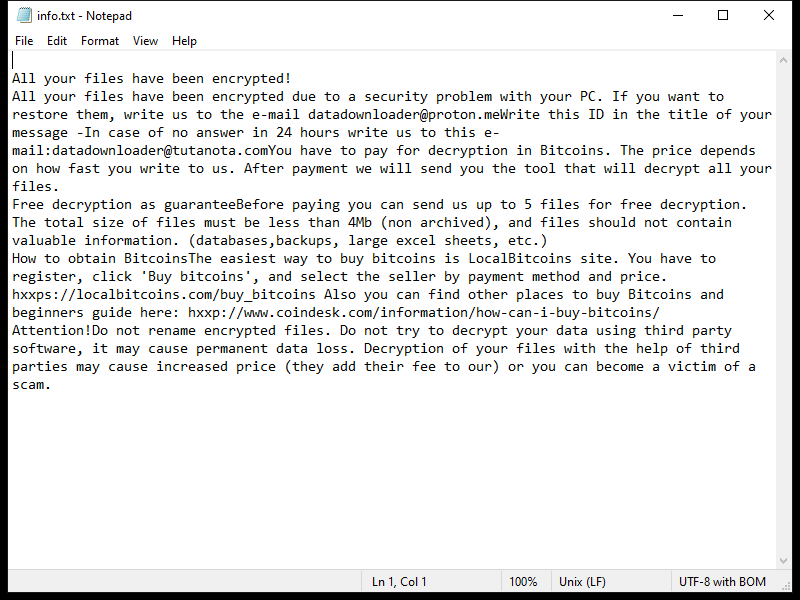
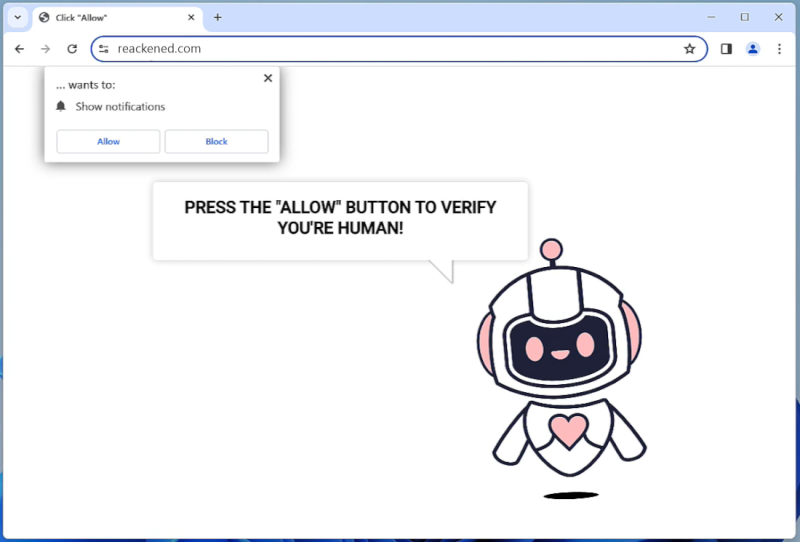
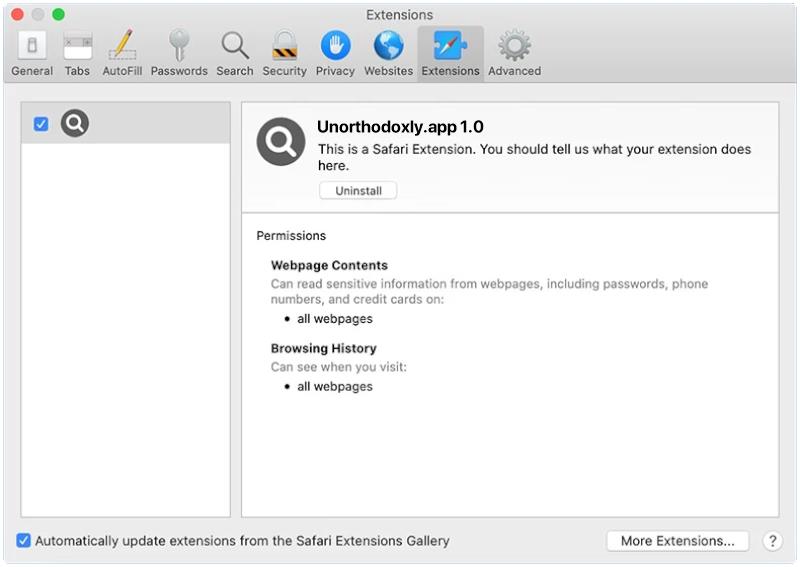
QuestDevice is a type of malware that specifically targets Mac computers. It is designed to infect the system and perform malicious activities without the user’s consent or knowledge. QuestDevice typically infiltrates Mac devices through various channels, such as malicious email attachments, software downloads from untrusted sources, or by exploiting vulnerabilities in the operating system or installed applications.
Once QuestDevice successfully infects a Mac, it can perform a range of harmful actions. For instance, it may collect sensitive information like login credentials, banking details, or personal data, which can then be used for identity theft or financial fraud. Additionally, QuestDevice may create backdoors in the system, allowing remote hackers to gain unauthorized access and control over the infected Mac. This can enable them to execute further malicious activities, such as installing additional malware, stealing more data, or using the infected machine as part of a larger botnet for launching cyberattacks. Overall, QuestDevice poses a significant threat to Mac users, highlighting the importance of maintaining strong security measures and being cautious while browsing the internet or downloading software.