Virus:Win32/Expiro.Ek!Mtb is a type of computer virus classified as a Trojan horse. Trojans are malicious software programs that disguise themselves as legitimate files or applications to trick users into executing them, allowing hackers to gain unauthorized access to the affected system.
Virus:Win32/Expiro.Ek!Mtb infects computers through various means, including:
1. Email attachments: The virus can be spread through infected email attachments. When the user opens the attachment, the virus is executed, and it starts infecting the computer.
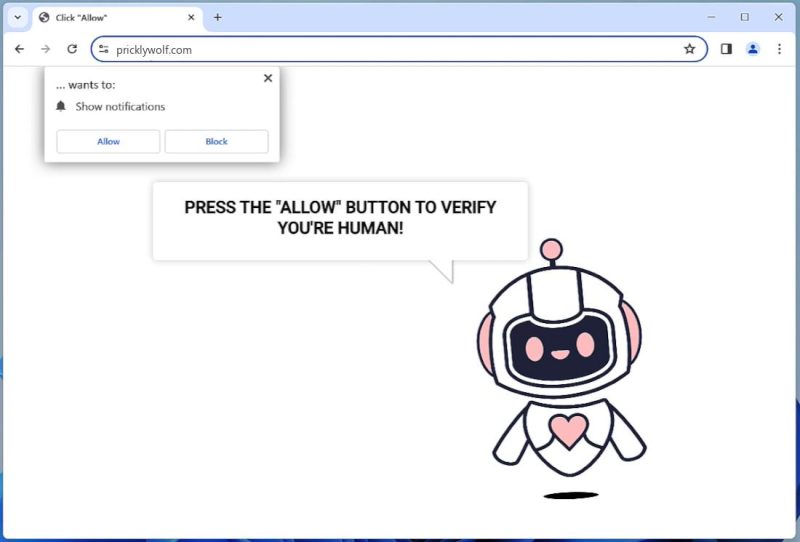
2. Malicious websites: Visiting compromised or malicious websites can result in the automatic download and execution of the virus.
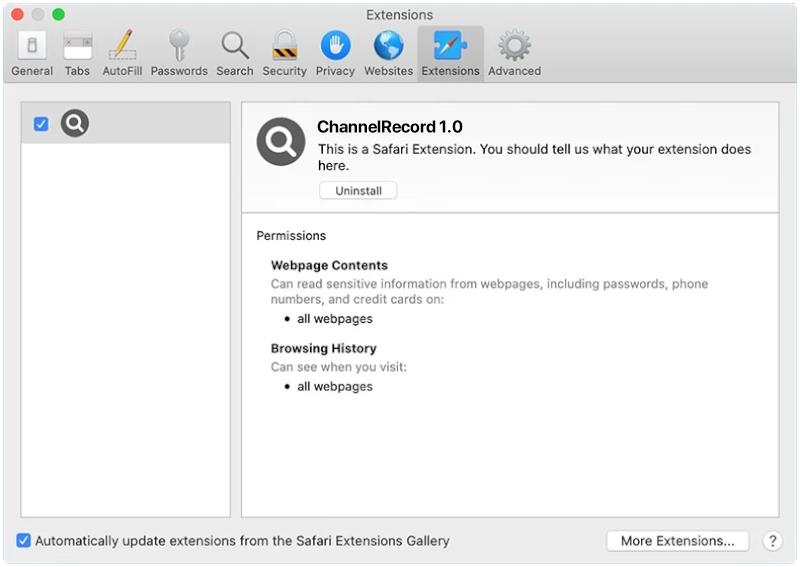
3. Software downloads: Downloading software from unofficial or untrusted sources can often lead to the installation of malware, including Virus:Win32/Expiro.Ek!Mtb.
4. Exploit kits: Exploit kits are toolkits that hackers use to take advantage of vulnerabilities in software or operating systems. By exploiting these vulnerabilities, the virus can be injected into the computer.
Once the virus infects a computer, it may perform various malicious activities, such as stealing sensitive information, modifying or deleting files, and allowing remote access to the compromised system for further exploitation.
To protect your computer from Virus:Win32/Expiro.Ek!Mtb and similar threats, it is essential to keep your operating system and software up to date, use reliable antivirus software, avoid downloading files from suspicious sources, and exercise caution when opening email attachments or visiting unfamiliar websites.