OneSafe PC Cleaner is a computer optimization tool that claims to improve the performance of your computer by scanning for and removing junk files, unnecessary registry entries, and other redundant items. However, it is essential to note that this program is often categorized as potentially unwanted software (PUS) or a potentially unwanted program (PUP). This is primarily due to its deceptive distribution methods and the misleading information it provides about the status of your computer. In many cases, OneSafe PC Cleaner tends to exaggerate the level of threat or issues present in the system, creating an illusion of severe problems to persuade users into purchasing its full version. The infiltration of OneSafe PC Cleaner into computers typically involves software bundling, a common technique used by many PUP developers. This method entails packaging the unwanted program with other popular free software, so users inadvertently download and install the PUP while installing the desired software. Users may also unwillingly download OneSafe PC Cleaner from deceptive pop-up advertisements or compromised websites that trick visitors into believing their computers are at risk. Once installed, OneSafe PC Cleaner starts performing unnecessary system scans and displaying alarming results to create a sense of urgency, encouraging users to buy its premium version. Therefore, although it is not a virus or malware, the manipulative tactics employed by OneSafe PC Cleaner classify it as a potentially unwanted program.
Author: admin
How to remove Vbmarker
VBMarker is a type of malware that infects computers. It is classified as a Visual Basic script virus and is known for its ability to spread through removable storage devices, particularly USB drives.
When a computer is infected with VBMarker, it typically occurs when a user inserts an infected USB drive into their computer. The virus takes advantage of the AutoRun feature in Windows, which automatically executes certain commands when a removable storage device is connected. VBMarker creates an autorun.inf file on the USB drive, which contains specific instructions to execute the virus.
Once executed, VBMarker starts infecting other files on the computer and any connected storage devices. It typically targets executable files by injecting malicious code into them, making it difficult to detect and remove. The virus can also disable antivirus software and perform other malicious actions.
VBMarker is designed to spread rapidly and can quickly infect multiple computers within a network if connected devices are shared. It can cause system slowdowns, crashes, and may even compromise sensitive data.
To protect against VBMarker and similar malware, it is essential to keep antivirus software up to date, avoid connecting unknown or suspicious USB drives to your computer, and regularly scan your system for any signs of infection.
How to remove Adware:Win32/Trickler
Adware:Win32/Trickler is a type of adware that infects computers and displays unwanted advertisements to users. It is designed to generate revenue for the creators by forcing users to view or click on these advertisements.
Adware:Win32/Trickler typically infects computers through deceptive methods such as bundling itself with legitimate software downloads. When users download and install the software, the adware is installed alongside it without their knowledge or consent. It can also be spread through malicious email attachments, infected websites, or by exploiting vulnerabilities in outdated software.
Once installed, Adware:Win32/Trickler modifies the browser settings and injects unwanted advertisements into webpages visited by the user. These ads can be displayed as pop-ups, banners, or even as text links within the content. The adware may also redirect the user to malicious websites or install additional unwanted software.
Adware:Win32/Trickler can significantly slow down the infected computer’s performance, consume system resources, and cause stability issues. It can also collect user data and browsing habits to deliver targeted advertisements.
To protect your computer from Adware:Win32/Trickler and similar threats, it is important to practice safe browsing habits. This includes being cautious when downloading software from untrusted sources, regularly updating your software and operating system, and using reputable antivirus software to scan and remove any potential threats.
How to remove Mycool Search
Mycool Search adware is a potentially unwanted program (PUP) that infiltrates computers and browsers, primarily targeting Windows operating systems. It falls under the category of adware due to its intrusive behavior of displaying unwanted advertisements and redirecting users to sponsored websites. Mycool Search claims to enhance the web browsing experience by providing improved search results and quick access to various online services. However, its true purpose is to generate revenue for its creators through the promotion of third-party content.
Mycool Search usually infects computers through deceptive software bundling techniques. It is often bundled with free software downloaded from unreliable websites or distributed through fake software update prompts. When users unknowingly install such bundled software, Mycool Search gets installed alongside it without their consent. Additionally, it may also infect browsers by modifying their settings, such as the default search engine, homepage, and new tab page, to redirect users to its own search engine and display sponsored advertisements. This intrusive behavior can disrupt the user’s browsing experience and compromise their privacy, as Mycool Search may collect and share their browsing data with third parties for targeted advertising purposes.
How to remove Trojan:Win32/Riseprostealer.A!Mtb
Trojan:Win32/Riseprostealer.A!Mtb is a type of malicious software, commonly known as a Trojan horse, that targets Windows operating systems. It is designed to steal sensitive information from infected computers, such as login credentials, credit card details, and personal data.
Trojans like Trojan:Win32/Riseprostealer.A!Mtb often infect computers through various methods, including:
1. Email attachments: The Trojan may be disguised as a legitimate file attached to an email. Once the attachment is opened, the malware gets executed and infects the system.
2. Malicious websites: Visiting compromised websites or clicking on malicious ads can lead to the download and execution of Trojans.
3. Software vulnerabilities: Exploiting security weaknesses in software or operating systems allows Trojans to gain unauthorized access to a computer.
4. Social engineering: Cybercriminals may trick users into downloading and executing Trojans by disguising them as legitimate software or enticing users to click on malicious links.
Once a computer is infected with Trojan:Win32/Riseprostealer.A!Mtb, it may perform various malicious activities silently in the background. These activities can include logging keystrokes, capturing screenshots, monitoring web browsing activities, and transmitting the stolen data to remote servers controlled by cybercriminals.
To protect your computer from Trojans and other malware, it is essential to maintain up-to-date antivirus software, regularly update your operating system and applications, avoid downloading files from untrusted sources, and exercise caution when opening email attachments or clicking on links.
How to remove Win32/Skeeyah
Win32/Skeeyah is a type of malware classified as a Trojan horse. Trojans are malicious software that disguise themselves as legitimate programs and can perform various harmful actions on a computer system without the user’s knowledge or consent.
Once a computer is infected with Win32/Skeeyah, it can perform several malicious activities. Some common actions performed by this Trojan include stealing sensitive information such as login credentials, credit card numbers, or personal data. It may also allow unauthorized access to the infected computer, enabling remote hackers to control the machine or use it for illegal activities.
Win32/Skeeyah typically spreads through various means, such as email attachments, infected software downloads, malicious websites, or exploiting security vulnerabilities in the operating system or other software applications. It can also be distributed through social engineering techniques, where users are tricked into running the malware by clicking on malicious links or downloading infected files.
It is important to have up-to-date antivirus software installed on your computer and to exercise caution while opening emails or downloading files from unknown sources to minimize the risk of being infected by Win32/Skeeyah or any other malware.
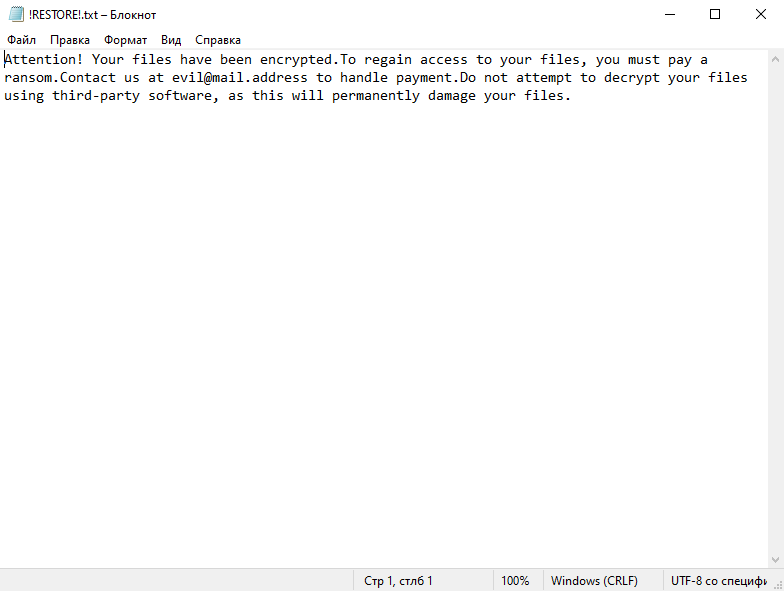
How to remove Tprc Ransomware and decrypt .tprc files
Tprc Ransomware is a type of malicious software that belongs to the Djvu ransomware family. Its primary function is to encrypt files on a victim’s computer, making them inaccessible until a ransom is paid.
Infection Methods:
Tprc ransomware typically infects computers through spam email attachments, dubious software downloads, or malicious advertisements. Users often inadvertently download and install the ransomware by opening an infected file or clicking on a suspicious link.
File Extensions:
Once in the system, Tprc ransomware scans for files to encrypt and appends a specific extension to the affected files. The extension is typically “.tprc”.
File Encryption:
Tprc Ransomware uses asymmetric encryption, typically RSA or AES, to lock the victims’ files. Asymmetric encryption involves a pair of keys – a public key to encrypt the files and a private key to decrypt them. The private key is held by the attacker, who demands a ransom in exchange for it.
Ransom Note:
After encrypting the files, Tprc Ransomware generates a ransom note, usually in a text file. The note typically includes information about the encryption and instructions on how to pay the ransom to retrieve the decryption key. This note is usually placed in every folder containing the encrypted files, often named “_readme.txt”.
Decryption Tools:
It’s important to note that paying the ransom does not guarantee that the files will be decrypted. In fact, it only encourages the criminals to continue their illicit activities. Instead, victims should seek professional help to remove the ransomware and restore their files. However, as of now, there are no specific decryption tools available for Tprc Ransomware.
Decryption of %EXTENSION% Files:
Decryption of files encrypted by Tprc Ransomware is challenging without the private key. However, victims can try to recover their files through other means such as backup copies, shadow volume copies, or file recovery tools. In some cases, cybersecurity firms or law enforcement agencies may be able to assist with decryption. It’s always advisable to maintain regular backups of important files and keep your system and antivirus software up-to-date to prevent such infections.
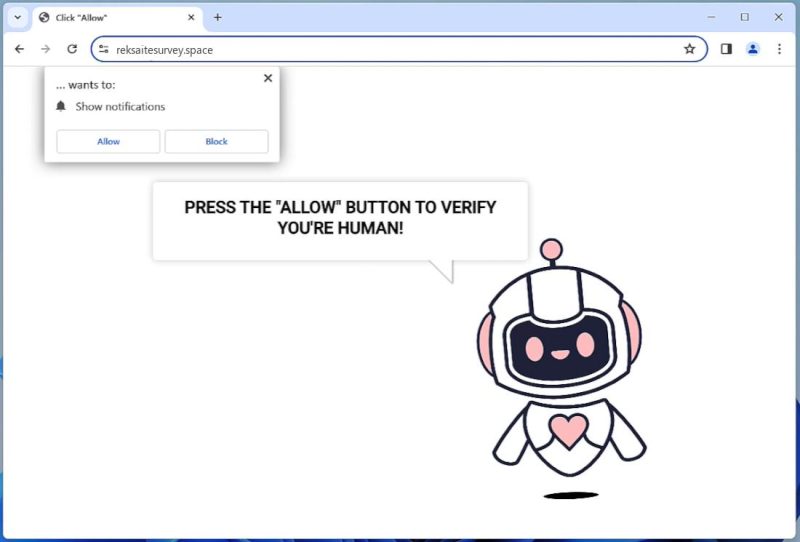
How to remove Reksaitesurvey.space
Reksaitesurvey.space is a potentially malicious website designed to trick users into enabling push notifications on their browser. It employs deceptive tactics, such as displaying fake error messages, surveys, or prizes to mislead users into subscribing to its notifications. This website does not infect computers in the traditional sense, like a virus or malware. Instead, it relies on social engineering tactics to trick users into interacting with it.
Reksaitesurvey.space exploits browser notifications by asking users to allow notifications to continue with a page, view content, or claim a prize. Once the users click the ‘allow’ button, they start receiving unwanted advertisements and pop-ups directly on their desktop. It can affect multiple browsers including Google Chrome, Mozilla Firefox, Safari, and Internet Explorer, and it is not limited to any particular device. Both Windows and Mac systems can be targeted, as well as Android and iOS devices.
How to remove Trojan:Msil/Agenttesla.Lan!Mtb
Trojan:Msil/Agenttesla.Lan!Mtb is a type of malware that belongs to the Trojan family. Trojan malware is designed to appear harmless or legitimate, while in reality, it carries out malicious activities without the user’s knowledge or consent.
Trojan:Msil/Agenttesla.Lan!Mtb specifically refers to a variant of the Agent Tesla Trojan that primarily targets Microsoft .NET Framework. Agent Tesla is a type of Remote Access Trojan (RAT) that enables unauthorized individuals to remotely control an infected computer. It is commonly used for stealing sensitive information such as login credentials, banking details, and personal data.
Trojans like Agent Tesla are typically distributed through various means, including:
1. Phishing emails: The malware may be attached as a file or embedded within a malicious link in an email. Opening the attachment or clicking the link can initiate the infection process.
2. Malicious websites: Visiting compromised or malicious websites can trigger the automatic download and installation of the Trojan onto the user’s computer.
3. Software vulnerabilities: Exploiting security flaws or vulnerabilities in software (such as outdated operating systems, browsers, or plugins) can allow Trojans to gain unauthorized access to a system.
4. Infected external devices: Trojans can also spread through infected USB drives, external hard drives, or other removable media.
To protect your computer from Trojan:Msil/Agenttesla.Lan!Mtb and other malware, it is crucial to follow good security practices, such as:
– Keep your operating system, software, and antivirus programs up to date.
– Exercise caution when opening email attachments or clicking on links, especially from unknown or suspicious sources.
– Only download software from trusted sources.
– Regularly scan your computer for malware using reputable antivirus software.
– Use a firewall to block unauthorized access to your system.
– Backup your important files and data regularly to minimize potential damage in case of an infection.
Remember, avoiding interactions with suspicious content and maintaining a robust security posture significantly reduces the risk of malware infections.
How to remove Trojan:Win32/Mptamperbulkexcl.C
Trojan:Win32/Mptamperbulkexcl.C is a type of Trojan horse malware that infects computers running the Windows operating system. It is a malicious program that disguises itself as a legitimate file or software to gain unauthorized access to a computer system. Once installed, it can perform various malicious activities without the user’s knowledge or consent.
Trojan:Win32/Mptamperbulkexcl.C infects computers through various means, including:
1. Email attachments: The Trojan can be distributed through infected email attachments. When the user opens such attachments, the Trojan gets executed, infecting the computer.
2. Software downloads: It can also be bundled with pirated or cracked software, or disguised as a legitimate software download from untrusted sources. When the user installs or runs the downloaded software, the Trojan gets installed alongside it.
3. Malicious websites: Visiting compromised or malicious websites can lead to a drive-by download, where the Trojan gets downloaded and installed automatically without the user’s knowledge.
4. Exploiting software vulnerabilities: The Trojan can exploit vulnerabilities in outdated or unpatched software to gain unauthorized access and infect the computer.
Once the Trojan infects a computer, it can perform various malicious activities, such as stealing sensitive information (e.g., passwords, credit card details), modifying or deleting files, downloading and installing additional malware, and taking control of the infected system.
To protect your computer from Trojan:Win32/Mptamperbulkexcl.C and other malware, it is important to keep your operating system and software up to date, avoid downloading files from untrusted sources, be cautious when opening email attachments, use a reliable antivirus software, and regularly scan your computer for malware.