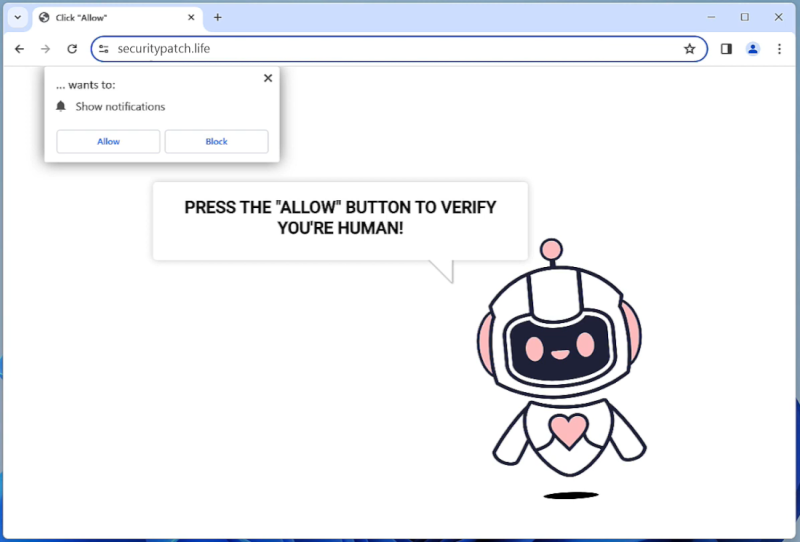
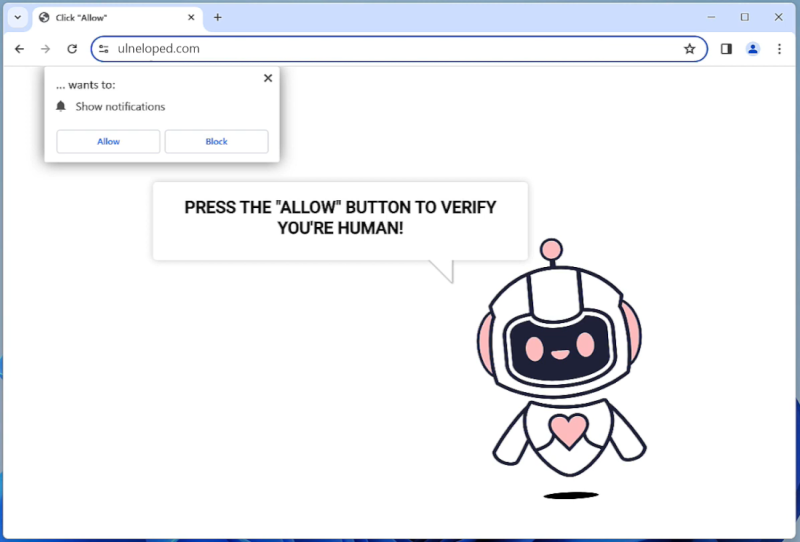
Securitypatch.life is a malicious website that is designed to trick users into downloading and installing potentially harmful software on their computers. Typically, users are redirected to this website through various means such as clicking on deceptive ads, visiting compromised websites, or being redirected by other malware. Once the user lands on Securitypatch.life, they are presented with a fake security alert claiming that their computer is infected with viruses or malware. The website urges users to click on a button to download and install a security patch to fix the supposed issue. However, if the user falls for this trick and downloads the suggested patch, they will actually be installing malware onto their system.
In addition to its deceptive practices, Securitypatch.life also exploits browser notifications to further infect computers. If a user allows notifications from this website, they may start receiving a barrage of pop-up messages containing fraudulent information or enticing offers. These notifications can be very intrusive and difficult to close, making it more likely for users to click on them accidentally. Through these notifications, Securitypatch.life may promote other malicious websites, display fake software updates, or even try to trick users into revealing personal information. This way, it continues to spread its malicious activities and potentially infect more devices.
Securitypatch.life can affect various browsers and devices. It can target popular web browsers such as Google Chrome, Mozilla Firefox, and Microsoft Edge, among others. As for devices, it can infect both Windows and Mac computers. It is important for users to stay cautious while browsing the internet and avoid clicking on suspicious links or downloading software from unknown sources to prevent falling victim to Securitypatch.life and other similar malware.