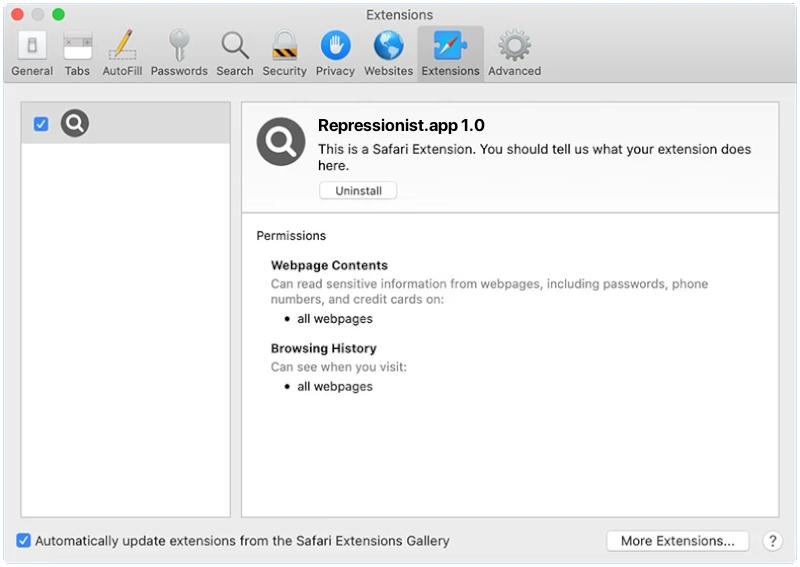
Repressionist.app is a potentially unwanted program (PUP) or adware that often targets Mac users. It is a deceptive software that is typically bundled with other free software or programs that you download off of the internet. Once installed, it can lead to a variety of unwanted behaviors such as displaying annoying pop-up ads, redirecting your browser to unwanted sites, and slowing down your computer. It can also potentially expose your system to other more serious threats like malware or spyware. Repressionist.app usually infects a Mac when the user unknowingly installs it alongside other software. This type of adware is often hidden in the advanced or custom settings of the installation process, and if these settings are not carefully checked, the unwanted program can be installed without the user’s knowledge. In some cases, it might also be disguised as a necessary update or tool that the user is tricked into downloading. It’s always recommended to only download software from trusted sources and to carefully review all installation settings to avoid such threats.
Author: admin
How to remove PakicetusAttocki
PakicetusAttocki is a type of adware, which is software that automatically displays or downloads advertising material such as banners or pop-ups when a user is online. It is designed to generate revenue for its creator by generating online clicks and page views for advertisers. This adware can also collect user’s personal information, track online activities, and change browser settings without user’s consent, making it a threat to both personal privacy and computer security. PakicetusAttocki infects computers through various methods. One common way is through bundled software, where the adware is hidden within the installation files of a legitimate program. When the user installs this program, the adware is also installed without their knowledge. Another method is through malicious websites or email attachments. When the user visits these sites or opens the attachments, the adware is automatically downloaded and installed onto their computer. Once infected, the computer will start displaying unwanted ads and pop-ups, and the user may notice a slowdown in their computer’s performance due to the adware using up system resources.
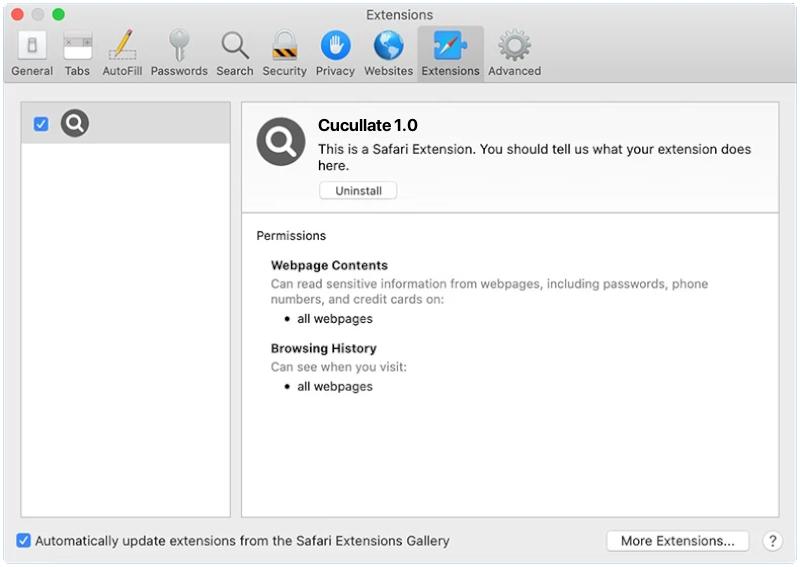
How to remove Cucullate (Mac)
Cucullate is a type of malware that targets Mac computers. It is often disguised as a legitimate software or application and can be unknowingly downloaded by users when they visit compromised websites or open malicious email attachments. Once installed, Cucullate can gather sensitive data, such as login credentials and banking information, from the affected system. It can also provide hackers with remote access to the infected computer, allowing them to take control and perform a range of malicious activities. The infection process of Cucullate typically begins when users download and install a malicious application that contains the malware. This can happen when users are tricked into clicking on a fake update or software download link. Once the malicious application is installed, Cucullate activates and starts its data collection process. In some cases, Cucullate can also exploit vulnerabilities in the system or use social engineering techniques to gain administrative privileges, which can increase its control over the system and make it more difficult to detect and remove.
How to remove PC HelpSoft Driver Updater
PC HelpSoft Driver Updater is a system optimization tool designed to manage your computer’s drivers. It operates as an automated tool that scans your computer to identify outdated or missing drivers, subsequently updating them to improve the system’s performance and stability. This software claims to significantly enhance your PC’s functionality by ensuring its drivers are up-to-date, thereby reducing system crashes and improving overall performance. However, despite its utility-focused facade, PC HelpSoft Driver Updater is often categorized as potentially unwanted software (PUS). This categorization is due to its intrusive behavior, as it frequently lands on computer systems without the user’s explicit consent. It mainly infects computers through bundling, a marketing strategy used by many free software providers. In this strategy, the PC HelpSoft Driver Updater comes as an additional package or a ‘recommended application’ alongside another software that the user intends to download. As a result, it often gets installed unbeknownst to the user, leading to unwanted changes in the system. Furthermore, once installed, it tends to perform automatic system scans and generate alarming results concerning outdated drivers, compelling the user to purchase its full version for driver updates. This invasive behavior and the deceptive scare tactics used to encourage purchases are key reasons why PC HelpSoft Driver Updater is often deemed undesirable.
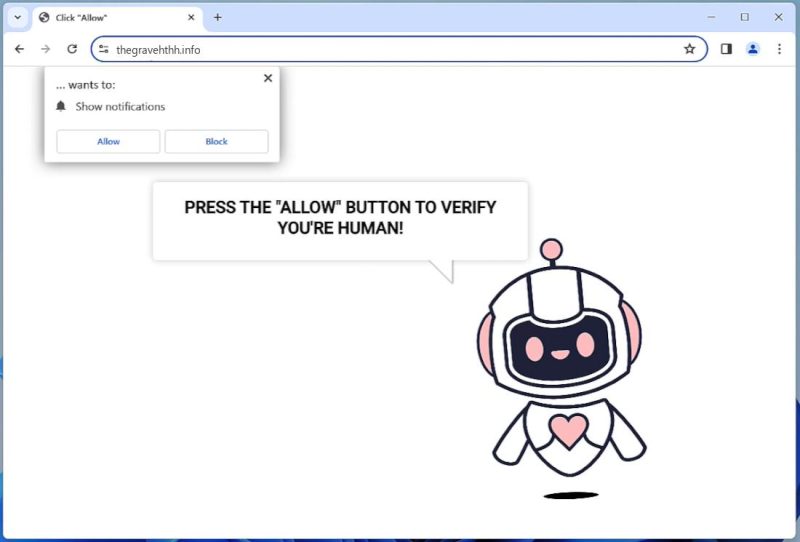
How to remove Thegravehthh.info
Thegravehthh.info is a malicious site known for employing social engineering methods to trick users into subscribing to its browser notifications. The site usually claims that clicking “Allow” is necessary to access the content of the site, to confirm that the user is not a robot, to proceed to the website, or to watch a video. Once users click “Allow”, they start receiving unwanted advertisements directly on their desktop or browser. These ads can lead to potentially harmful sites, introduce malware, or download unwanted and potentially harmful software. Thegravehthh.info can infect any device that uses a web browser, including personal computers, smartphones, and tablets. It targets all major browsers such as Google Chrome, Mozilla Firefox, Internet Explorer, Safari, and Microsoft Edge. The infection usually occurs when users visit compromised websites, click on malicious advertisements, or download software from untrustworthy sources. Users may also get infected through email links or attachments. This malicious site exploits browser notifications by sending push notifications containing ads or links to malicious sites.
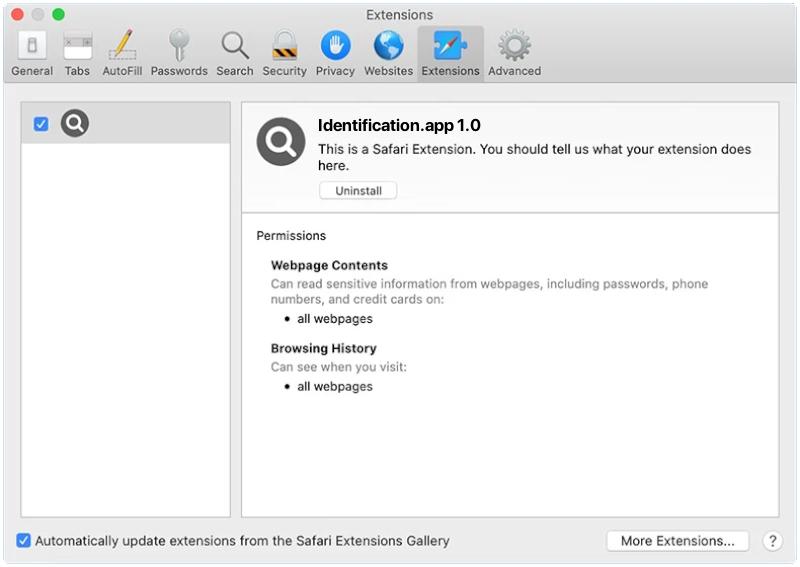
How to remove Identification.app (Mac)
Identification.app is a potentially unwanted program (PUP) or a type of malware that can infiltrate your Mac without your knowledge. This app usually presents itself as a legitimate and useful tool, while in reality, it carries out various malicious activities. It can degrade your system’s performance, show intrusive ads, redirect browsers to sponsored pages, and even collect personal information. This app typically gets into your system bundled with freeware or shareware, or through deceptive advertising. Infection with Identification.app usually starts when a user unknowingly installs a freeware or shareware that has this app bundled into it. The developers often use a deceptive marketing method known as “bundling” to spread PUPs like Identification.app. Users might also get infected by clicking on deceptive ads or links that automatically download the app. Once inside a system, the Identification.app can make changes to the browser settings, install additional malicious software, and begin its harmful activities. To protect your system, it’s important to download software from reputable sources, be cautious about clicking on ads, and use reliable antivirus software.
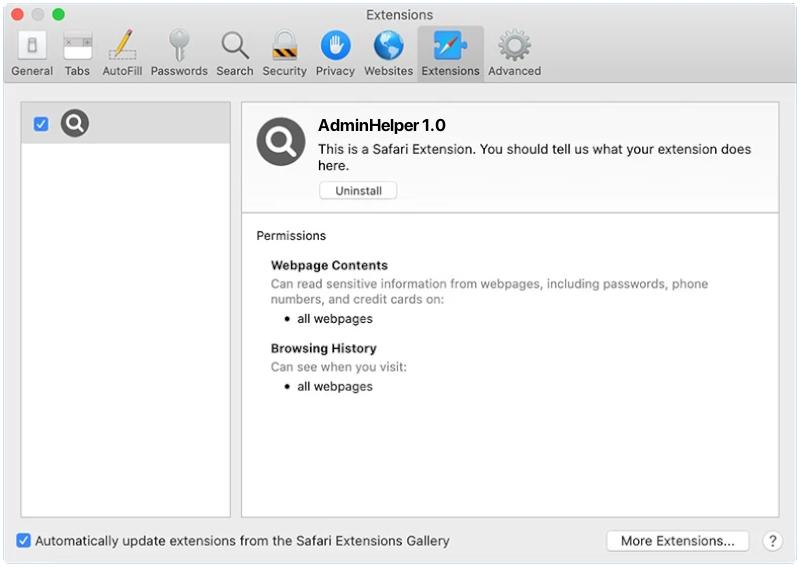
How to remove AdminHelper (Mac)
AdminHelper is a type of potentially unwanted program (PUP) or adware that primarily targets Mac operating systems. It is often disguised as a legitimate system utility tool, promising to enhance the performance of your device by cleaning unnecessary files or optimizing various functions. However, once installed, AdminHelper exhibits intrusive behavior such as displaying unwanted advertisements, redirecting browsers to suspicious websites, or even potentially installing more malicious software without the user’s consent. AdminHelper usually infects Mac systems through bundled software or deceptive marketing strategies. It often comes hidden within the installation packages of free software downloaded from the internet, and gets installed when the user does not opt-out of its installation during the setup process. In some cases, it can also infiltrate the system through fake updates or misleading pop-up advertisements that trick users into downloading and installing the adware. Once inside, AdminHelper can modify browser settings, track user’s online activities, and cause various performance issues. It is highly recommended to remove this adware to prevent further damage to the system.
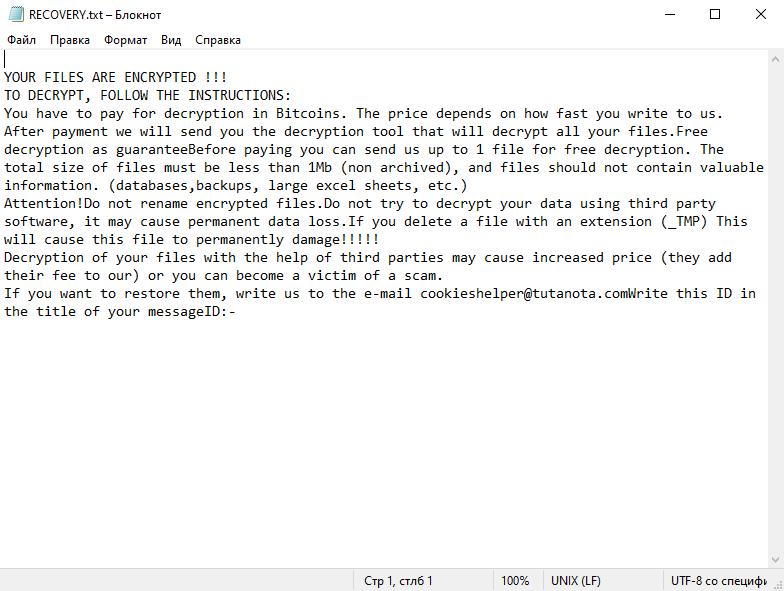
How to remove CookiesHelper Ransomware and decrypt .cookieshelper files
CookiesHelper Ransomware is a type of malicious software designed by cybercriminals to encrypt data on a victim’s computer or network, making it inaccessible until a ransom is paid. Once infiltrated, it encrypts various files and data, rendering them unreadable.
Infection Methods:
Ransomware like CookiesHelper typically infects computers through various methods such as phishing scams, malicious email attachments, fake software updates, or by exploiting vulnerabilities in an operating system, software, or network.
File Extensions:
The specific file extensions added by CookiesHelper ransomware can vary, but usually it’s .cookieshelper. However, most ransomware typically adds unique extensions to the encrypted files, often containing the attacker’s contact information or specific identifiers related to the ransomware.
File Encryption:
The exact encryption algorithm used by CookiesHelper ransomware is not specified in the public domain. However, many types of ransomware use advanced encryption algorithms, like RSA or AES, to encrypt the files.
Ransom Note:
After encrypting the files, ransomware typically creates a ransom note explaining what has happened and how to pay the ransom to get the files back. The specific content and location of this note can vary greatly, and the specifics for CookiesHelper ransomware are not publicly available.
Decryption Tools:
Whether a decryption tool exists for CookiesHelper ransomware is also not specifically known. In many cases, unless a security flaw is found in the ransomware or the cybercriminals are apprehended and the decryption keys are released, no reliable decryption tool would be available.
Decrypt .cookieshelper files:
Decrypting files encrypted by ransomware can be complex and is often not possible without the specific decryption key. If a decryption tool is available, it would typically need to be run on the affected computer. The tool would then attempt to decrypt the files. However, due to the potential for data loss, it is generally recommended to back up the encrypted files before attempting decryption.
It’s important to note that paying the ransom is not recommended because it does not guarantee that the files will be decrypted or that the ransomware will be removed from the computer. Instead, victims should remove the ransomware from their system using a reliable anti-malware program and restore their files from a backup if possible.
How to remove Win32/Floxif
Win32/Floxif is a Trojan horse type of malware that specifically targets computers running on the Windows 32-bit operating system. Its main goal is to infiltrate your system and corrupt your files, which can lead to various detrimental effects such as a decrease in system performance, loss of data, or even total system failure. Win32/Floxif infiltrates computers by hiding itself within another program or file. The user unknowingly installs the malicious program thinking they are installing something legitimate. The Trojan can also be introduced into a system through spam emails, fraudulent downloads, or by visiting infected websites. Once inside the system, Win32/Floxif starts to gather and transmit sensitive user data to a remote server controlled by cybercriminals. This data can include passwords, credit card information, and other personal details. It may also download and install additional malware onto the infected computer, further compromising its security. The Trojan can also modify system settings to make itself run automatically each time the computer is turned on, making its removal challenging.
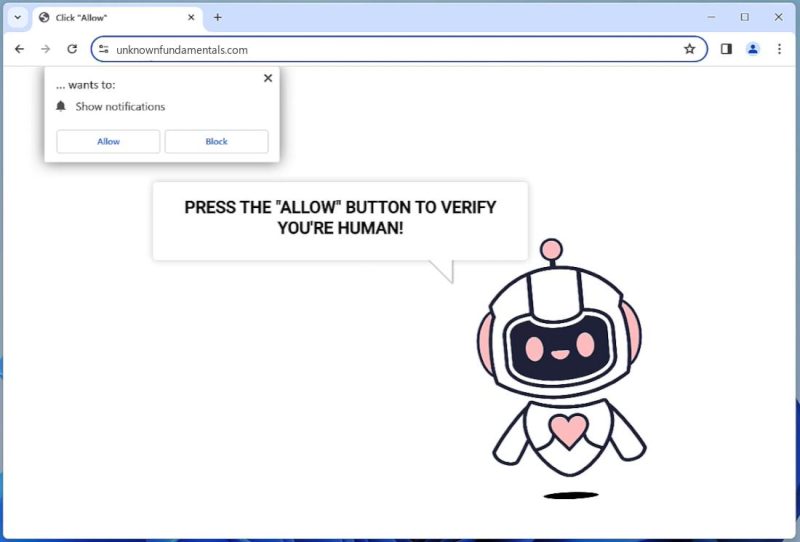
How to remove Unknownfundamentals.com
Unknownfundamentals.com is a malicious website that is notorious for its deceptive techniques to infect computers. This website primarily targets unsuspecting users by luring them with misleading prompts to enable push notifications. Once the user permits these notifications, the website starts sending unwanted ads and pop-ups directly to their desktop or browser. These advertisements can lead to other malicious websites or potentially unwanted programs (PUPs), further exposing the user’s system to various security risks. The site exploits browser notifications by tricking users into allowing them with deceptive prompts or misleading content. Once granted permission, it sends numerous intrusive ads which, when clicked upon, can lead to the download of malware or other harmful software. Unknownfundamentals.com is not specific to any browser or device and can infect a wide range of systems. It can potentially affect popular browsers such as Google Chrome, Mozilla Firefox, Safari, and Internet Explorer on devices running Windows, MacOS, or Android. Users are strongly advised to be cautious about granting permissions to unknown websites and regularly update their security software to protect against such threats.